Vulnerability Scanning in your CI/CD Pipeline - Part Two
Por um escritor misterioso
Last updated 13 janeiro 2025


Adding Image Security Scanning to a CI/CD pipeline, by Larbi Youcef Mohamed Reda, alter way

Vulnerability Scanning in your CI/CD Pipeline - Part Two
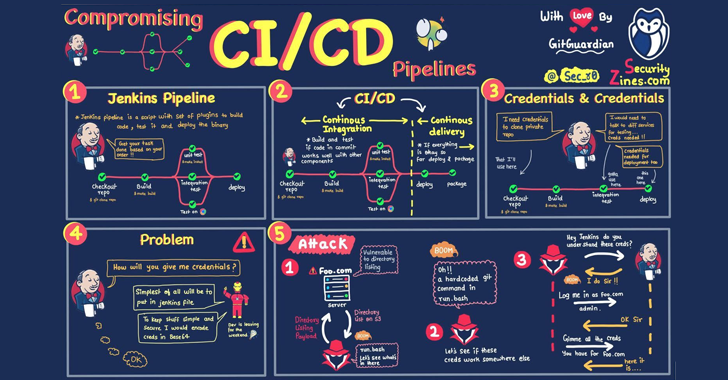
CI/CD Risks: Protecting Your Software Development Pipelines
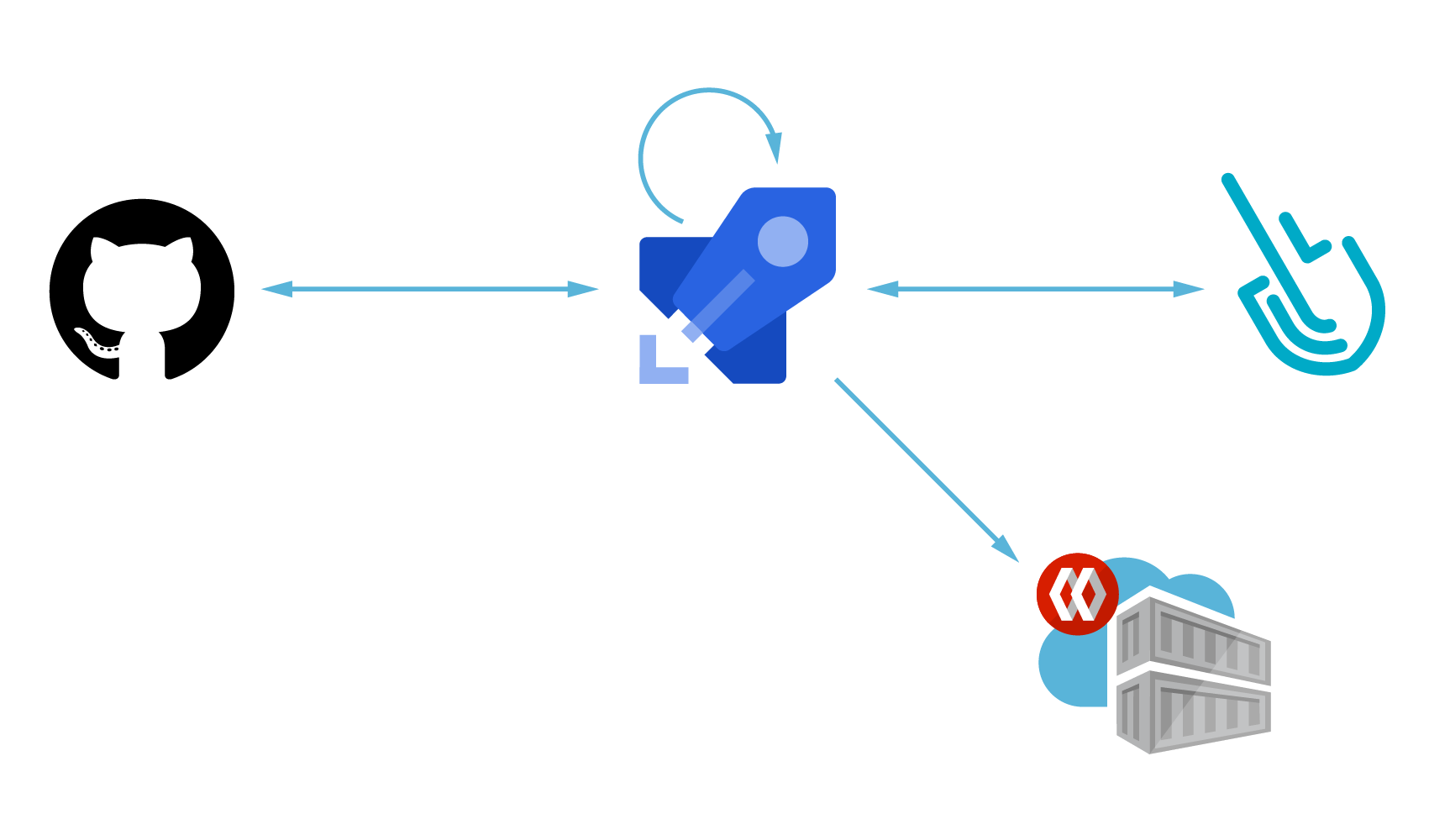
Container Image Scanning for Azure Pipelines with Sysdig – Sysdig

CI/CD Vulnerability Scanning - How to begin your DevSecOps journey
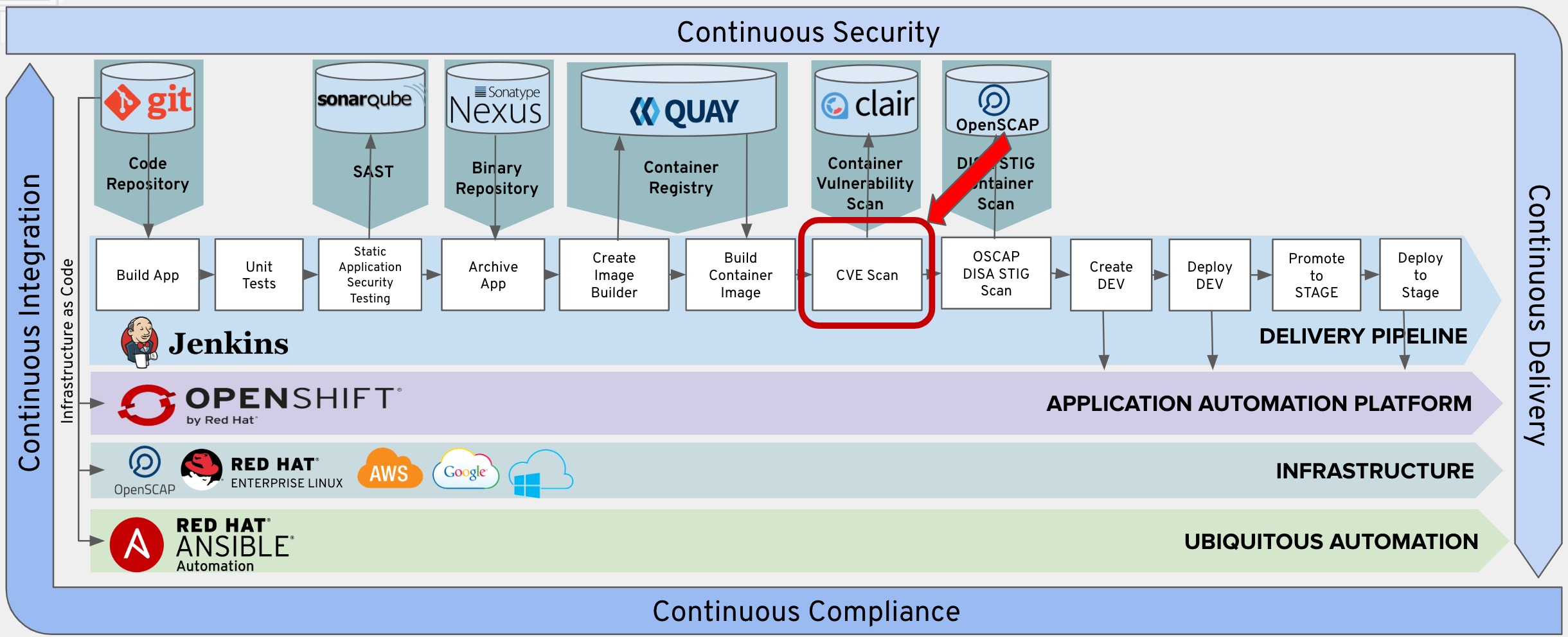
Lab 17 - Clair Vulnerability Scan, Red Hat
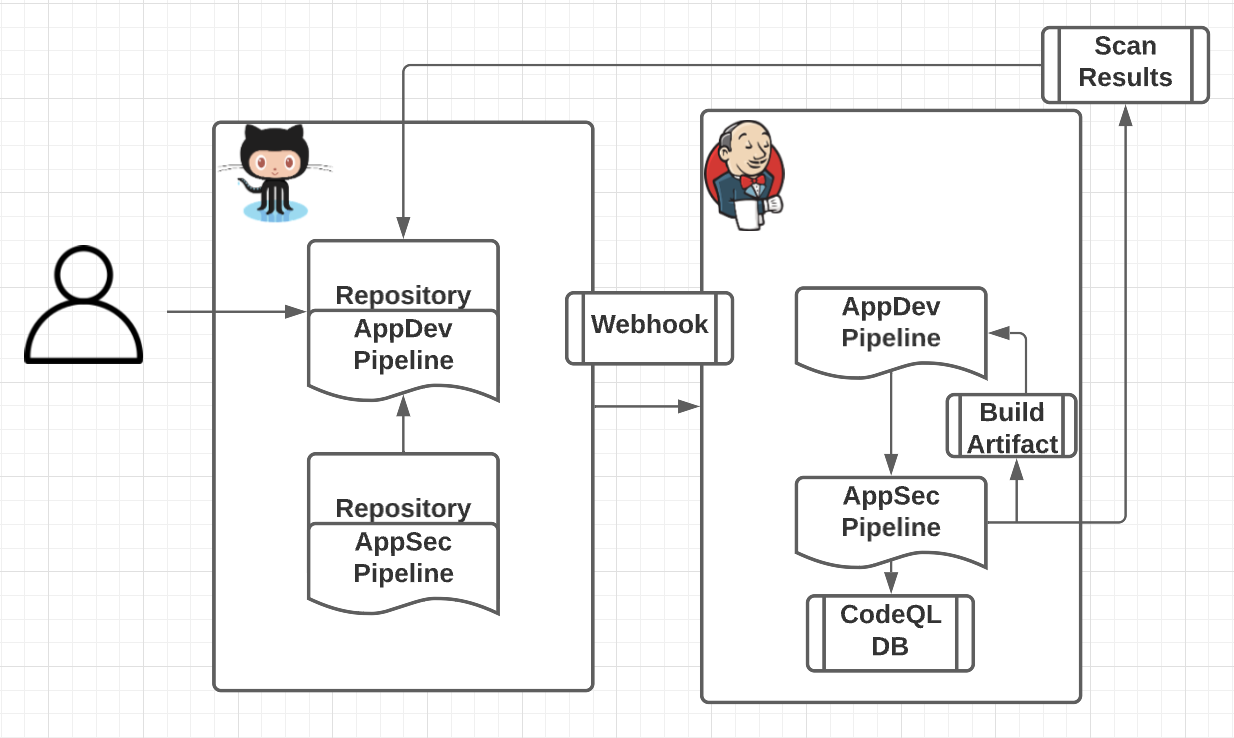
Best practices on rolling out code scanning at enterprise scale - The GitHub Blog
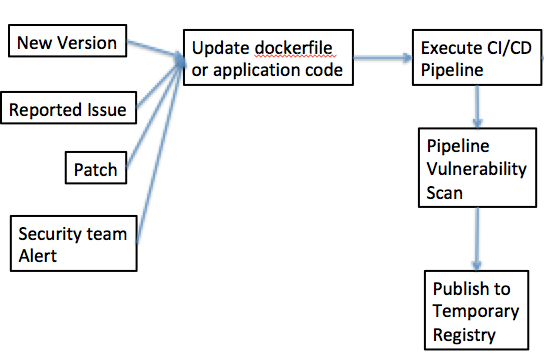
Pipeline Vulnerability Scanner - Cloud Adoption Patterns
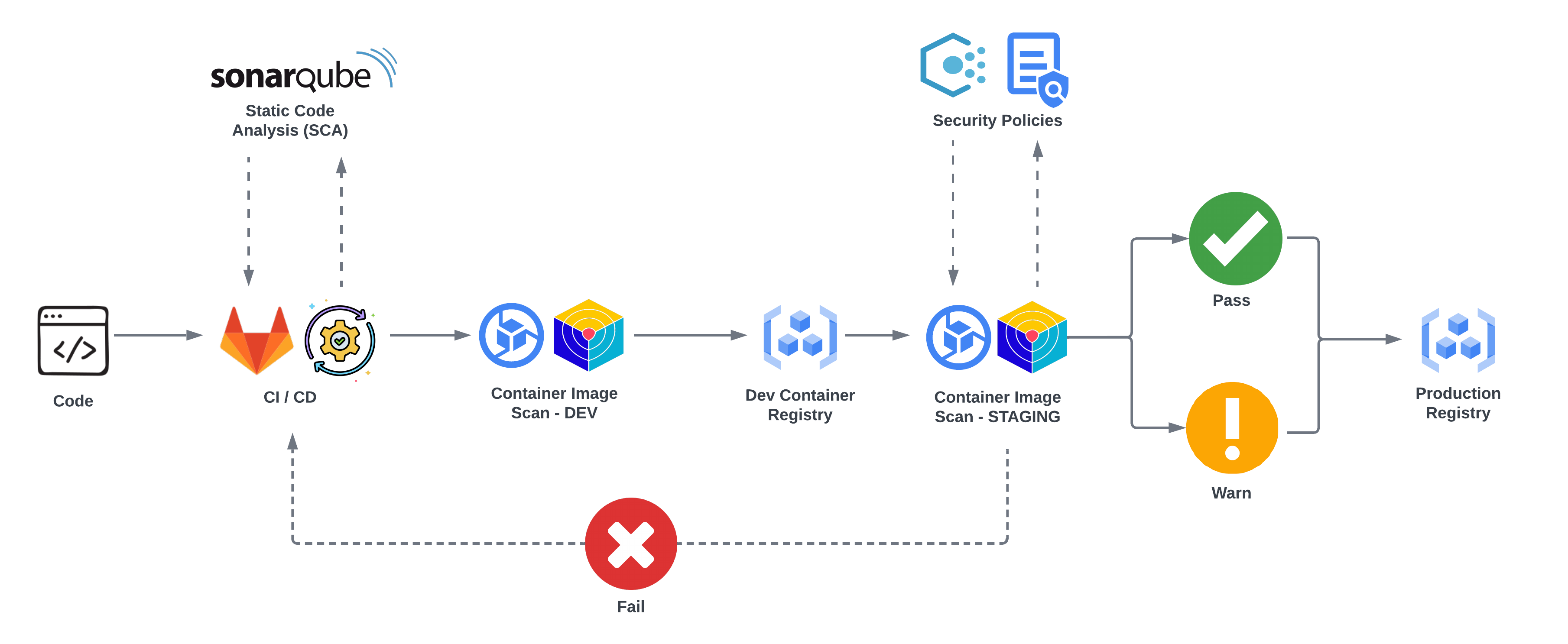
Adroit Cloud Consulting
Continuous Security Testing: Integrating Security into CI/CD Pipeline

CI/CD Security: What is it and How to Protect Your Pipelines

How to build a CI/CD pipeline for container vulnerability scanning with Trivy and AWS Security Hub
Recomendado para você
-
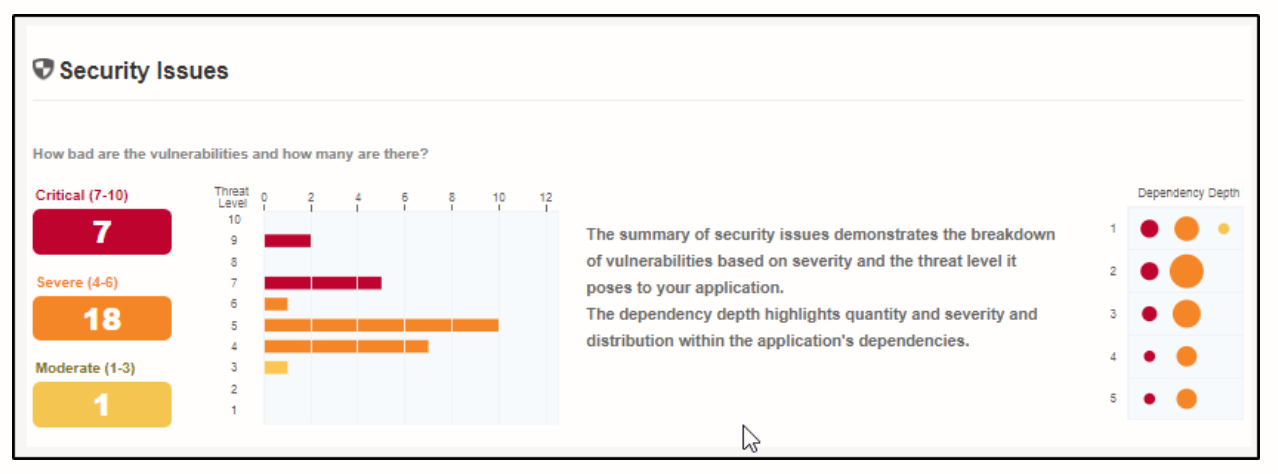 Getting Started with Sonatype Vulnerability Analysis13 janeiro 2025
Getting Started with Sonatype Vulnerability Analysis13 janeiro 2025 -
 Tools of the trade: Scan Gauge kits - Bite Magazine13 janeiro 2025
Tools of the trade: Scan Gauge kits - Bite Magazine13 janeiro 2025 -
Nexus iOS13 janeiro 2025
-
 NEXUS iOS Generation 2.0 Scan Gauges Walk-Thru with Michael Tuckman13 janeiro 2025
NEXUS iOS Generation 2.0 Scan Gauges Walk-Thru with Michael Tuckman13 janeiro 2025 -
Nexus iOS - Looking to get started with Nexus iOS? Order one of our Scan Demo Kits and utilise the power of your Intraoral scanner, seeing how easy it is to upgrade13 janeiro 2025
-
 NEXUS score vs CT scan findings.13 janeiro 2025
NEXUS score vs CT scan findings.13 janeiro 2025 -
Nexus iOS - Nexus iOS Scan Gauges provide the most13 janeiro 2025
-
 Nexus Vulnerability Scanner: Getting Started with Vulnerability Analysis - DEV Community13 janeiro 2025
Nexus Vulnerability Scanner: Getting Started with Vulnerability Analysis - DEV Community13 janeiro 2025 -
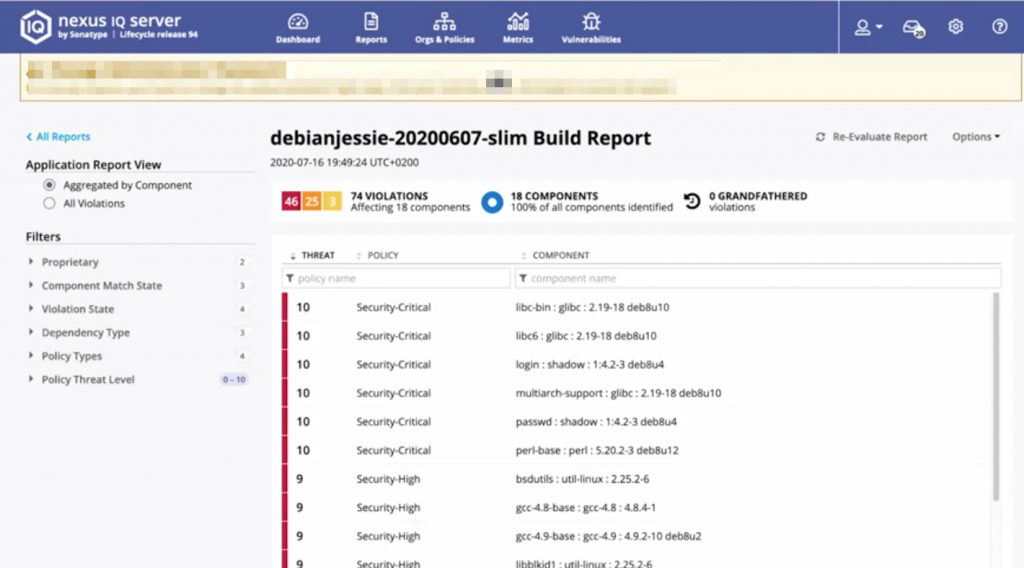 NeuVector Integrates with Sonatype Nexus Lifecycle to Secure Container..13 janeiro 2025
NeuVector Integrates with Sonatype Nexus Lifecycle to Secure Container..13 janeiro 2025 -
Keystone Dental Announces Market Launch of Nexus Connect, the First A.I. Enabled Intraoral Implant-Scan Analyzer for the Nexus iOS Full-Arch Solution13 janeiro 2025
você pode gostar
-
 Epic Wubbox My Singing Monsters Wallpapers - Wallpaper Cave13 janeiro 2025
Epic Wubbox My Singing Monsters Wallpapers - Wallpaper Cave13 janeiro 2025 -
SHAWTY's leading men 🔥 1M views in 1 day ackkkk!! Road to 2M babiiiies!!! You know where to find it ;) btw, sharing is caring so tap…13 janeiro 2025
-
 Download Batatinha frita 123 on PC with MEmu13 janeiro 2025
Download Batatinha frita 123 on PC with MEmu13 janeiro 2025 -
 How To Join All Star Tower Defense Discord Server 202313 janeiro 2025
How To Join All Star Tower Defense Discord Server 202313 janeiro 2025 -
 Botas Hombre Louis Vuitton13 janeiro 2025
Botas Hombre Louis Vuitton13 janeiro 2025 -
Hino Da Vitória13 janeiro 2025
-
 Witch, Goblin Slayer Wiki, Fandom13 janeiro 2025
Witch, Goblin Slayer Wiki, Fandom13 janeiro 2025 -
 Add and Setup Dank Member in Discord Server13 janeiro 2025
Add and Setup Dank Member in Discord Server13 janeiro 2025 -
 KartShop.com Castor Kit - - KartStore-USA13 janeiro 2025
KartShop.com Castor Kit - - KartStore-USA13 janeiro 2025 -
 Neon Play13 janeiro 2025
Neon Play13 janeiro 2025



