Just-In-Time Privilege Elevation
Por um escritor misterioso
Last updated 18 abril 2025

Find out how Just-In-Time Privilege can prevent breach and protect your Active Directory.
Just-in-Time (JIT) Access Series Part 3: Zero Standing Privileges, Centrify, by Centrify Medium

Just-in-Time Administration for Secure Access Management
Just-In-Time Privilege Elevation: A least-privilege solution to protect your AD-connected business

Follow 'just-enough-access' principle by scoping resources during role elevation in Azure PIM

Automated Just-in-Time (JIT) for Least Privilege - Tenable Cloud Security

What is the principle of least privilege (POLP)?

What is Just-In-Time Access?
Linux Privilege Escalation Guide(Updated for 2023)

Zero Trust vs. Least-Privilege

What are Just-in-Time (JIT) Security Tokens?
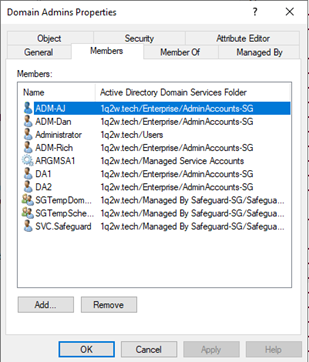
Just in Time Privilege Elevation in Active Directory - One Identity - Blogs - One Identity Community

Mastering Privileged Access Management (PAM): Essential Features Explained!

How Just-in-Time Privilege Elevation Prevents Data Breaches

Privileged Access Management (PAM)

What Is Just-in-Time Access? JIT Explained
Recomendado para você
-
 Data control: from management to accounting18 abril 2025
Data control: from management to accounting18 abril 2025 -
 Codelapa - Criação de Sites e E-commerce18 abril 2025
Codelapa - Criação de Sites e E-commerce18 abril 2025 -
 Contabilidade Online, Abrir Empresa Grátis18 abril 2025
Contabilidade Online, Abrir Empresa Grátis18 abril 2025 -
Contotal Contabilidade - Apps on Google Play18 abril 2025
-
 Accounting Software for Small Business 202218 abril 2025
Accounting Software for Small Business 202218 abril 2025 -
 Valuation: você sabe quanto vale sua empresa e no que se atentar? - Astec Contabilidade - Ribeirão Preto18 abril 2025
Valuation: você sabe quanto vale sua empresa e no que se atentar? - Astec Contabilidade - Ribeirão Preto18 abril 2025 -
 Ciclo da contabilidade de custos18 abril 2025
Ciclo da contabilidade de custos18 abril 2025 -
 Juruá Editora - Resumo de Contabilidade de Custos - Série Contabilidade Lúdica - Volume 2, Marlúcio Cândido e Ranylson de Sá Barreto Neto18 abril 2025
Juruá Editora - Resumo de Contabilidade de Custos - Série Contabilidade Lúdica - Volume 2, Marlúcio Cândido e Ranylson de Sá Barreto Neto18 abril 2025 -
 Control Gracias, Querido Dios, Por Ayudarme18 abril 2025
Control Gracias, Querido Dios, Por Ayudarme18 abril 2025 -
 Um conjunto de ilustrações vetoriais sobre um tópico de negócios comunicação online banking worktime control18 abril 2025
Um conjunto de ilustrações vetoriais sobre um tópico de negócios comunicação online banking worktime control18 abril 2025
você pode gostar
-
 Andrés Andy Rivas on X: Nothing to see here just practicing my gestures. 👀 #draw #drawing #practice #gestures #art #sketch #illustration #pose # poses #action / X18 abril 2025
Andrés Andy Rivas on X: Nothing to see here just practicing my gestures. 👀 #draw #drawing #practice #gestures #art #sketch #illustration #pose # poses #action / X18 abril 2025 -
Blackjack Rants: JoJo's Bizarre Adventure: Stone Ocean S05E38 Review: End of The World18 abril 2025
-
 Sonic Adventure 2 Battle - GameCube : Unknown: Video Games18 abril 2025
Sonic Adventure 2 Battle - GameCube : Unknown: Video Games18 abril 2025 -
 cutegirlsplayingchess18 abril 2025
cutegirlsplayingchess18 abril 2025 -
Pou fumante 😈🚬 (@pou.comendo.maconha)18 abril 2025
-
 Windows XP - Roblox18 abril 2025
Windows XP - Roblox18 abril 2025 -
Mondaiji Tachi ga Isekai kara kuru Sou Desu Yo? Light Novel18 abril 2025
-
 Pokémon GO Community Day: How To Get Yourself Every Shiny Eevee Evolution18 abril 2025
Pokémon GO Community Day: How To Get Yourself Every Shiny Eevee Evolution18 abril 2025 -
All Star Code - Org Chart, Teams, Culture & Jobs18 abril 2025
-
 19 filmes incríveis para assistir no cinema ainda em 201518 abril 2025
19 filmes incríveis para assistir no cinema ainda em 201518 abril 2025


