Major surge in memory-based attacks as hackers evade traditional
Por um escritor misterioso
Last updated 26 janeiro 2025

Protecting workloads with tools that understand how to interpret attacks on cloud runtime environments is crucial.
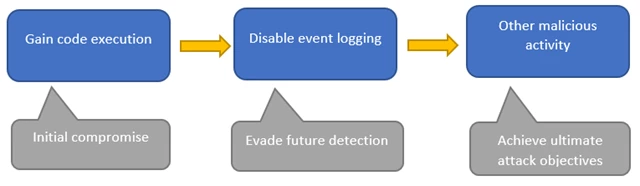
Detecting in-memory attacks with Sysmon and Azure Security Center

Antivirus & Malware Evasion Techniques
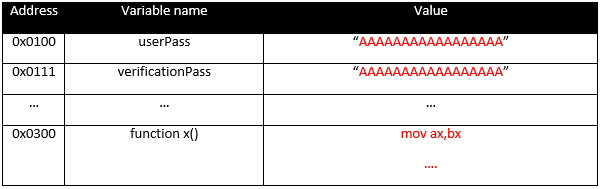
Inside the Mind of a Hacker: Attacking the Memory

Metador APT hackers target telecommunications, ISPs, universities

What is a fileless attack? How hackers invade systems without

Denial-of-service attack - Wikipedia

CrowdStrike Uses Similarity Search to Detect Script-Based Malware
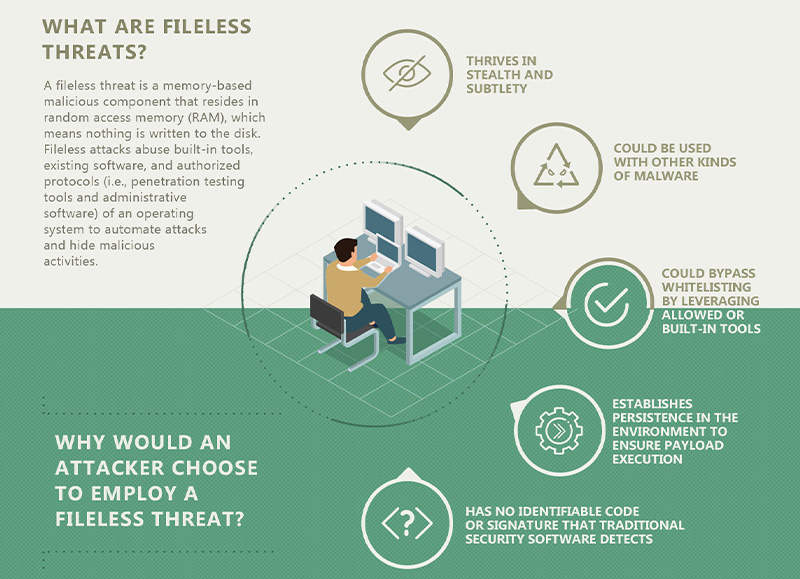
Security 101: How Fileless Attacks Work and Persist in Systems

Five Reasons Memory-Based Cyberattacks Continue to Succeed

What is a Fileless Malware Attack (with examples)
Recomendado para você
-
 BlueNoroff How DPRK's macOS RustBucket Seeks to Evade Analysis26 janeiro 2025
BlueNoroff How DPRK's macOS RustBucket Seeks to Evade Analysis26 janeiro 2025 -
 Evade Script/GUI Review26 janeiro 2025
Evade Script/GUI Review26 janeiro 2025 -
![OP Evade Script GUI [FREE]](https://vapouryt.co.uk/wp-content/uploads/2022/09/evade-script.jpg) OP Evade Script GUI [FREE]26 janeiro 2025
OP Evade Script GUI [FREE]26 janeiro 2025 -
![Selling] 🔥the best external lol script🔥, ✓undetected](https://i.imgur.com/2mBXxFQ.jpg) Selling] 🔥the best external lol script🔥, ✓undetected26 janeiro 2025
Selling] 🔥the best external lol script🔥, ✓undetected26 janeiro 2025 -
![🔥NOVO] Evade Script ROBLOX!! (Funcionando 2022)](https://i.ytimg.com/vi/m_qS5tSnnts/maxresdefault.jpg) 🔥NOVO] Evade Script ROBLOX!! (Funcionando 2022)26 janeiro 2025
🔥NOVO] Evade Script ROBLOX!! (Funcionando 2022)26 janeiro 2025 -
 ⭐League of Legends⭐, SELLY, Scripts/Evade/Tracker26 janeiro 2025
⭐League of Legends⭐, SELLY, Scripts/Evade/Tracker26 janeiro 2025 -
 Hack Like a Pro: How to Evade AV Detection with Veil-Evasion26 janeiro 2025
Hack Like a Pro: How to Evade AV Detection with Veil-Evasion26 janeiro 2025 -
 Evade Script Roblox: Auto Farm, Auto Respawn & More26 janeiro 2025
Evade Script Roblox: Auto Farm, Auto Respawn & More26 janeiro 2025 -
 Disassemble Script26 janeiro 2025
Disassemble Script26 janeiro 2025 -
 New Magecart group uses an e-Skimmer that avoids VMs and sandboxes26 janeiro 2025
New Magecart group uses an e-Skimmer that avoids VMs and sandboxes26 janeiro 2025
você pode gostar
-
 Couple Digi Stamp Digital Stamp Romantic Drawing Man Woman Husband Wife Boyfriend Girlfriend Hand Drawn Line Illustration Images Graphics26 janeiro 2025
Couple Digi Stamp Digital Stamp Romantic Drawing Man Woman Husband Wife Boyfriend Girlfriend Hand Drawn Line Illustration Images Graphics26 janeiro 2025 -
 União Sinistra26 janeiro 2025
União Sinistra26 janeiro 2025 -
 Five Amazing Gaming Moments From the Speed Run Event AGDQ - GameSpot26 janeiro 2025
Five Amazing Gaming Moments From the Speed Run Event AGDQ - GameSpot26 janeiro 2025 -
While waiting for Lumi and to get a second opinion please type me, by collage and questionnaire, enneagram, mbti and instinctual variant.26 janeiro 2025
-
 New Super Mario Bros 2 CIA QR Code for use with FBI : r/Roms26 janeiro 2025
New Super Mario Bros 2 CIA QR Code for use with FBI : r/Roms26 janeiro 2025 -
 The Last Of Us Part II Ellie Edition - Unboxing & Review - FuryPixel®26 janeiro 2025
The Last Of Us Part II Ellie Edition - Unboxing & Review - FuryPixel®26 janeiro 2025 -
 Fortnite recebe nova lista de personagens do Naruto26 janeiro 2025
Fortnite recebe nova lista de personagens do Naruto26 janeiro 2025 -
 NFS Mobile Banking icon. Element of mobile banking for smart26 janeiro 2025
NFS Mobile Banking icon. Element of mobile banking for smart26 janeiro 2025 -
caro-kann defense by Magnus carlsen #chess #grandmaster26 janeiro 2025
-
 AS LETRAS ganharam vida no Roblox! (ABC Lore)26 janeiro 2025
AS LETRAS ganharam vida no Roblox! (ABC Lore)26 janeiro 2025
