Validating User Flows to Protect Software Defined Network Environments
Por um escritor misterioso
Last updated 24 janeiro 2025

Software Defined Network is a promising network paradigm which has led to several security threats in SDN applications that involve user flows, switches, and controllers in the network. Threats as spoofing, tampering, information disclosure, Denial of Service, flow table overloading, and so on have been addressed by many researchers. In this paper, we present novel SDN design to solve three security threats: flow table overloading is solved by constructing a star topology-based architecture, unsupervised hashing method mitigates link spoofing attack, and fuzzy classifier combined with L1-ELM running on a neural network for isolating anomaly packets from normal packets. For effective flow migration Discrete-Time Finite-State Markov Chain model is applied. Extensive simulations using OMNeT++ demonstrate the performance of our proposed approach, which is better at preserving holding time than are other state-of-the-art works from the literature.
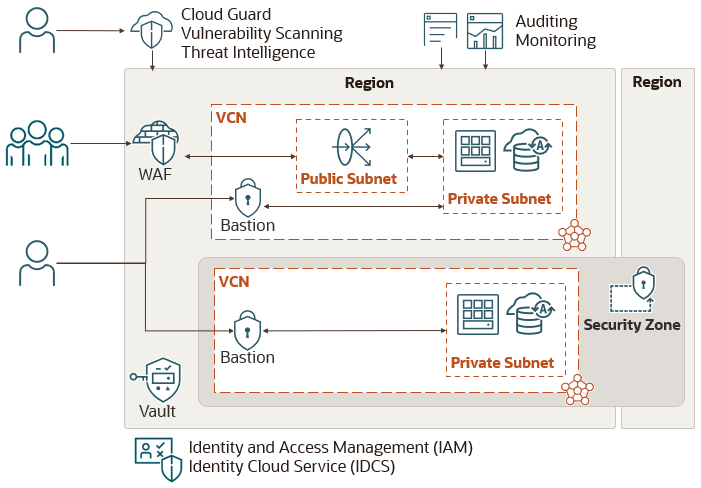
Security Services

PDF) Enhancing Network Security through Software Defined
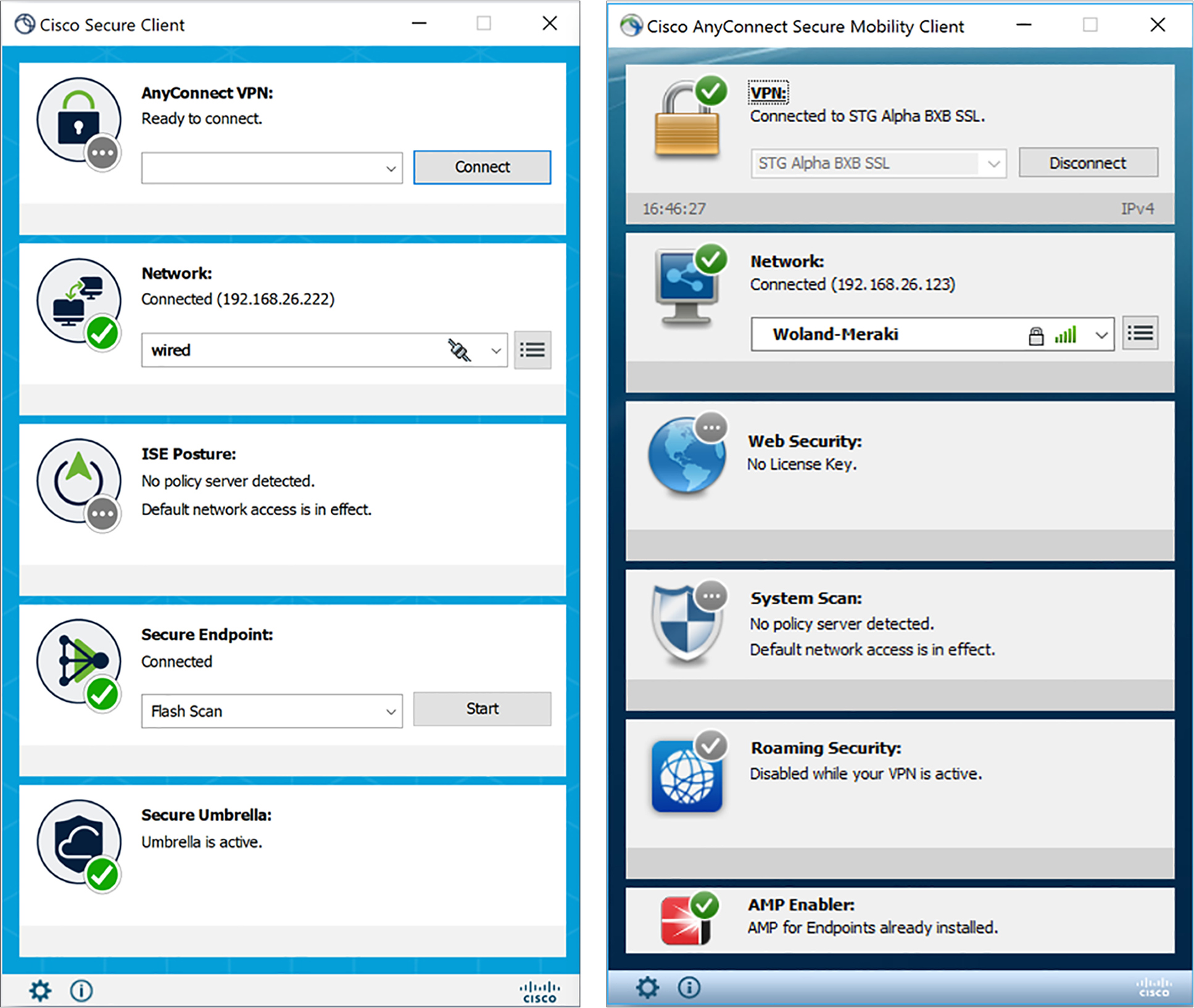
Cisco Secure Client Data Sheet - Cisco

Managing multi-tenant APIs using API Gateway

PERM-GUARD: Authenticating the Validity of Flow Rules in Software
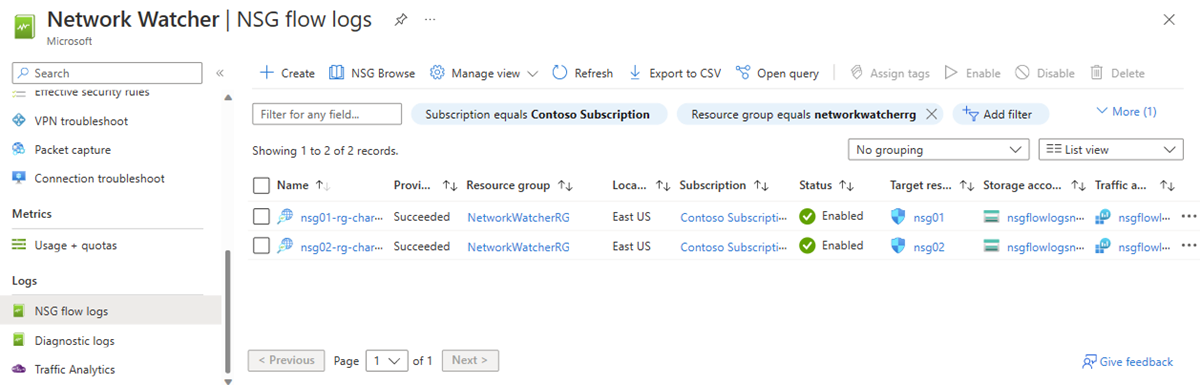
NSG flow logs overview - Azure Network Watcher

What Is Zero Trust Security? How to Implement It & More
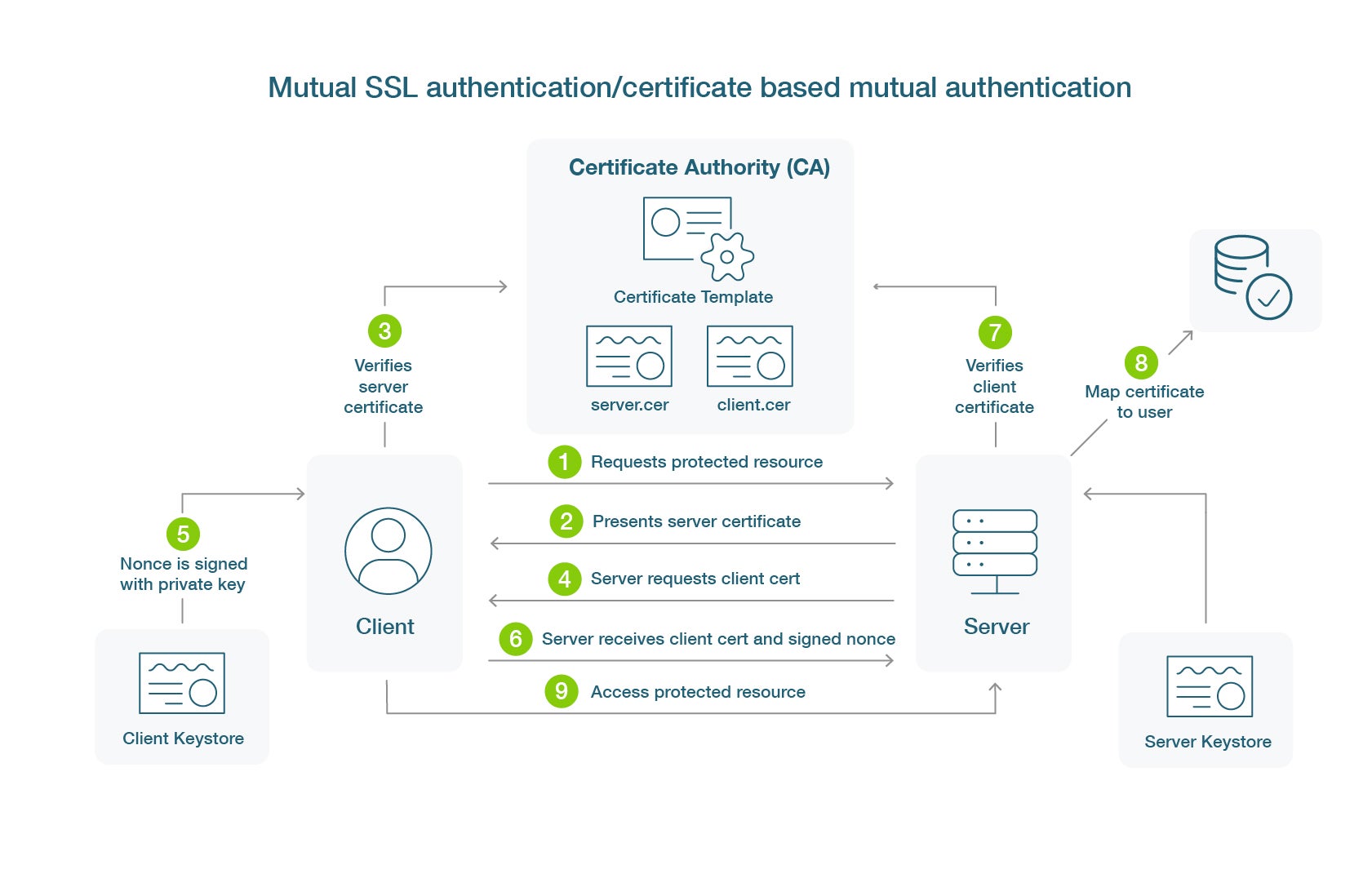
What is Certificate-Based Authentication - Yubico

Validating User Flows to Protect Software Defined Network Environments

Continuous integration: code, deliverables and environments

PDF) Validating User Flows to Protect Software Defined Network
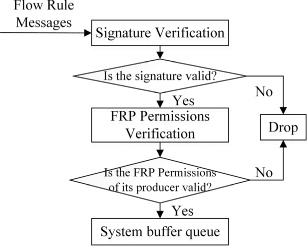
PERM-GUARD: Authenticating the Validity of Flow Rules in Software

Validating User Flows to Protect Software Defined Network Environments

PDF) Validating User Flows to Protect Software Defined Network

Innovax Technologies, LLC - Software Defined Perimeter (SDP) for
Recomendado para você
-
 Faecal impaction with overflow24 janeiro 2025
Faecal impaction with overflow24 janeiro 2025 -
5 POO Overloading, PDF, Subroutine24 janeiro 2025
-
 Overloading vs. Overriding – Hermes's Blog24 janeiro 2025
Overloading vs. Overriding – Hermes's Blog24 janeiro 2025 -
![Tutoriel Java - Poo (Surcharge De Méthode) [Overloading Method]](https://i.ytimg.com/vi/1K18xoxJ5a4/maxresdefault.jpg) Tutoriel Java - Poo (Surcharge De Méthode) [Overloading Method]24 janeiro 2025
Tutoriel Java - Poo (Surcharge De Méthode) [Overloading Method]24 janeiro 2025 -
 POO: Principal conceito de Polimorfismo24 janeiro 2025
POO: Principal conceito de Polimorfismo24 janeiro 2025 -
 Humor Shit Poop Emoji Funny Kawaii Character Stock Vector by ©shawlin 27140649424 janeiro 2025
Humor Shit Poop Emoji Funny Kawaii Character Stock Vector by ©shawlin 27140649424 janeiro 2025 -
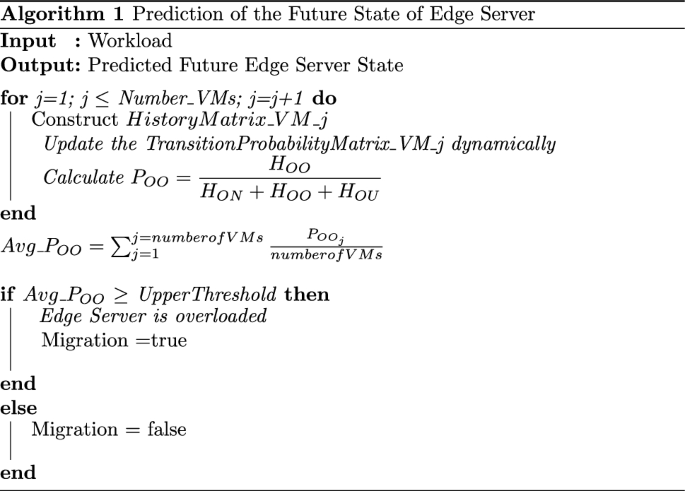 Novel Approaches for Resource Management Across Edge Servers International Journal of Networked and Distributed Computing24 janeiro 2025
Novel Approaches for Resource Management Across Edge Servers International Journal of Networked and Distributed Computing24 janeiro 2025 -
 Bedtime Story Poo Poo's Incredible Adventure24 janeiro 2025
Bedtime Story Poo Poo's Incredible Adventure24 janeiro 2025 -
 Soiling - ERIC24 janeiro 2025
Soiling - ERIC24 janeiro 2025 -
 Cooling cabinet Williams. - PS Auction - We value the future - Largest in net auctions24 janeiro 2025
Cooling cabinet Williams. - PS Auction - We value the future - Largest in net auctions24 janeiro 2025
você pode gostar
-
 Cadeira Barbeiro Cabeleireiro Ajuste Altura E Amortecedor24 janeiro 2025
Cadeira Barbeiro Cabeleireiro Ajuste Altura E Amortecedor24 janeiro 2025 -
 The purple gummy bear - Plant-Ex24 janeiro 2025
The purple gummy bear - Plant-Ex24 janeiro 2025 -
![Roblox Digital Gift Code for 22,500 Robux [Redeem Worldwide - Includes Exclusive Virtual Item] [Online Game Code] : Everything Else](https://m.media-amazon.com/images/I/A1UPw70x09L._SY350_PKmb-play-button-overlay_.png) Roblox Digital Gift Code for 22,500 Robux [Redeem Worldwide - Includes Exclusive Virtual Item] [Online Game Code] : Everything Else24 janeiro 2025
Roblox Digital Gift Code for 22,500 Robux [Redeem Worldwide - Includes Exclusive Virtual Item] [Online Game Code] : Everything Else24 janeiro 2025 -
 New trending GIF tagged spongebob squarepants friendship patrick…24 janeiro 2025
New trending GIF tagged spongebob squarepants friendship patrick…24 janeiro 2025 -
 The Neighbourhood music, videos, stats, and photos24 janeiro 2025
The Neighbourhood music, videos, stats, and photos24 janeiro 2025 -
 Play LENDARIO RUBI by DJ NEM DE ICOARACI feat. DJ NEM O ORIGINAL24 janeiro 2025
Play LENDARIO RUBI by DJ NEM DE ICOARACI feat. DJ NEM O ORIGINAL24 janeiro 2025 -
 OS PODERES DE CADA HOKAGE EM NARUTO E BORUTO!24 janeiro 2025
OS PODERES DE CADA HOKAGE EM NARUTO E BORUTO!24 janeiro 2025 -
 Ip grabber - Imgflip24 janeiro 2025
Ip grabber - Imgflip24 janeiro 2025 -
 Download and use Anime Center on PC & Mac (Emulator)24 janeiro 2025
Download and use Anime Center on PC & Mac (Emulator)24 janeiro 2025 -
 Tell Me Why - SteamGridDB24 janeiro 2025
Tell Me Why - SteamGridDB24 janeiro 2025
