The SpiKey attack: How to copy keys using sound
Por um escritor misterioso
Last updated 26 janeiro 2025

The SpiKey attack: How one can copy a key using a phone recording of the sound of the clicks the key makes during insertion into a lock.

Segmentation, trace denoising and spike extraction framework. (A) Mask

Vengeance Sound
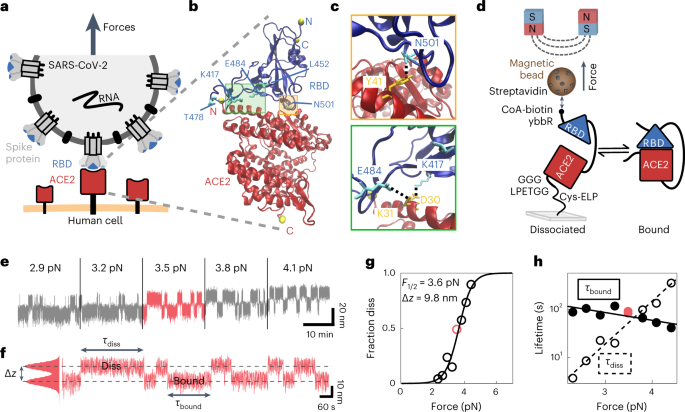
Single-molecule force stability of the SARS-CoV-2–ACE2 interface in variants-of-concern

SpiKey: Beware of the Sound of Your Key
What are transients? How to deal with it in the mixing proces?

Spectrasonics - Omnisphere 2.8 - Library

Spike Lee on Tom Pollock: “The Unsung Hero” of 'Do the Right Thing' – The Hollywood Reporter

Ransomware, extortion and the cyber crime ecosystem
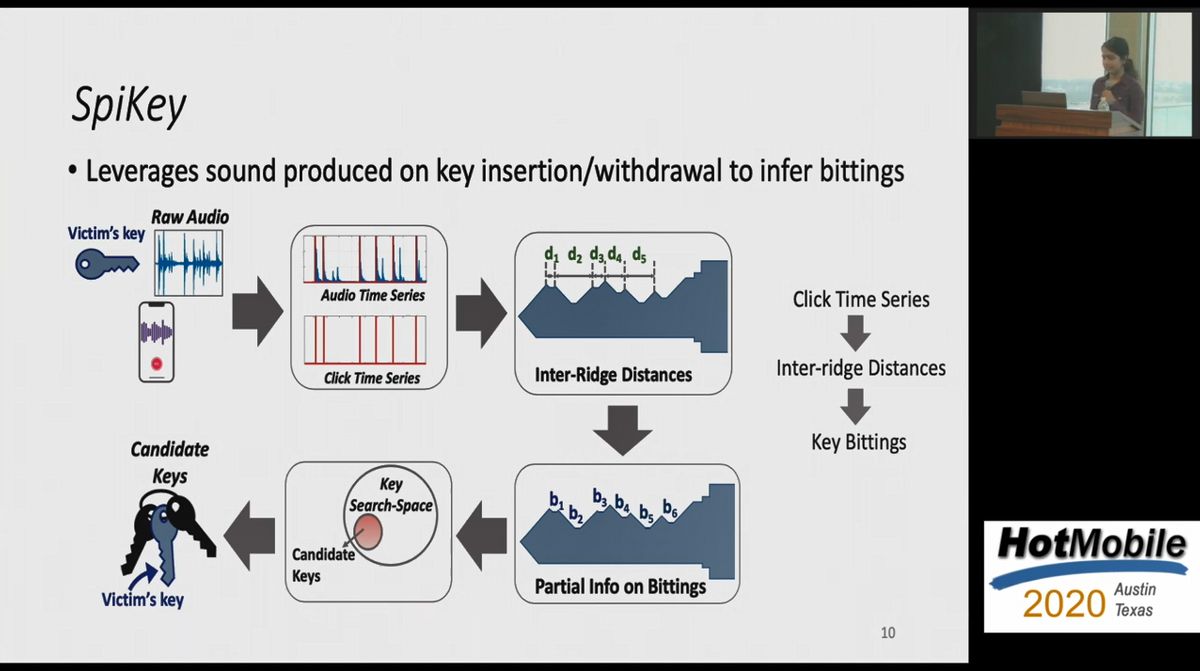
Researchers warn that there is a danger that a duplicate key will be made from 'sound when inserting a key into a keyhole' - GIGAZINE

Spike - Super Mario Wiki, the Mario encyclopedia

Basic Volleyball Rules and Terms - The Art of Coaching Volleyball

Negative SEO: How to Prevent 6 Types of Attacks & Stay Safe

The sound your keystrokes make is enough for AI to steal them — how to stay safe
Recomendado para você
-
 Kwikset 10119 4 CUT KEYS SmartKey Kit26 janeiro 2025
Kwikset 10119 4 CUT KEYS SmartKey Kit26 janeiro 2025 -
 Key Precut Y (2 Lever)26 janeiro 2025
Key Precut Y (2 Lever)26 janeiro 2025 -
 What to Do When You Lose Your Key26 janeiro 2025
What to Do When You Lose Your Key26 janeiro 2025 -
 How to Recycle Keys or Put Them to Good Use26 janeiro 2025
How to Recycle Keys or Put Them to Good Use26 janeiro 2025 -
 Types of keys - All Locks26 janeiro 2025
Types of keys - All Locks26 janeiro 2025 -
 Get key copies that work at McGuire Lock26 janeiro 2025
Get key copies that work at McGuire Lock26 janeiro 2025 -
 Why Can't I Get My Key Copied? - Alpha Locksmith26 janeiro 2025
Why Can't I Get My Key Copied? - Alpha Locksmith26 janeiro 2025 -
 Lost without you - 11 sets of car keys located - Far North26 janeiro 2025
Lost without you - 11 sets of car keys located - Far North26 janeiro 2025 -
 Tiffany Keys Heart Key in Silver, Mini26 janeiro 2025
Tiffany Keys Heart Key in Silver, Mini26 janeiro 2025 -
 8 x Royal Skeleton Key Antique Old look Vintage Key AU SELLER26 janeiro 2025
8 x Royal Skeleton Key Antique Old look Vintage Key AU SELLER26 janeiro 2025
você pode gostar
-
PSP Sony Caixas dos jogos com livros e selo Igac Matosinhos E Leça26 janeiro 2025
-
 Calaméo - The popular PC games story site26 janeiro 2025
Calaméo - The popular PC games story site26 janeiro 2025 -
 O morcego Draluc” 🦇 🇧🇷 Kyuuketsuki Sugu Shinu (DUBLADO PT/BR)26 janeiro 2025
O morcego Draluc” 🦇 🇧🇷 Kyuuketsuki Sugu Shinu (DUBLADO PT/BR)26 janeiro 2025 -
 Home - Nerdizmo Adventure time art, Adventure time, Adventure time anime26 janeiro 2025
Home - Nerdizmo Adventure time art, Adventure time, Adventure time anime26 janeiro 2025 -
 Desire The Asenheim Project (18+)26 janeiro 2025
Desire The Asenheim Project (18+)26 janeiro 2025 -
 Narmada River sand Balu Reti in Indore at best price by Agrawal Traders - Justdial26 janeiro 2025
Narmada River sand Balu Reti in Indore at best price by Agrawal Traders - Justdial26 janeiro 2025 -
 HD Paper Hole Burst Rip PNG Paper, Original image, Transparent26 janeiro 2025
HD Paper Hole Burst Rip PNG Paper, Original image, Transparent26 janeiro 2025 -
 Ghost of Tsushima release date has finally been revealed - here's26 janeiro 2025
Ghost of Tsushima release date has finally been revealed - here's26 janeiro 2025 -
 Fortune Mouse oferece prêmios em dinheiro em jogo de slot divertido, VARIEDADES26 janeiro 2025
Fortune Mouse oferece prêmios em dinheiro em jogo de slot divertido, VARIEDADES26 janeiro 2025 -
 Rosto do boneco do roblox26 janeiro 2025
Rosto do boneco do roblox26 janeiro 2025