Algorithms, Free Full-Text
Por um escritor misterioso
Last updated 15 abril 2025
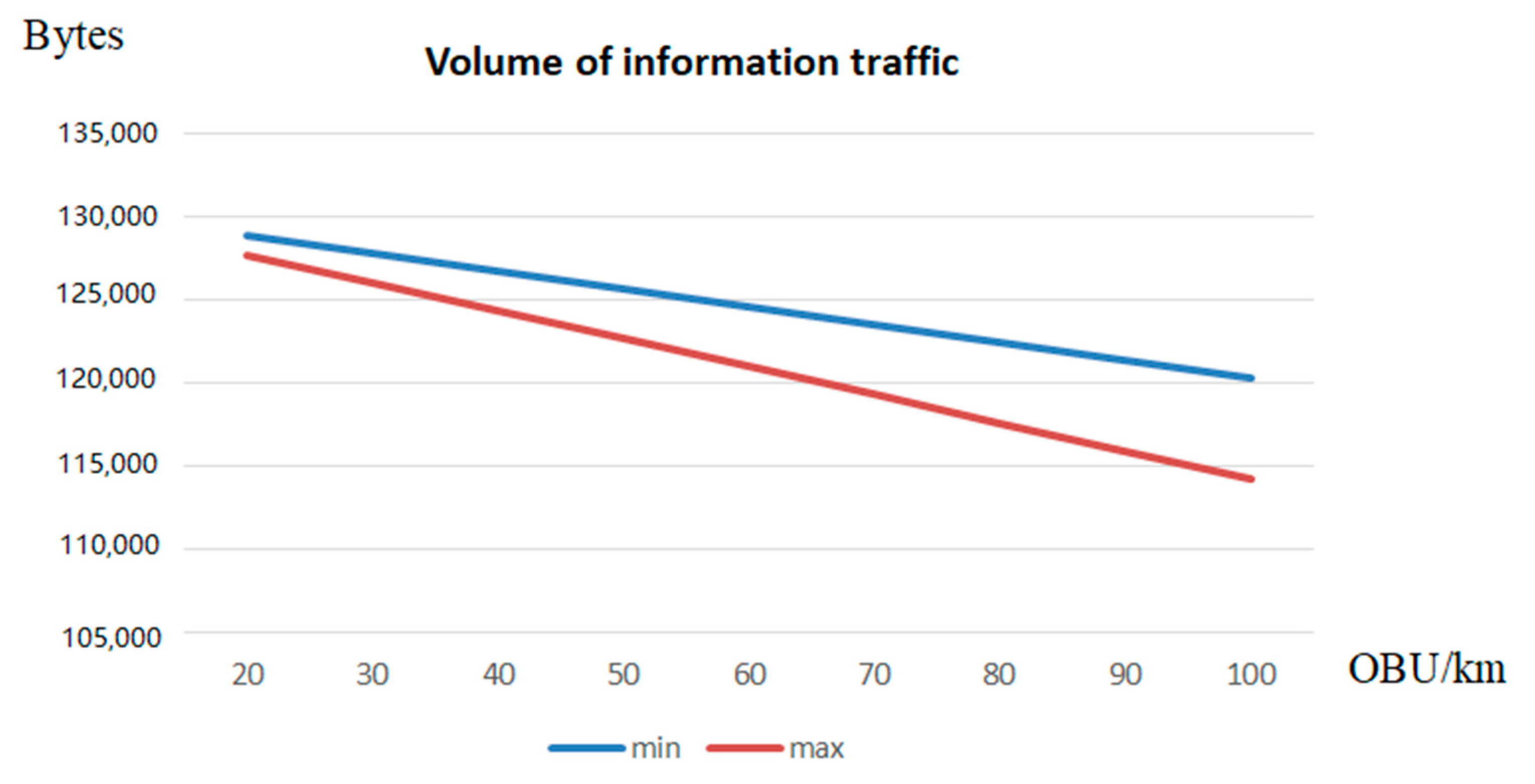
Authentication protocols are expanding their application scope in wireless information systems, among which are low-orbit satellite communication systems (LOSCS) for the OneWeb space Internet, automatic object identification systems using RFID, the Internet of Things, intelligent transportation systems (ITS), Vehicular Ad Hoc Network (VANET). This is due to the fact that authentication protocols effectively resist a number of attacks on wireless data transmission channels in these systems. The main disadvantage of most authentication protocols is the use of symmetric and asymmetric encryption systems to ensure high cryptographic strength. As a result, there is a problem in delivering keys to the sides of the prover and the verifier. At the same time, compromising of keys will lead to a decrease in the level of protection of the transmitted data. Zero-knowledge authentication protocols (ZKAP) are able to eliminate this disadvantage. However, most of these protocols use multiple rounds to authenticate the prover. Therefore, ZKAP, which has minimal time costs, is developed in the article. A scheme for adapting protocol parameters has been developed in this protocol to increase its efficiency. Reductions in the level of confidentiality allow us to reduce the time spent on the execution of the authentication protocol. This increases the volume of information traffic. At the same time, an increase in the confidentiality of the protocol entails an increase in the time needed for authentication of the prover, which reduces the volume of information traffic. The FPGA Artix-7 xc7a12ticsg325-1L was used to estimate the time spent implementing the adaptive ZKAP protocol. Testing was performed for 32- and 64-bit adaptive authentication protocols.

Top 10 Machine Learning Algorithms for Beginners

Screening for extranodal extension in HPV-associated oropharyngeal
Psycho Tropical Berlin Rym - Colaboratory

Free Algorithms Book

15 Best Data Structures and Algorithms Courses (Free & Paid
Genetic Algorithms Software Testing - Colaboratory
Validation of automatic wear-time detection algorithms in a free

Large Scale Text Search Algorithm with Tries: A Tutorial

Beyond the Worst-Case Analysis of Algorithms
Recomendado para você
-
![All Roblox Project New World Codes (December 2023) [Haze Piece]](https://twinfinite.net/wp-content/uploads/2022/12/Roblox-Anime-Dimensions.jpg) All Roblox Project New World Codes (December 2023) [Haze Piece]15 abril 2025
All Roblox Project New World Codes (December 2023) [Haze Piece]15 abril 2025 -
 Project New World Codes (December 2023): Free Spins & Gems15 abril 2025
Project New World Codes (December 2023): Free Spins & Gems15 abril 2025 -
 Project New World Codes – Gamezebo15 abril 2025
Project New World Codes – Gamezebo15 abril 2025 -
 FUTURE CODES!! *NEW* ROBLOX PROJECT NEW WORLD CODES 2023! (135K CODE)15 abril 2025
FUTURE CODES!! *NEW* ROBLOX PROJECT NEW WORLD CODES 2023! (135K CODE)15 abril 2025 -
 Roblox - Códigos para o Project New World (julho 2023) - Critical Hits15 abril 2025
Roblox - Códigos para o Project New World (julho 2023) - Critical Hits15 abril 2025 -
 Why the West Rules―for Now: The Patterns of by Morris, Ian15 abril 2025
Why the West Rules―for Now: The Patterns of by Morris, Ian15 abril 2025 -
Slave voyages: the transatlantic trade in enslaved Africans15 abril 2025
-
 Jen Easterly🛡️ (@CISAJen) / X15 abril 2025
Jen Easterly🛡️ (@CISAJen) / X15 abril 2025 -
 Green Infrastructure Codes and Ordinances15 abril 2025
Green Infrastructure Codes and Ordinances15 abril 2025 -
 News/Media Archive - Skender15 abril 2025
News/Media Archive - Skender15 abril 2025
você pode gostar
-
 maquiar boneca app|Pesquisa do TikTok15 abril 2025
maquiar boneca app|Pesquisa do TikTok15 abril 2025 -
 Jacyara Carvalho (jcampos5832) - Profile15 abril 2025
Jacyara Carvalho (jcampos5832) - Profile15 abril 2025 -
 Volume 11, The Promised Neverland Wiki15 abril 2025
Volume 11, The Promised Neverland Wiki15 abril 2025 -
 Call of Duty: Vanguard ocupará entre 36 GB e 61 GB no PC; confira15 abril 2025
Call of Duty: Vanguard ocupará entre 36 GB e 61 GB no PC; confira15 abril 2025 -
 Honzuki no Gekokujou ~Shisho ni Naru Tame ni wa Shudan wo Erandeiraremasen~ Dai 2-bu 「Hon no Tamenara Miko ni Naru!」 manga - Mangago15 abril 2025
Honzuki no Gekokujou ~Shisho ni Naru Tame ni wa Shudan wo Erandeiraremasen~ Dai 2-bu 「Hon no Tamenara Miko ni Naru!」 manga - Mangago15 abril 2025 -
 ESTREIAS: John Wick ou a arte de matar para não morrer15 abril 2025
ESTREIAS: John Wick ou a arte de matar para não morrer15 abril 2025 -
 Oscars 2021 winners: Nomadland, Frances McDormand, Daniel Kaluuya15 abril 2025
Oscars 2021 winners: Nomadland, Frances McDormand, Daniel Kaluuya15 abril 2025 -
 Watch Mysteria Friends Episode 10 Online - The Pair's Promise15 abril 2025
Watch Mysteria Friends Episode 10 Online - The Pair's Promise15 abril 2025 -
 Borderlands 3: How to open the Vaulthalla Secret Room15 abril 2025
Borderlands 3: How to open the Vaulthalla Secret Room15 abril 2025 -
 The Rake Teaser Trailer15 abril 2025
The Rake Teaser Trailer15 abril 2025
