Infrastructure Hacking: WHOIS Protocol » Hacking Lethani
Por um escritor misterioso
Last updated 04 abril 2025
Did you know that the Secure Shell protocol, better known as SSH, is not as secure as its name suggests? In this post I show you different ways to attack this protocol. %

Infrastructure Hacking: WHOIS Protocol » Hacking Lethani
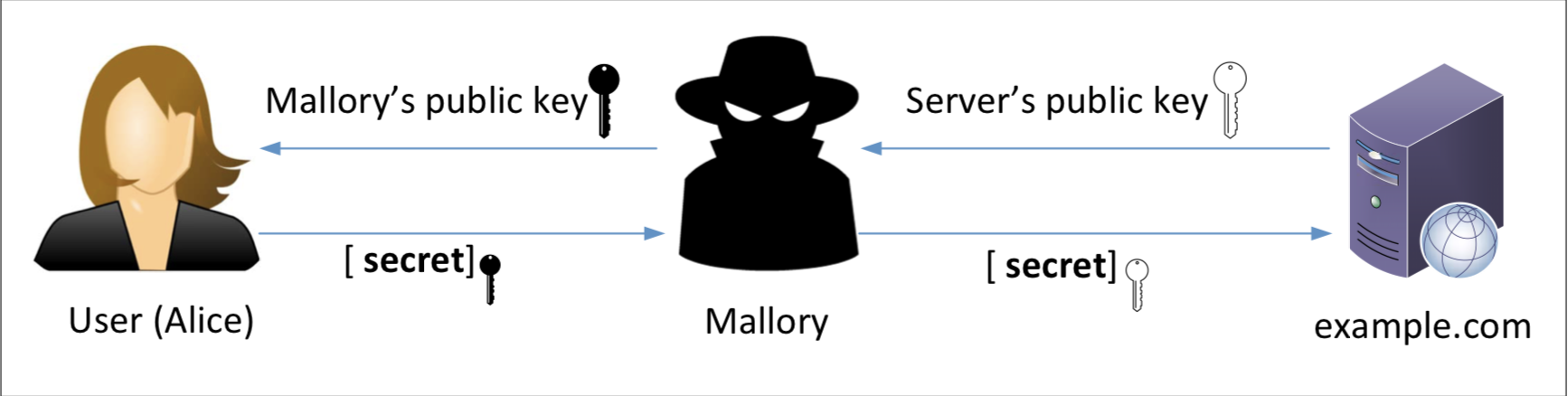
Network Security: Public Key Infrastructure Lab

Tips for Investigating Cybercrime Infrastructure

Ethical Hacking - Project C - QuickStart Cybersecurity Bootcamp

Tips for Investigating Cybercrime Infrastructure

Infrastructure Hacking: Telnet Protocol » Hacking Lethani

Hackers breached Greece's top-level domain registrar

Malicious Life Podcast: Wild West Hackin' Fest

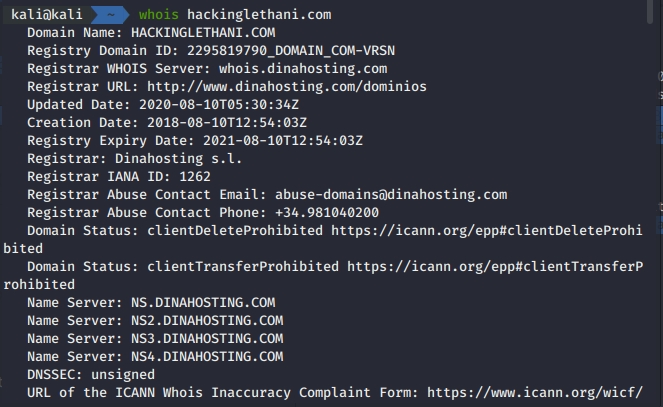
Infrastructure Hacking: WHOIS Protocol » Hacking Lethani
Ethical Hacking - How to start

DNC Hacks: How Spear Phishing Emails Were Used
Recomendado para você
-
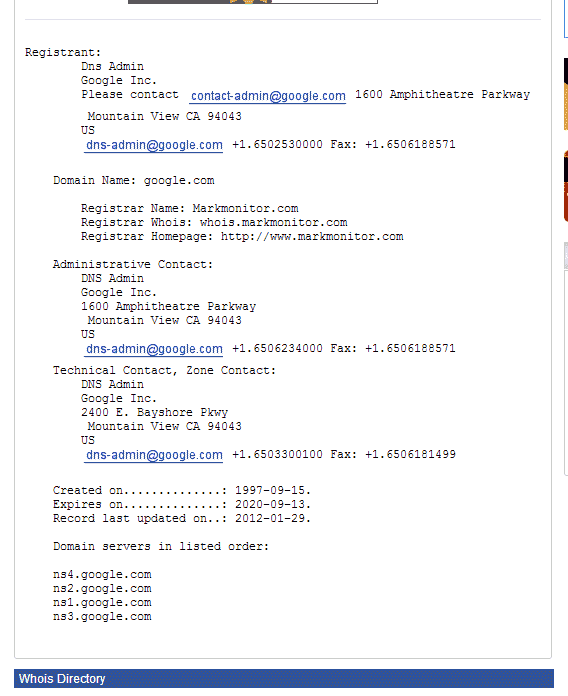 How to Look Up WHOIS Information for any Domain04 abril 2025
How to Look Up WHOIS Information for any Domain04 abril 2025 -
 Whois Visiting, Website Visitor Tracking Software04 abril 2025
Whois Visiting, Website Visitor Tracking Software04 abril 2025 -
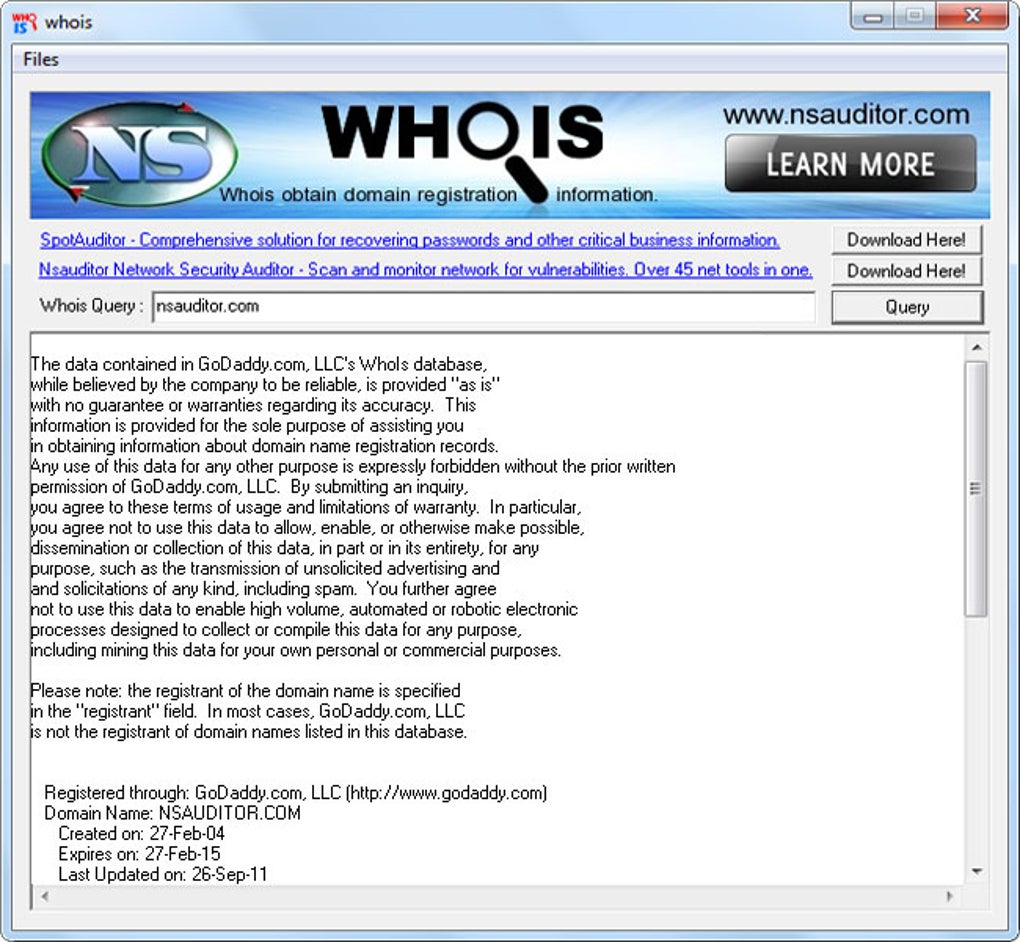 Whois - Download04 abril 2025
Whois - Download04 abril 2025 -
 WHOIS - Wikipedia04 abril 2025
WHOIS - Wikipedia04 abril 2025 -
Find your current registrar or domain WHOIS information04 abril 2025
-
 whois Command in Linux Explained04 abril 2025
whois Command in Linux Explained04 abril 2025 -
 Domain Privacy and WHOIS Lookup Explained04 abril 2025
Domain Privacy and WHOIS Lookup Explained04 abril 2025 -
Whois Icon04 abril 2025
-
 Who is WHOIS?04 abril 2025
Who is WHOIS?04 abril 2025 -
 Domain Status: 'ClientHold' or 'ServerHold', Help Center04 abril 2025
Domain Status: 'ClientHold' or 'ServerHold', Help Center04 abril 2025
você pode gostar
-
 Leone (Akame ga Kill!), Heroes Wiki04 abril 2025
Leone (Akame ga Kill!), Heroes Wiki04 abril 2025 -
 Wonder Creative Answer Search For Confused Idea Or Problem04 abril 2025
Wonder Creative Answer Search For Confused Idea Or Problem04 abril 2025 -
 Gaia, The 100 Wiki04 abril 2025
Gaia, The 100 Wiki04 abril 2025 -
Sonic Movie 3 Posters I Made in Picsart #104 abril 2025
-
 Undecember Runes List Guide04 abril 2025
Undecember Runes List Guide04 abril 2025 -
 Naruto Gaara Sand Village Patch Miniature Novelty Toys, : Toys & Games04 abril 2025
Naruto Gaara Sand Village Patch Miniature Novelty Toys, : Toys & Games04 abril 2025 -
 Fundo Arte Moda Retrato De Mulher Bonita Com Maquiagem Brilhante04 abril 2025
Fundo Arte Moda Retrato De Mulher Bonita Com Maquiagem Brilhante04 abril 2025 -
 Bola Basquete Spalding Graffiti Unissex - Verde/Amarela04 abril 2025
Bola Basquete Spalding Graffiti Unissex - Verde/Amarela04 abril 2025 -
/i.s3.glbimg.com/v1/AUTH_59edd422c0c84a879bd37670ae4f538a/internal_photos/bs/2017/c/Z/jRE2GCQ3CmcA7YpWHGuQ/campenha.jpg) Após vender 3 mil canetas para ir a campeonato de xadrez, garota04 abril 2025
Após vender 3 mil canetas para ir a campeonato de xadrez, garota04 abril 2025 -
Here's a condensed version of my anime hair shading tutorials04 abril 2025

