Cryptojacking - Cryptomining in the browser — ENISA
Por um escritor misterioso
Last updated 15 abril 2025

The technique of hijacking browsers for mining cryptocurrency (without user consent) is called

PDF) Detecting Cryptojacking Web Threats: An Approach with

The concept of cryptojacking and how it works?

Rundown of the Top 15 Cybersecurity Threats of 2019-2020 — Long Law
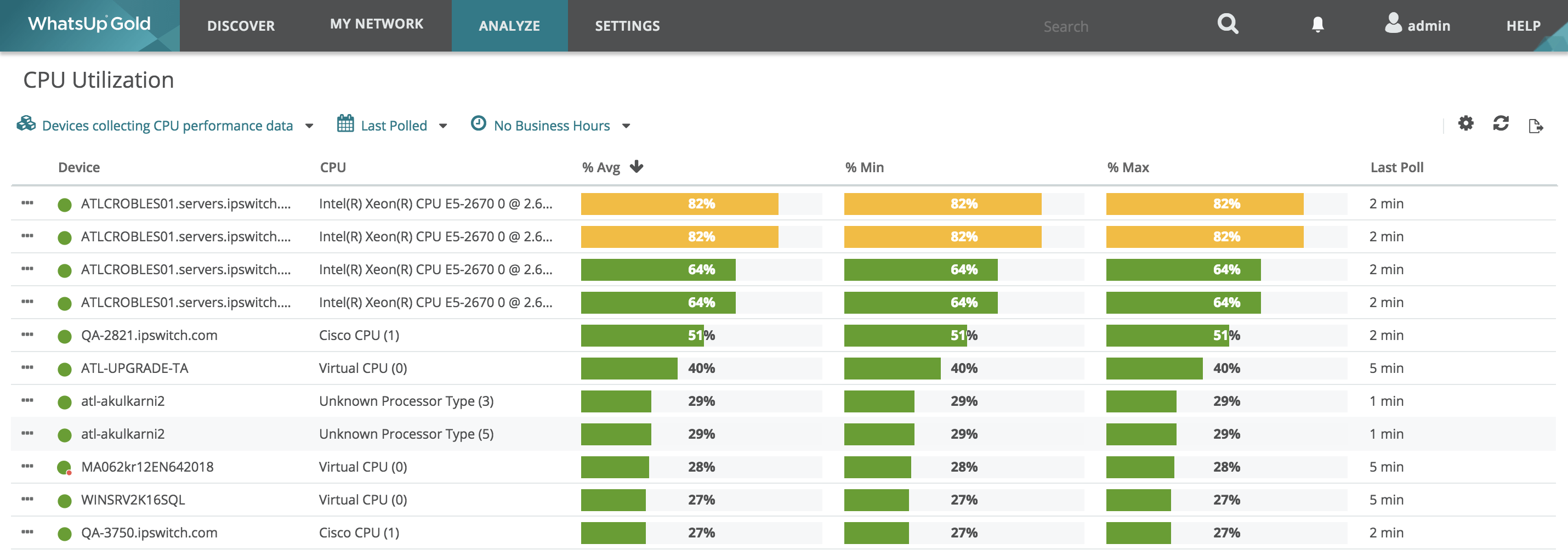
How to Detect and Stop Cryptomining on Your Network
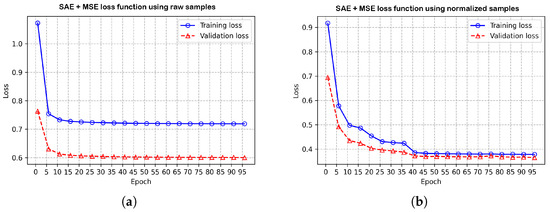
Applied Sciences, Free Full-Text

Awareness Articles – TPS ASAG – Application Security Awareness Group
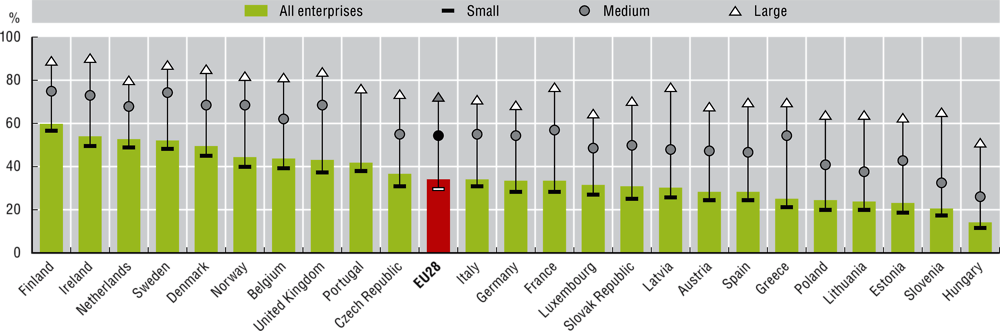
Chapter 7. Digital security OECD Digital Economy Outlook 2020

PacNOG 23: Introduction to Crypto Jacking

What is Cryptojacking. Criminals are now using ransomware-like
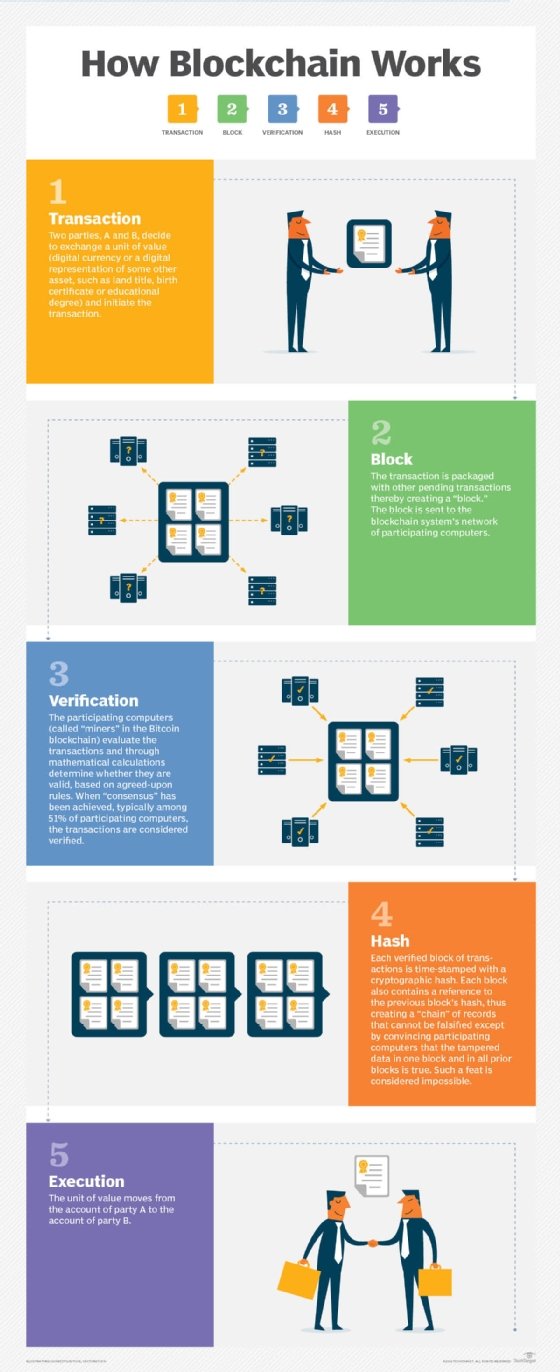
What is Cryptojacking? Detection and Preventions Techniques

Hundreds of new cyber security simulations to keep you safe from

What You Must Know About Cryptojacking in 2022

ENISA Threat Landscape 2020 - Cryptojacking — ENISA

The Anomali Blog

PacNOG 23: Introduction to Crypto Jacking
Recomendado para você
-
minerBlock15 abril 2025
-
GitHub - unkn0wn404/MinerBlocker: Chrome extension Miner Blocker designed to stop coin miners scripts and block cryptojackers from using your CPU for mining15 abril 2025
-
 13 Best Ad Blocker for Chrome in 2023 (Free & Paid) - EarthWeb15 abril 2025
13 Best Ad Blocker for Chrome in 2023 (Free & Paid) - EarthWeb15 abril 2025 -
 Task Mining Desktop Application browser extensions (optional)15 abril 2025
Task Mining Desktop Application browser extensions (optional)15 abril 2025 -
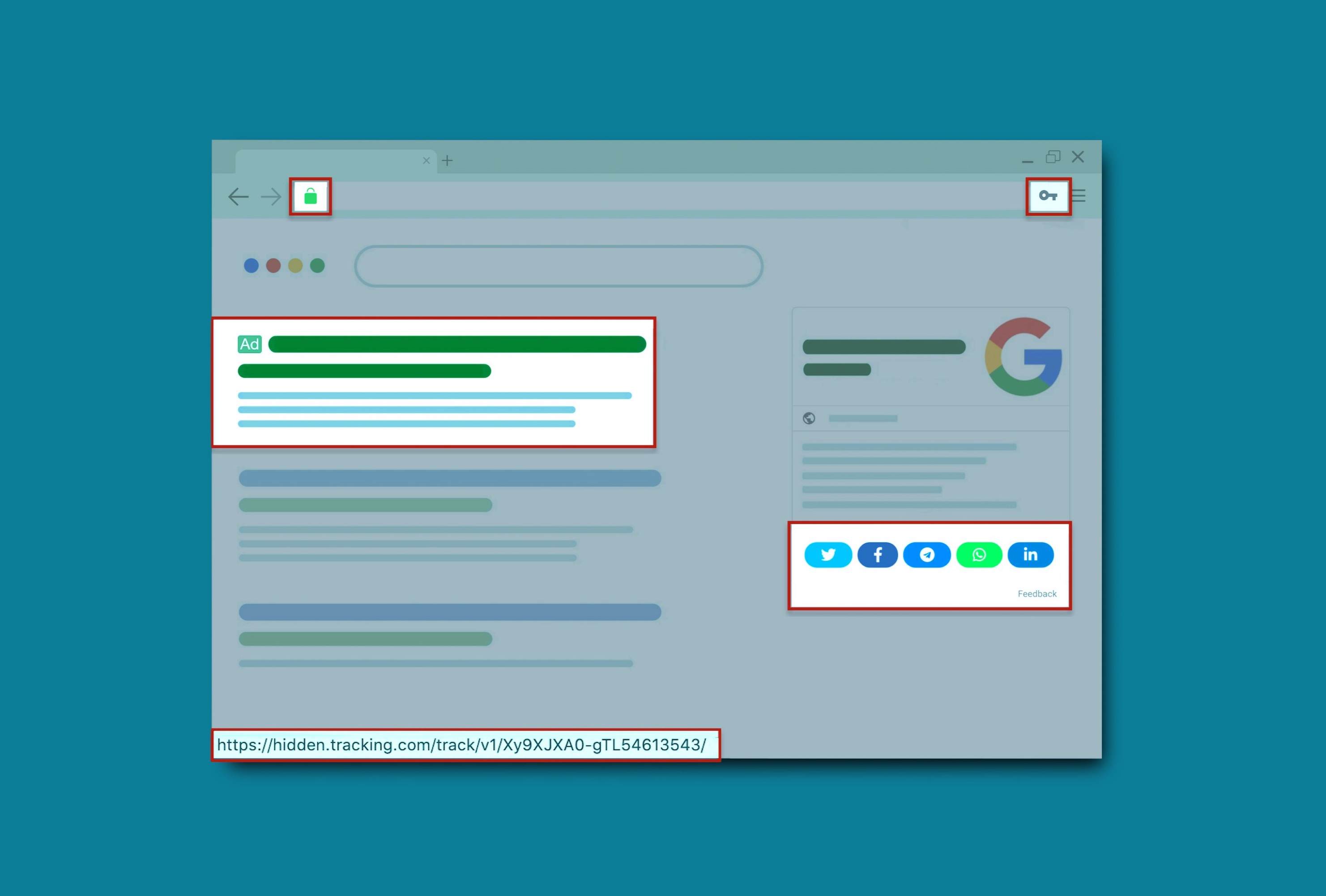 These 6 browser extensions will protect your privacy online15 abril 2025
These 6 browser extensions will protect your privacy online15 abril 2025 -
 Top 10 Crypto Browser Extensions For 2023 - ETH, BTC15 abril 2025
Top 10 Crypto Browser Extensions For 2023 - ETH, BTC15 abril 2025 -
 21 Must-Have SEO Chrome Extensions to Follow in 202315 abril 2025
21 Must-Have SEO Chrome Extensions to Follow in 202315 abril 2025 -
 Cryptojacking Extensions Found on Google Chrome Web Store15 abril 2025
Cryptojacking Extensions Found on Google Chrome Web Store15 abril 2025 -
 LinkedIn Chrome Extension: Top 7 You MUST Try15 abril 2025
LinkedIn Chrome Extension: Top 7 You MUST Try15 abril 2025 -
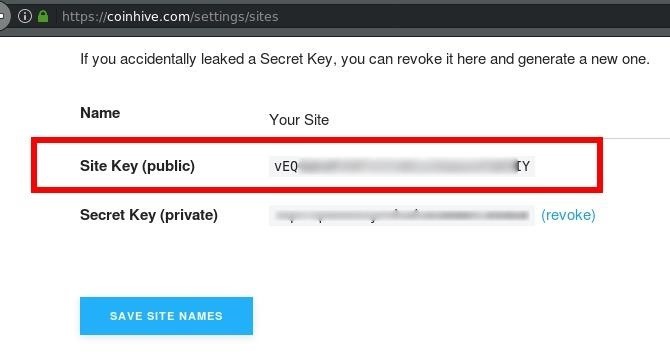 How to Inject Coinhive Miners into Public Wi-Fi Hotspots « Null15 abril 2025
How to Inject Coinhive Miners into Public Wi-Fi Hotspots « Null15 abril 2025
você pode gostar
-
 Call of Duty: Modern Warfare 3 makes $1 billion--in 16 days - CNET15 abril 2025
Call of Duty: Modern Warfare 3 makes $1 billion--in 16 days - CNET15 abril 2025 -
 PETS EMPIRE Dog Cat Pet Powder Rose Fragrance Companion Care Net15 abril 2025
PETS EMPIRE Dog Cat Pet Powder Rose Fragrance Companion Care Net15 abril 2025 -
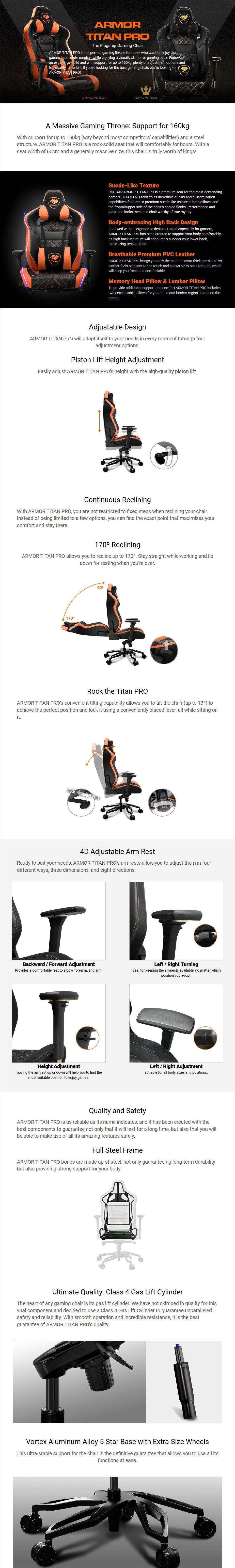 Cadeira Gamer Cougar Gaming Armor Titan Pro Royal Preto - 3MTITANR.000115 abril 2025
Cadeira Gamer Cougar Gaming Armor Titan Pro Royal Preto - 3MTITANR.000115 abril 2025 -
:no_upscale()/cdn.vox-cdn.com/uploads/chorus_asset/file/21922908/11.jpg) Win probability vs fan experience: Buffalo Bills v Los Angeles Rams - Buffalo Rumblings15 abril 2025
Win probability vs fan experience: Buffalo Bills v Los Angeles Rams - Buffalo Rumblings15 abril 2025 -
 Git Gud Hornet15 abril 2025
Git Gud Hornet15 abril 2025 -
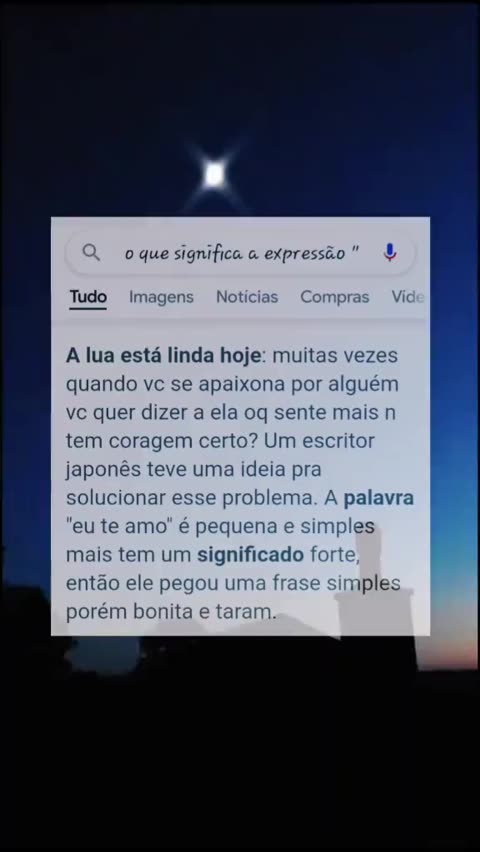 qual o significado da frase a lua está linda hoje15 abril 2025
qual o significado da frase a lua está linda hoje15 abril 2025 -
Creepypasta Brasil: Lendas e Terror - NOVA SÉRIE DE TERROR NA15 abril 2025
-
 Como ganhar nas apostas de futebol: guia completo - FutDados15 abril 2025
Como ganhar nas apostas de futebol: guia completo - FutDados15 abril 2025 -
 Spider life cycle song15 abril 2025
Spider life cycle song15 abril 2025 -
 Personagens de Street Fighter foram figurantes de anime nos anos 90 e você nem percebeu15 abril 2025
Personagens de Street Fighter foram figurantes de anime nos anos 90 e você nem percebeu15 abril 2025
