Attackers use dynamic code loading to bypass Google Play store's
Por um escritor misterioso
Last updated 17 abril 2025

Threat actors rely on the 'versioning' technique to evade malware detections of malicious code uploaded to the Google Play Store
Dynamic analysis and tampering

Tool Release: Magisk Module – Conscrypt Trust User Certs

Android and iPhone users get crucial Google Play and Apple App
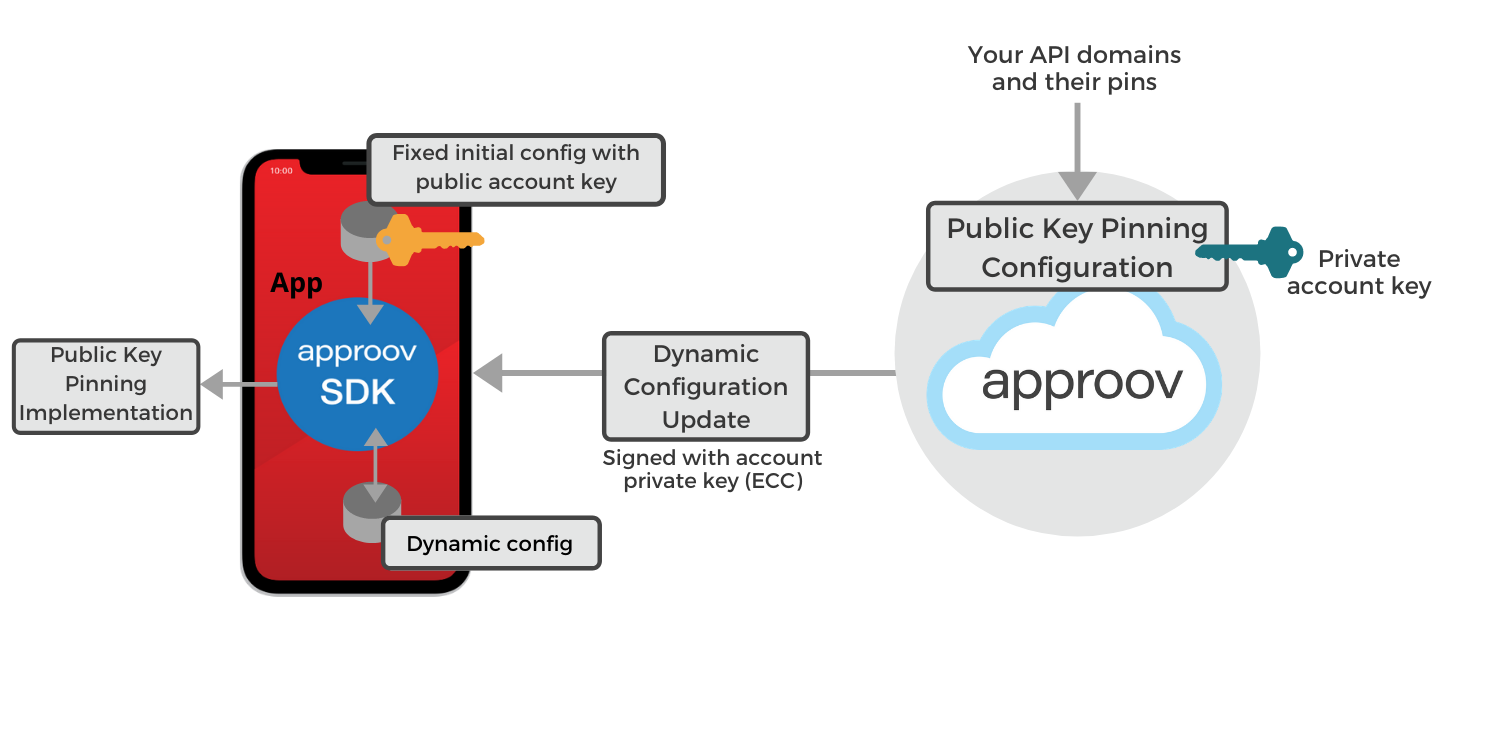
How to Protect Against Certificate Pinning Bypassing

Quash EDR/XDR Exploits With These Countermeasures

How to Code Sign Secured Android App with SHA Fingerprint Google

Testing Infrastructure-as-Code Using Dynamic Tooling

Life cycle of Promon Shield's native library.
%20-%20refresh/img_03.png?width=350&name=img_03.png)
Android App Permissions: Which to Allow and Avoid

Google Play Store, Breaking Cybersecurity News

Android: With Android 14, Google has a new plan to make your
Recomendado para você
-
The 1 Billion Visits Update, Roblox Evade Wiki17 abril 2025
-
 Roblox: Evade Codes17 abril 2025
Roblox: Evade Codes17 abril 2025 -
 Evolution Evade Tower Defense Codes - Roblox - December 202317 abril 2025
Evolution Evade Tower Defense Codes - Roblox - December 202317 abril 2025 -
 All Evade Codes(Roblox) - Tested December 2022 - Player Assist17 abril 2025
All Evade Codes(Roblox) - Tested December 2022 - Player Assist17 abril 2025 -
 CODES – Evade! - Rick News17 abril 2025
CODES – Evade! - Rick News17 abril 2025 -
 All Evade Codes For November 2023 - GameRiv17 abril 2025
All Evade Codes For November 2023 - GameRiv17 abril 2025 -
 Roblox Evolution Evade Promo Codes (July 2023) - Ohana Gamers17 abril 2025
Roblox Evolution Evade Promo Codes (July 2023) - Ohana Gamers17 abril 2025 -
 DragonSpark Attacks Evade Detection with SparkRAT and Golang17 abril 2025
DragonSpark Attacks Evade Detection with SparkRAT and Golang17 abril 2025 -
 Codes d'évasion (novembre 2022) – Guides de jeu professionnels17 abril 2025
Codes d'évasion (novembre 2022) – Guides de jeu professionnels17 abril 2025 -
Instagram photo by Derrick Van Orden • Oct 1, 2023 at 5:51 AM17 abril 2025
você pode gostar
-
 Mortal Kombat Goro Shao Kahn Mileena Liu Kang, Mortal Kombat17 abril 2025
Mortal Kombat Goro Shao Kahn Mileena Liu Kang, Mortal Kombat17 abril 2025 -
 Combee's Path of Solitude – Apple Crossing17 abril 2025
Combee's Path of Solitude – Apple Crossing17 abril 2025 -
 Disney Speedstorm: jogo rival de Mario Kart é lançado; veja preço17 abril 2025
Disney Speedstorm: jogo rival de Mario Kart é lançado; veja preço17 abril 2025 -
 D&D 5e: Wizard Class Guide - Sage Gamers17 abril 2025
D&D 5e: Wizard Class Guide - Sage Gamers17 abril 2025 -
Free Robux Generator 100% Working-568817 abril 2025
-
Wingmen17 abril 2025
-
 Twice lightstick cover: Crochet pattern17 abril 2025
Twice lightstick cover: Crochet pattern17 abril 2025 -
 sonic tennis by sonictopfan on DeviantArt17 abril 2025
sonic tennis by sonictopfan on DeviantArt17 abril 2025 -
 Calmed by the Dark Shin Neon on Steam17 abril 2025
Calmed by the Dark Shin Neon on Steam17 abril 2025 -
 THE KING OF FIGHTERS '98, iOS/Android17 abril 2025
THE KING OF FIGHTERS '98, iOS/Android17 abril 2025


