Malware analysis Suspicious activity
Por um escritor misterioso
Last updated 17 abril 2025
Malware Analysis - What is, Benefits & Types (Easily Explained)

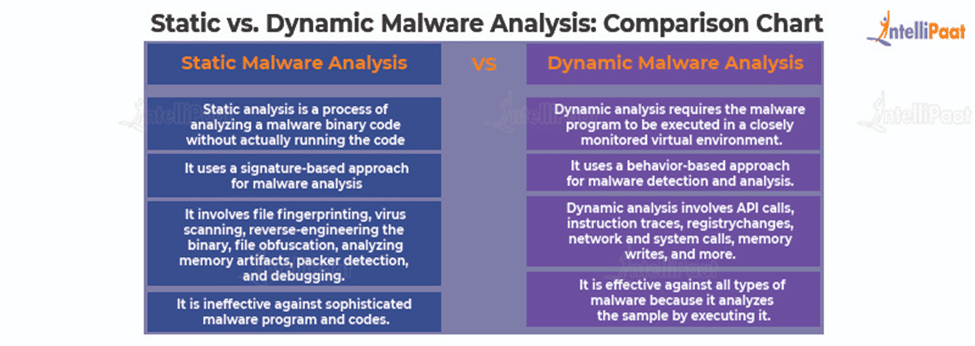
Malware Analysis 101 - Basic Static Analysis

Behavior-based malware analysis process as conducted by our

Fileless malware threats: Recent advances, analysis approach
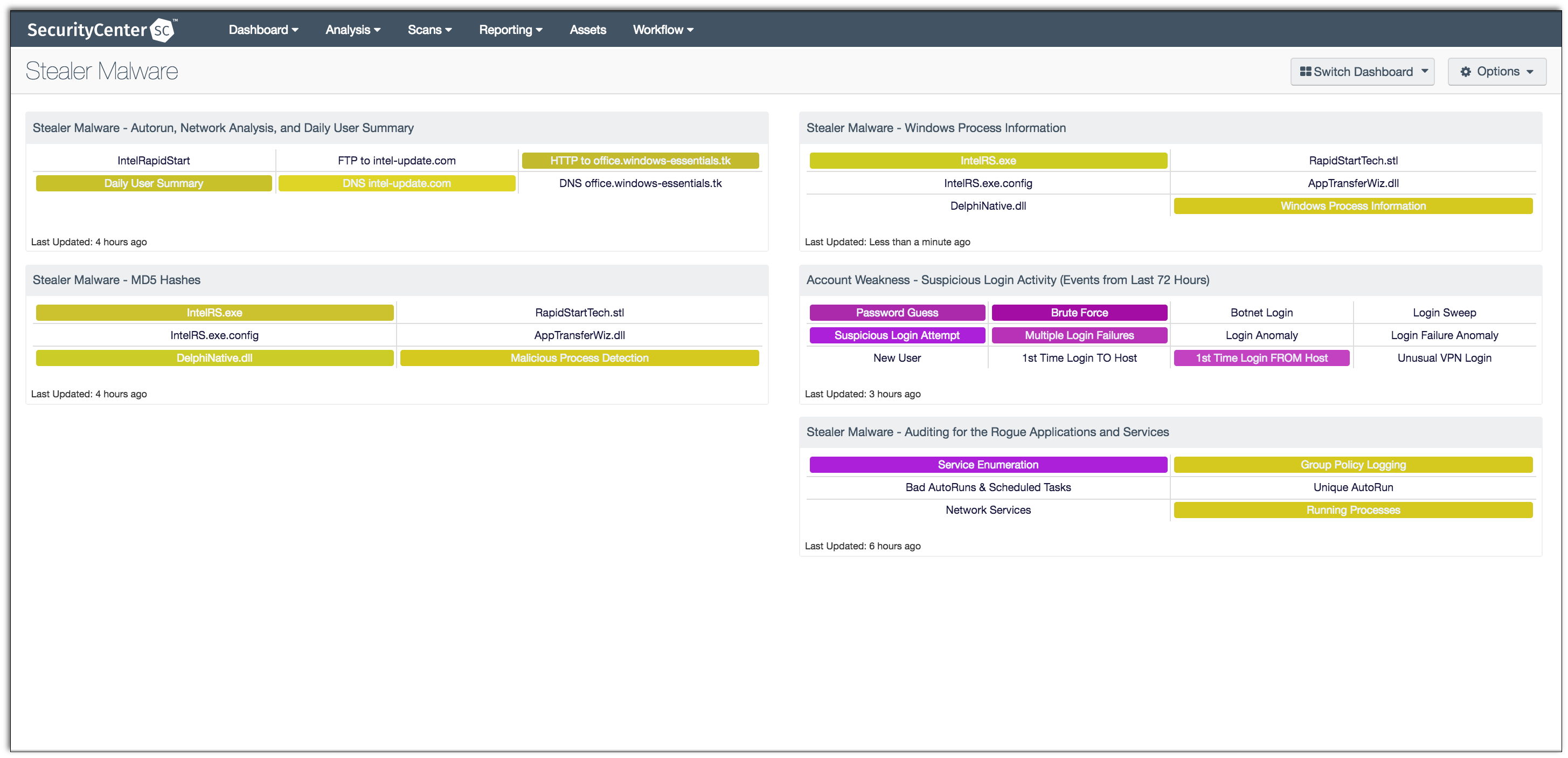
Stealer Malware - SC Dashboard

Microsoft 365 Alerting - Detect and React to Threats Instantly

The Top 20 Malware Analysis Tools for 2024
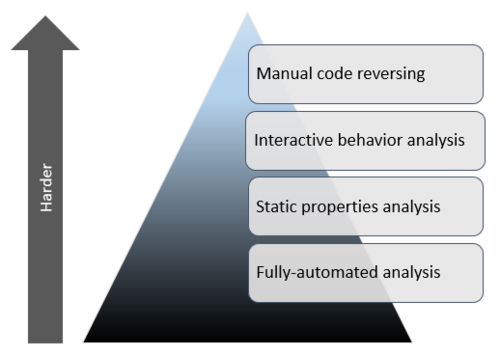
Mastering 4 Stages of Malware Analysis

Malware Incident Response Steps on Windows, and Determining If the
Malware analysis cable.exe Suspicious activity

What is Network Behavior Analysis (NBA)

Malware Analysis Framework v1.0

Malware Analysis Benefits Incident Response
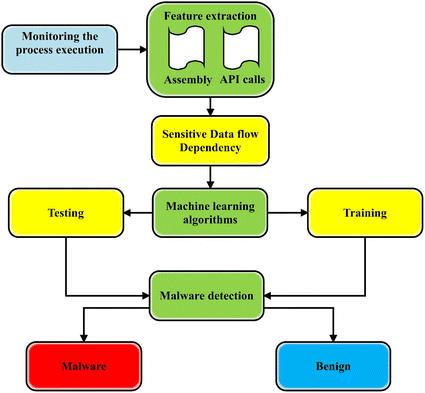
A state-of-the-art survey of malware detection approaches using
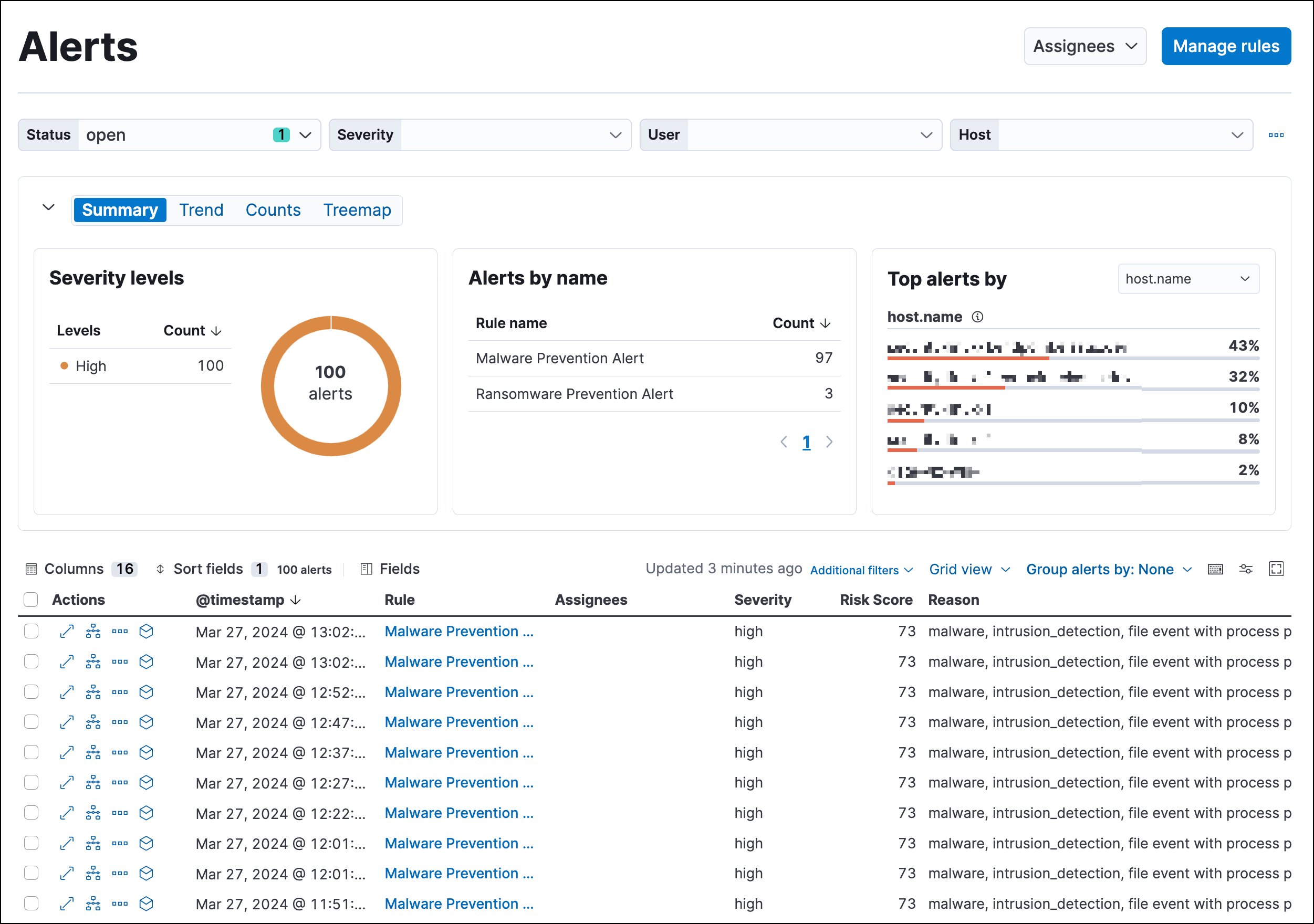
Detections and alerts, Elastic Security Solution [8.11]
Recomendado para você
-
ipchicken.com Traffic Analytics, Ranking Stats & Tech Stack17 abril 2025
-
 How to extract your outside IP address - What's My IP - IP Chicken - IP Monkey17 abril 2025
How to extract your outside IP address - What's My IP - IP Chicken - IP Monkey17 abril 2025 -
 8 Sites That Show Your IP Address –17 abril 2025
8 Sites That Show Your IP Address –17 abril 2025 -
174.218.138.250 is a publicly routable IP address is it not?17 abril 2025
-
![Zscaler- Source IP Anchoring [SIPA]](https://i.ytimg.com/vi/ylt74TZnS2Q/hq720.jpg?sqp=-oaymwE7CK4FEIIDSFryq4qpAy0IARUAAAAAGAElAADIQj0AgKJD8AEB-AH-CIAC0AWKAgwIABABGDwgEyh_MA8=&rs=AOn4CLAOEq5hhRYj-Kw0ehVImE5Q4ZxLDQ) Zscaler- Source IP Anchoring [SIPA]17 abril 2025
Zscaler- Source IP Anchoring [SIPA]17 abril 2025 -
 What Is A Port Scan? How To Prevent Port Scan Attacks?17 abril 2025
What Is A Port Scan? How To Prevent Port Scan Attacks?17 abril 2025 -
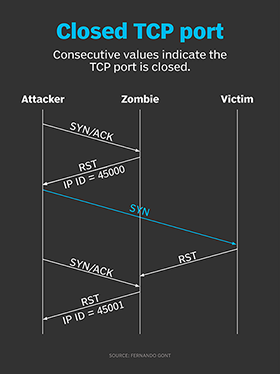 How hackers use idle scans in port scan attacks17 abril 2025
How hackers use idle scans in port scan attacks17 abril 2025 -
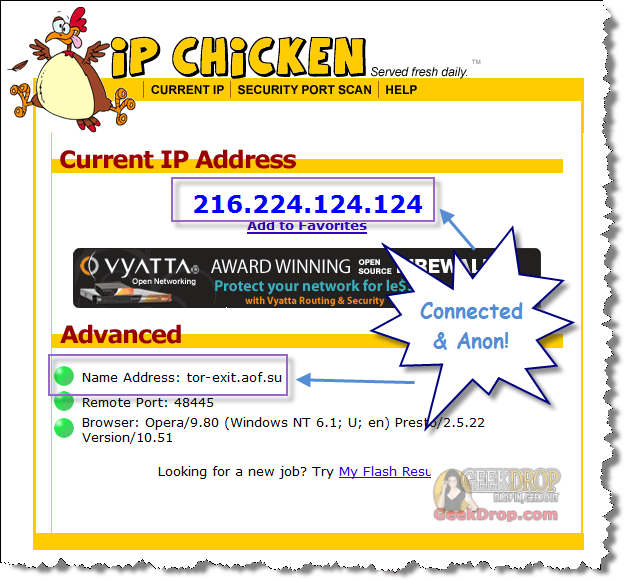 How To Use Tor With Opera Web Browser (With Polipo) For Beginners17 abril 2025
How To Use Tor With Opera Web Browser (With Polipo) For Beginners17 abril 2025 -
 10 Best Port Scanner Tools for Network Security - Geekflare17 abril 2025
10 Best Port Scanner Tools for Network Security - Geekflare17 abril 2025 -
 PPT - Safe Browsing PowerPoint Presentation, free download - ID:549326717 abril 2025
PPT - Safe Browsing PowerPoint Presentation, free download - ID:549326717 abril 2025
você pode gostar
-
 Devil May Cry 3 Both Guns Blazing17 abril 2025
Devil May Cry 3 Both Guns Blazing17 abril 2025 -
![Pre-order] Kaguya-sama: Love Is War Ultra Romantic – Nekotwo](https://nekotwo.com/cdn/shop/products/pre-order-kaguya-sama-love-is-war-ultra-romantic-kyunties-chika-fujiwara-seaside-ver-prize-figure-banprestoks-bp18877-649702_1024x1024.jpg?v=1657279751) Pre-order] Kaguya-sama: Love Is War Ultra Romantic – Nekotwo17 abril 2025
Pre-order] Kaguya-sama: Love Is War Ultra Romantic – Nekotwo17 abril 2025 -
 Steam Community :: Grand Theft Auto: San Andreas17 abril 2025
Steam Community :: Grand Theft Auto: San Andreas17 abril 2025 -
 UEFA Champions League Final 2022 - Full Match All Goals HD - eFootball PES Gameplay PC17 abril 2025
UEFA Champions League Final 2022 - Full Match All Goals HD - eFootball PES Gameplay PC17 abril 2025 -
 compare carro na web17 abril 2025
compare carro na web17 abril 2025 -
 Forest, Cat Game - The Cat Collector! Wiki17 abril 2025
Forest, Cat Game - The Cat Collector! Wiki17 abril 2025 -
 Star Wars: Andor - 2ª temporada adiada para 202517 abril 2025
Star Wars: Andor - 2ª temporada adiada para 202517 abril 2025 -
 You Are An Idiot, MUGEN Database17 abril 2025
You Are An Idiot, MUGEN Database17 abril 2025 -
 Pool Pro Online 3, jogo de sinuca Xbox Live para Windows Phone 8.1 - Windows Club17 abril 2025
Pool Pro Online 3, jogo de sinuca Xbox Live para Windows Phone 8.1 - Windows Club17 abril 2025 -
 enchanted sword shrine seed for 1.4.0.5 seed: 1 small corruption17 abril 2025
enchanted sword shrine seed for 1.4.0.5 seed: 1 small corruption17 abril 2025