Subdomain Reputation: Detecting Malicious Subdomains of Public Apex Domains Subdomain Reputation: Detecting Malicious Subdomains of Public Apex Domains
Por um escritor misterioso
Last updated 26 dezembro 2024
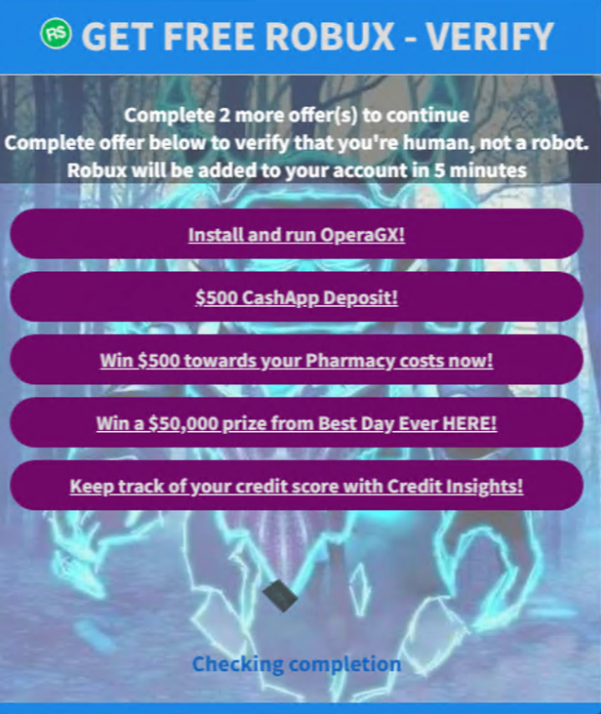
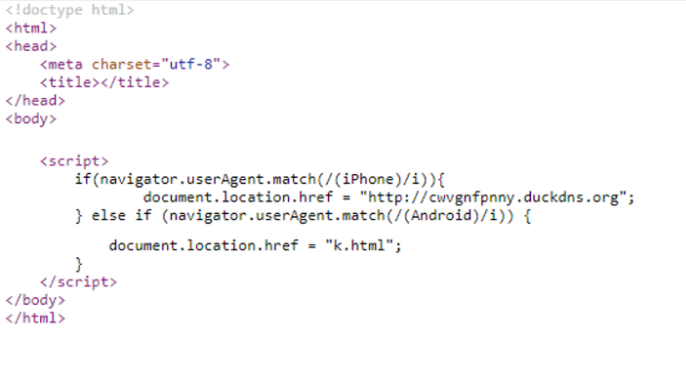
We cover two case studies of attacks hosted on malicious subdomains, including smishing and a scam Robux generator. We detail new methods in combating them.

Security Pills - Issue 37

Subdomain reconnaissance: enhancing a hacker's EASM - Labs Detectify
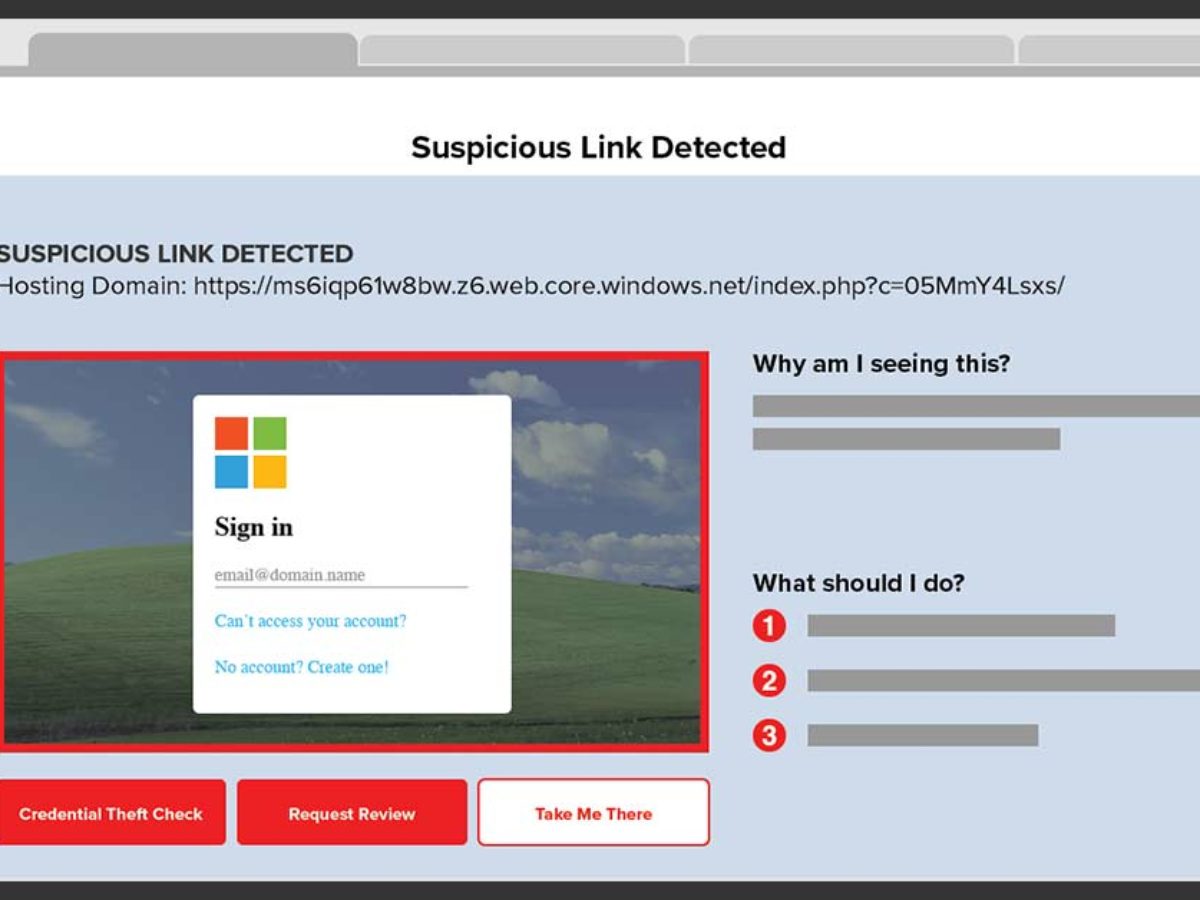
How to Protect Against Microsoft Subdomain Takeover - GreatHorn
Preventing Subdomain Takeover Attacks with Attack Surface Intelligence
Subdomain Reputation: Detecting Malicious Subdomains of Public Apex Domains Subdomain Reputation: Detecting Malicious Subdomains of Public Apex Domains

Compromised vs. Attack Domains: Building Machine Learning Models to Identify Malicious Hosting Types, by Mohamed Nabeel
Subdomain Reputation: Detecting Malicious Subdomains of Public Apex Domains Subdomain Reputation: Detecting Malicious Subdomains of Public Apex Domains
Subdomain Reputation: Detecting Malicious Subdomains of Public Apex Domains Subdomain Reputation: Detecting Malicious Subdomains of Public Apex Domains
Subdomain Reputation: Detecting Malicious Subdomains of Public Apex Domains Subdomain Reputation: Detecting Malicious Subdomains of Public Apex Domains

Subdomain Reputation: Detecting Malicious Subdomains of Public Apex Domains Subdomain Reputation: Detecting Malicious Subdomains of Public Apex Domains
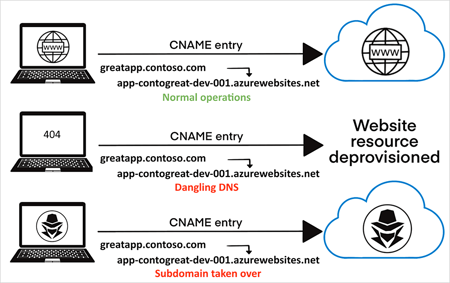
Preventing Subdomain Takeover Attacks with Attack Surface Intelligence
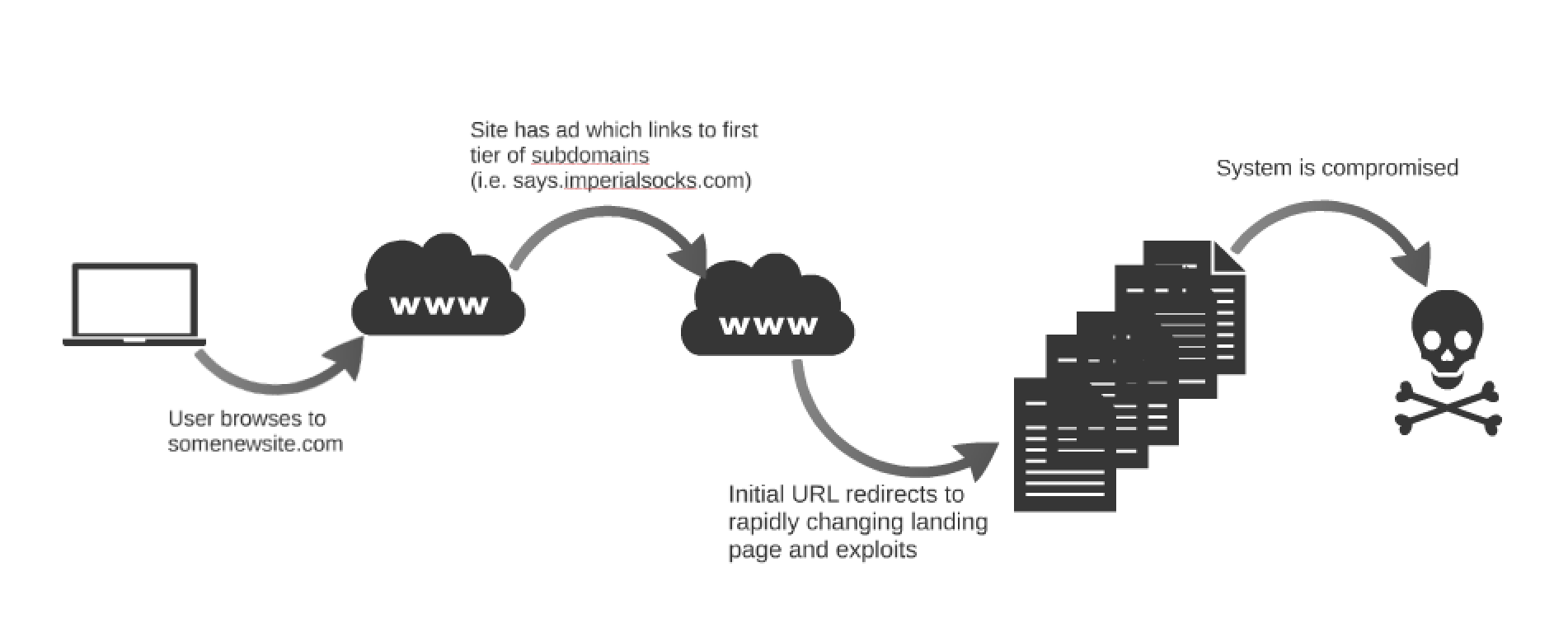
Threat Spotlight: Angler Lurking in the Domain Shadows - Cisco Blogs
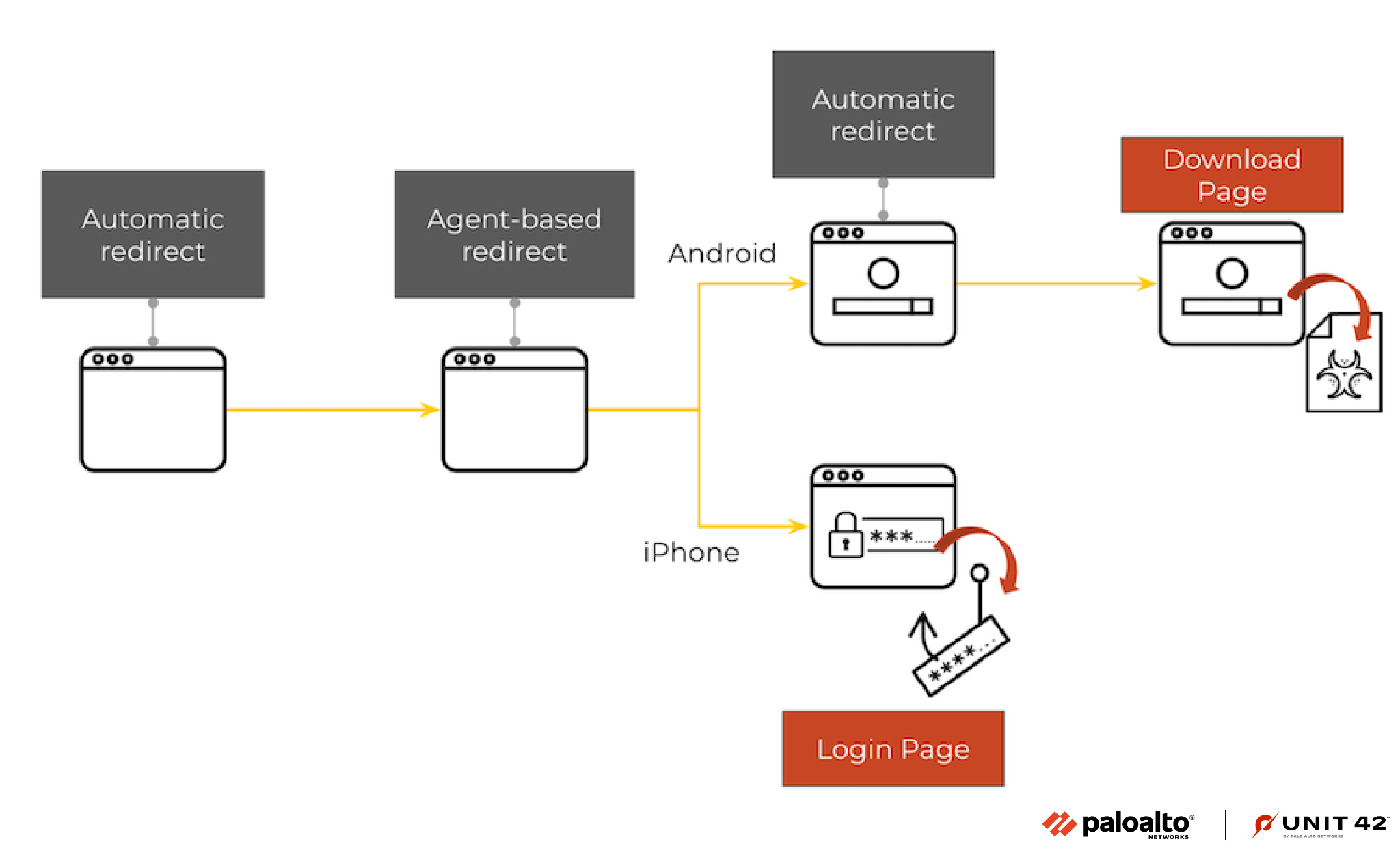
Subdomain Reputation: Detecting Malicious Subdomains of Public Apex Domains Subdomain Reputation: Detecting Malicious Subdomains of Public Apex Domains

Compromised vs. Attack Domains: Building Machine Learning Models to Identify Malicious Hosting Types, by Mohamed Nabeel
Recomendado para você
-
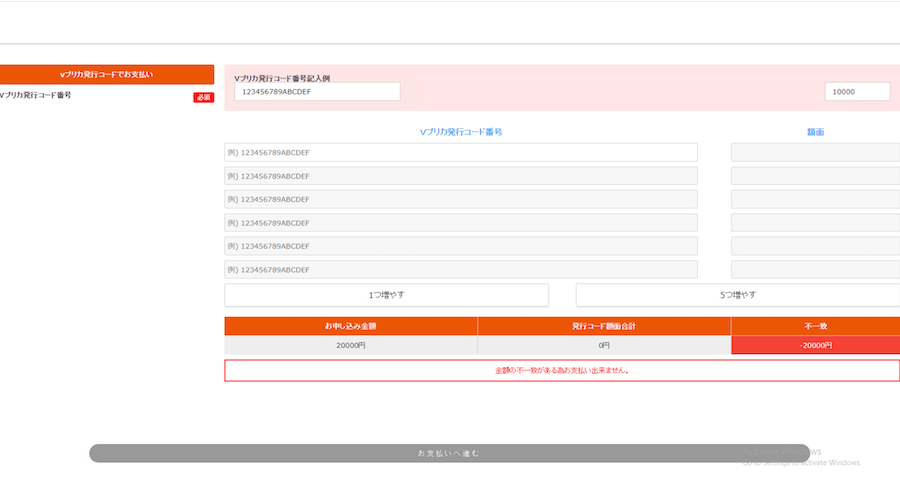
Roblox Robux Generator: No Human Verification, Make Ultimate Rubox Today 2023-202426 dezembro 2024
-
Robux Spin - Get ROBUX CALC - Apps on Google Play26 dezembro 2024
-
FREE Robux Generator: No Scam Verification ✮✧✮[Get 10000 Roblox Robux Codes]26 dezembro 2024
-
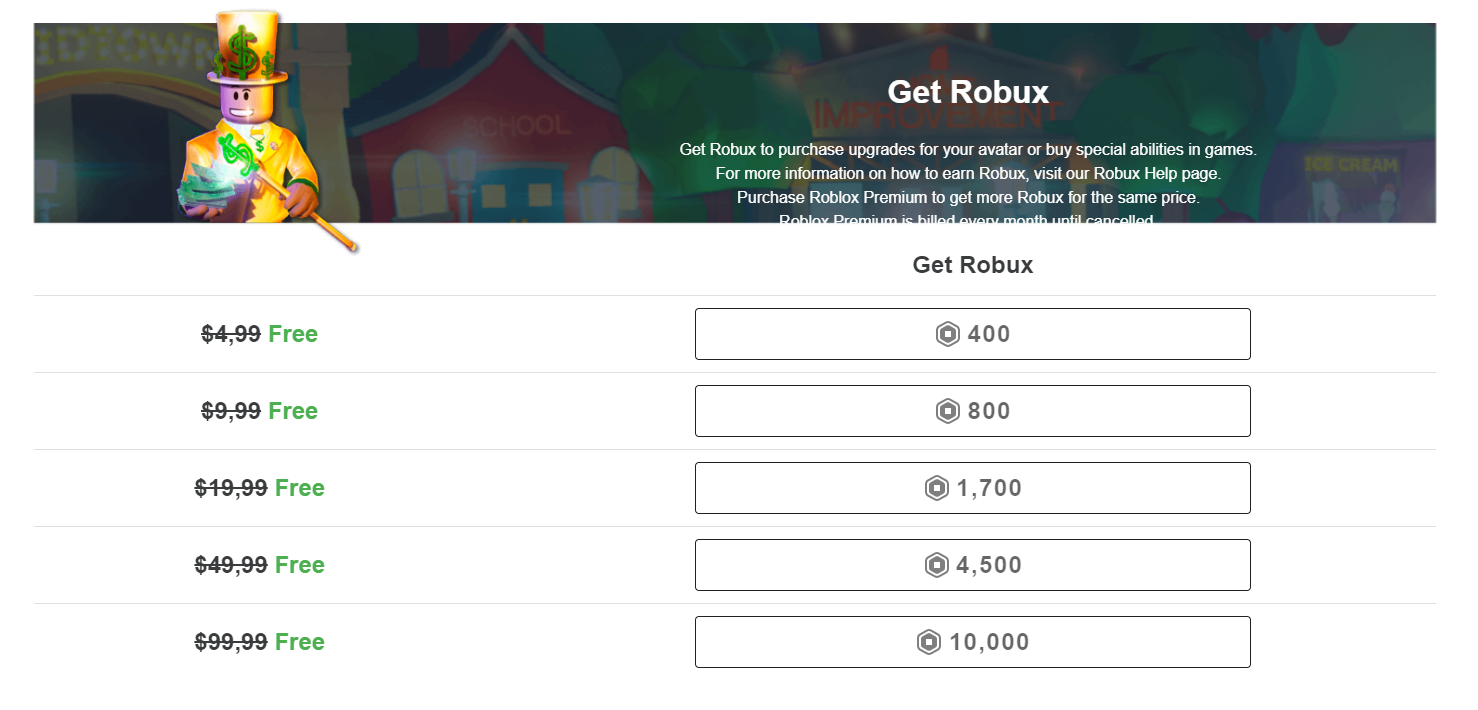 Do Free Robux Generators work?26 dezembro 2024
Do Free Robux Generators work?26 dezembro 2024 -
![Roblox $10 Gift Card - [Digital] + Exclusive Virtual Item](https://i5.walmartimages.com/seo/Roblox-100-Gift-Card-Digital-Exclusive-Virtual-Item_e10a3992-9d95-4fe0-9dcb-97e8c566837e.c23d36a937f4a9af755c530c3ec36104.jpeg) Roblox $10 Gift Card - [Digital] + Exclusive Virtual Item26 dezembro 2024
Roblox $10 Gift Card - [Digital] + Exclusive Virtual Item26 dezembro 2024 -
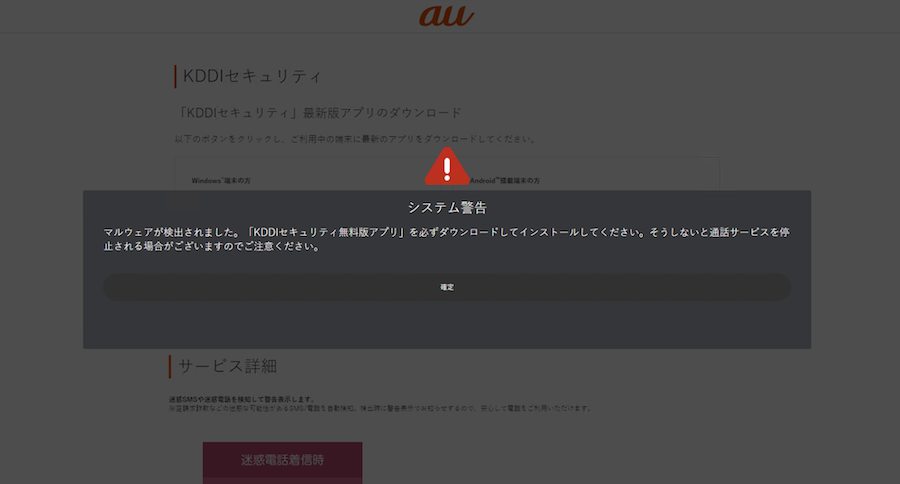
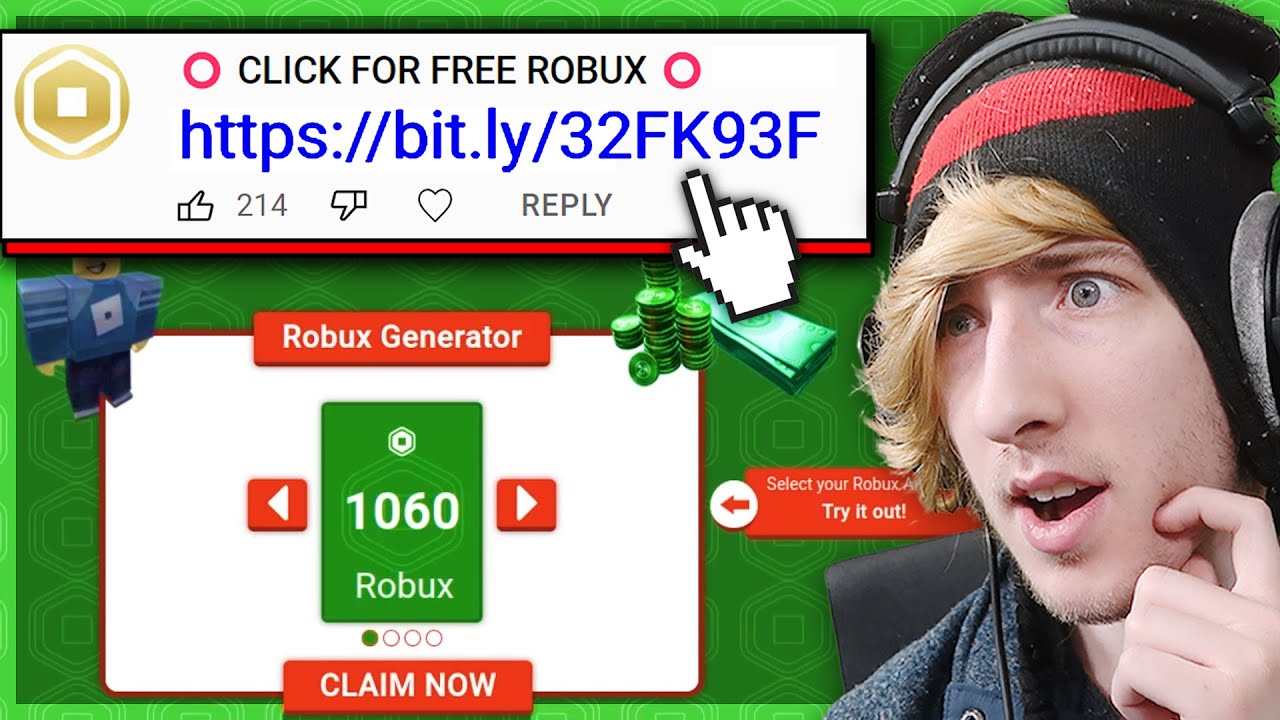 I Got HACKED by Clicking This Free Robux Link..26 dezembro 2024
I Got HACKED by Clicking This Free Robux Link..26 dezembro 2024 -
Are Robux generators scams? - Quora26 dezembro 2024
-
 Account Verification Documentation - Roblox Creator Hub26 dezembro 2024
Account Verification Documentation - Roblox Creator Hub26 dezembro 2024 -
 5 Letter Account Roblox26 dezembro 2024
5 Letter Account Roblox26 dezembro 2024 -
 Free Robux Generator No Human Verification Get 1,0000 Free RobloxRobux And Codes 202326 dezembro 2024
Free Robux Generator No Human Verification Get 1,0000 Free RobloxRobux And Codes 202326 dezembro 2024
você pode gostar
-
 A New PVP Roblox One Piece Game 🔥 (2022)26 dezembro 2024
A New PVP Roblox One Piece Game 🔥 (2022)26 dezembro 2024 -
 Skull and Bones delayed yet again, now launching March 202326 dezembro 2024
Skull and Bones delayed yet again, now launching March 202326 dezembro 2024 -
 Guia da Champions League 21/22 by pedrobuenno - Issuu26 dezembro 2024
Guia da Champions League 21/22 by pedrobuenno - Issuu26 dezembro 2024 -
 Call of Duty : Warzone 2.0 Live on Challenger26 dezembro 2024
Call of Duty : Warzone 2.0 Live on Challenger26 dezembro 2024 -
 Dragon Ball' é rejeitado na Espanha por desrespeitar código de valores26 dezembro 2024
Dragon Ball' é rejeitado na Espanha por desrespeitar código de valores26 dezembro 2024 -
 Disney Is Spending More on Theme Parks Than It Did on Pixar, Marvel and Lucasfilm Combined - The New York Times26 dezembro 2024
Disney Is Spending More on Theme Parks Than It Did on Pixar, Marvel and Lucasfilm Combined - The New York Times26 dezembro 2024 -
 Emma, Yakusoku no Neverland Wiki26 dezembro 2024
Emma, Yakusoku no Neverland Wiki26 dezembro 2024 -
 ✓Apk de la primera version de subway surfers ( actualizado26 dezembro 2024
✓Apk de la primera version de subway surfers ( actualizado26 dezembro 2024 -
 Sweatshirt com capuz King e Queen conjunto namorados - Personalizei26 dezembro 2024
Sweatshirt com capuz King e Queen conjunto namorados - Personalizei26 dezembro 2024 -
 Mortal Kombat 1 has been announced for September 1926 dezembro 2024
Mortal Kombat 1 has been announced for September 1926 dezembro 2024

![FREE Robux Generator: No Scam Verification ✮✧✮[Get 10000 Roblox Robux Codes]](https://media.licdn.com/dms/image/D4D12AQEXUEIwqcHJQQ/article-cover_image-shrink_600_2000/0/1701316346607?e=2147483647&v=beta&t=1Pej40o0FBLBTAXYgAZ7An0VHGS1q05mrDAcWfZ5cek)