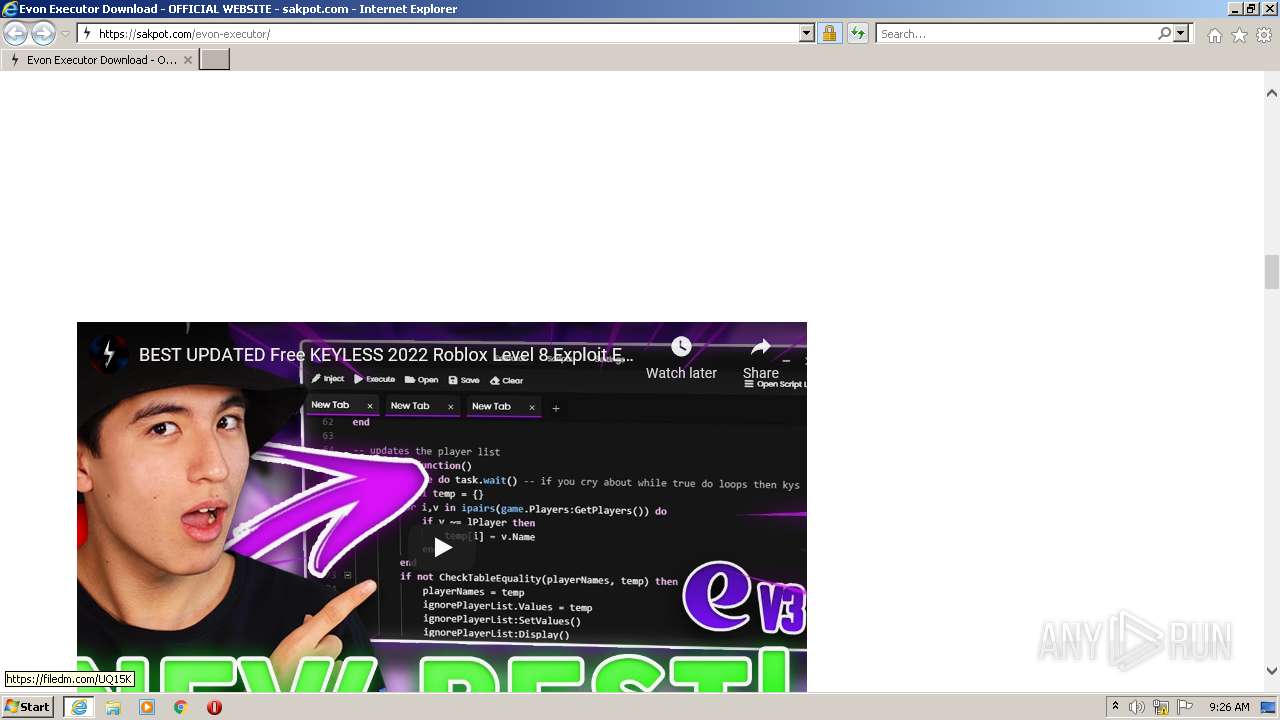
Malware analysis Malicious activity
Por um escritor misterioso
Last updated 18 abril 2025

Endpoint Detection and Response, Free - What is EDR Security?

Routers Roasting on an Open Firewall: the KV-botnet Investigation

PROUD-MAL: static analysis-based progressive framework for deep
Interactive Online Malware Sandbox
MetaDefender Cloud Advanced threat prevention and detection

Malware Analysis: Steps & Examples - CrowdStrike

Security Orchestration Use Case: Automating Malware Analysis

Cybersecurity Search Engine

Endpoint Detection and Response, Free - What is EDR Security?

How to Do Malware Analysis?

Brute Force Attacks: Password Protection
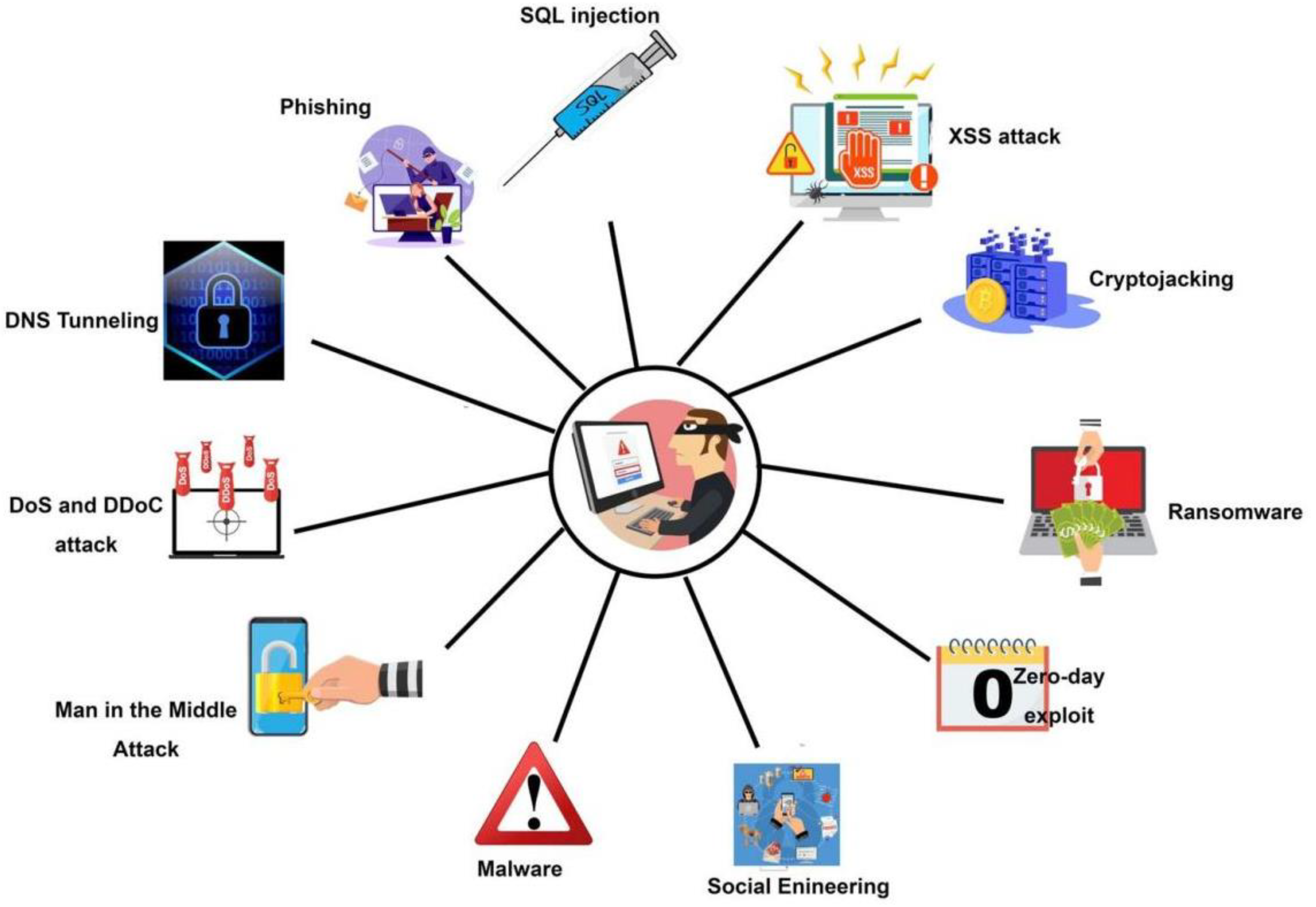
Symmetry, Free Full-Text

Playbook of the Week: Malware Investigation and Response - Palo
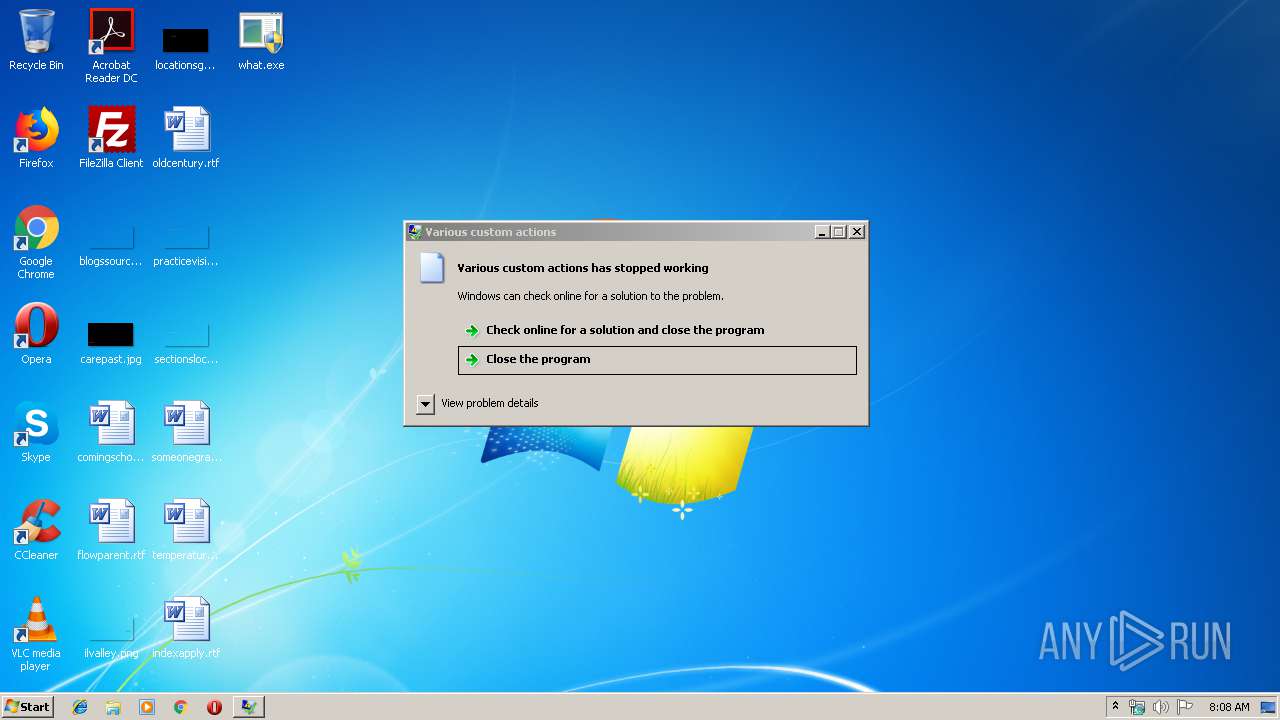
Malware analysis what.exe Malicious activity

What to Include in a Malware Analysis Report
Recomendado para você
-
 Electron x Script Menu, Electron x Executor Free18 abril 2025
Electron x Script Menu, Electron x Executor Free18 abril 2025 -
byfron-roblox · GitHub Topics · GitHub18 abril 2025
-
 Roblox Best Executor 2023, Roblox Best Cheat MENU FREE18 abril 2025
Roblox Best Executor 2023, Roblox Best Cheat MENU FREE18 abril 2025 -
 Delta Executor APK Download for Android Free18 abril 2025
Delta Executor APK Download for Android Free18 abril 2025 -
 Executor - Download18 abril 2025
Executor - Download18 abril 2025 -
![Hydrogen Executor v82 [v604]: Download #1 Android Roblox Exploit](https://hydrogenexecutor.com/wp-content/uploads/2023/05/download-button-1024x853.webp) Hydrogen Executor v82 [v604]: Download #1 Android Roblox Exploit18 abril 2025
Hydrogen Executor v82 [v604]: Download #1 Android Roblox Exploit18 abril 2025 -
 Make you a roblox ss executor by Gamerthefox108118 abril 2025
Make you a roblox ss executor by Gamerthefox108118 abril 2025 -
 why my roblox executor is not working?18 abril 2025
why my roblox executor is not working?18 abril 2025 -
 I need some help with all these random scripts - Scripting Support - Developer Forum18 abril 2025
I need some help with all these random scripts - Scripting Support - Developer Forum18 abril 2025 -
 Roblox x Electron Script Menu, Roblox x Electron Executor18 abril 2025
Roblox x Electron Script Menu, Roblox x Electron Executor18 abril 2025
você pode gostar
-
 FreeCell - Play Online & 100% Free18 abril 2025
FreeCell - Play Online & 100% Free18 abril 2025 -
 Assistir Perfect World – Episódio 83 Online18 abril 2025
Assistir Perfect World – Episódio 83 Online18 abril 2025 -
 ✧Alaric Saltzman; icons✧ Vampire diaries, The vampire diaries18 abril 2025
✧Alaric Saltzman; icons✧ Vampire diaries, The vampire diaries18 abril 2025 -
 Thor da fiel? Apresentador presenteia Chris Hemsworth com camisa18 abril 2025
Thor da fiel? Apresentador presenteia Chris Hemsworth com camisa18 abril 2025 -
 I made a Spidersona - Imgflip18 abril 2025
I made a Spidersona - Imgflip18 abril 2025 -
 Detroit: Become Human review: failure is more rewarding than success18 abril 2025
Detroit: Become Human review: failure is more rewarding than success18 abril 2025 -
 Crunchyroll Is Celebrating Ani-May with Merch, Partnerships, More18 abril 2025
Crunchyroll Is Celebrating Ani-May with Merch, Partnerships, More18 abril 2025 -
 Rap de Five Nights At Freddy's Security Breach Ruin DLC - Single18 abril 2025
Rap de Five Nights At Freddy's Security Breach Ruin DLC - Single18 abril 2025 -
 Drift Zone PS4 gameplay18 abril 2025
Drift Zone PS4 gameplay18 abril 2025 -
 Assistir Infinite Dendrogram Todos os Episódios Online - Animes BR18 abril 2025
Assistir Infinite Dendrogram Todos os Episódios Online - Animes BR18 abril 2025