Abusing Exceptions for Code Execution, Part 1
Por um escritor misterioso
Last updated 10 abril 2025

A common offensive technique used by operators and malware developers alike has been to execute malicious code at runtime to avoid static detection. Often, methods of achieving runtime execution have focused on placing arbitrary code into executable memory that can then be executed. In this article, we will explore a
A common offensive technique used by operators and malware developers alike has been to execute malicious code at runtime to avoid static detection. Often, methods of achieving runtime execution have focused on placing arbitrary code into executable memory that can then be executed. In this article, we will explore a new approach to executing runtime code that does not rely on finding executable regions of memory, but instead relies on abusing existing trusted memory to execute arbitrary code.
A common offensive technique used by operators and malware developers alike has been to execute malicious code at runtime to avoid static detection. Often, methods of achieving runtime execution have focused on placing arbitrary code into executable memory that can then be executed. In this article, we will explore a new approach to executing runtime code that does not rely on finding executable regions of memory, but instead relies on abusing existing trusted memory to execute arbitrary code.

GitHub Actions Security Best Practices [cheat sheet included]

InnoGear Boom Arm Microphone Mic Stand for Blue Yeti HyperX QuadCast SoloCast Snowball Fifine Shure SM7B and other Mic, Medium : Musical Instruments

Loophole Abuse - TV Tropes

How Dare They Peep into My Private Life?”: Children's Rights Violations by Governments that Endorsed Online Learning During the Covid-19 Pandemic
Learn how to add Input Validation to a REST API with NestJS and Prisma
CVE-2022-28219: Unauthenticated XXE to RCE and Domain Compromise in ManageEngine ADAudit Plus –
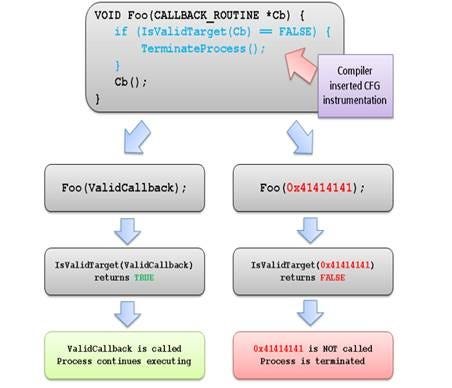
Exploitation Protections From Old To Bleeding Edge pt 1, by Edward Amaral Toledano, stolabs
Abusing Exceptions for Code Execution, Part 1
User Account Control – Overview and Exploitation

Detecting anomalous Vectored Exception Handlers on Windows, NCC Group Research Blog
Recomendado para você
-
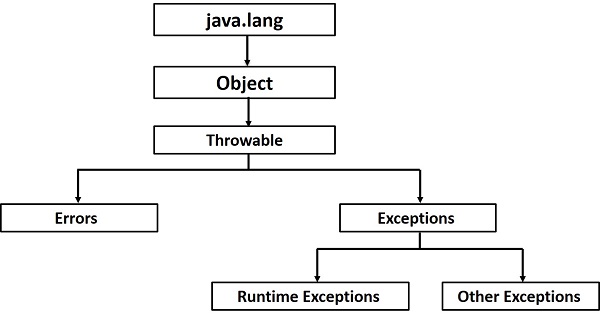 Java - Exceptions10 abril 2025
Java - Exceptions10 abril 2025 -
Types of Exceptions in Java10 abril 2025
-
 Dress Expectations / Dress Code Exceptions10 abril 2025
Dress Expectations / Dress Code Exceptions10 abril 2025 -
 Java - Custom Light Exceptions - Advlatam10 abril 2025
Java - Custom Light Exceptions - Advlatam10 abril 2025 -
 Different types of Exceptions in Salesforce - Apex Hours10 abril 2025
Different types of Exceptions in Salesforce - Apex Hours10 abril 2025 -
 What is Delivery Exceptions and How to Respond It10 abril 2025
What is Delivery Exceptions and How to Respond It10 abril 2025 -
![Exceptions API, Elastic Security Solution [8.11]](https://www.elastic.co/guide/en/security/current/images/exceptions-logic.png) Exceptions API, Elastic Security Solution [8.11]10 abril 2025
Exceptions API, Elastic Security Solution [8.11]10 abril 2025 -
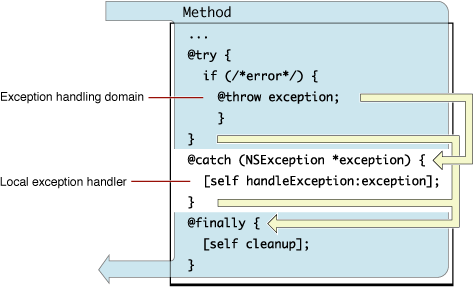 Handling Exceptions10 abril 2025
Handling Exceptions10 abril 2025 -
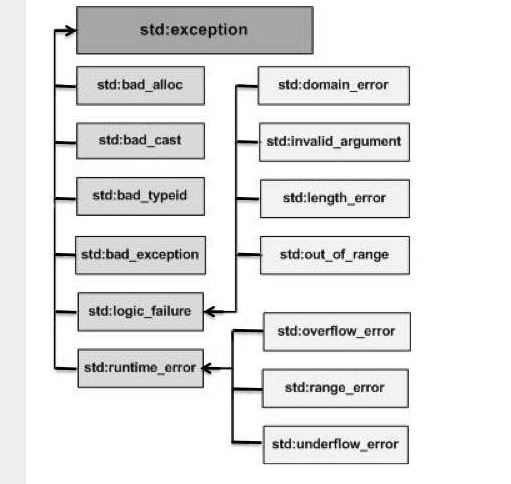 C++ Exception Handling. Back to, by Tech Notes10 abril 2025
C++ Exception Handling. Back to, by Tech Notes10 abril 2025 -
 Exceptions Stock Photos, Royalty Free Exceptions Images10 abril 2025
Exceptions Stock Photos, Royalty Free Exceptions Images10 abril 2025
você pode gostar
-
Quiz de Conhecimentos Gerais №7 - Parte 7. #educaquiz10 abril 2025
-
 CHAPTER 8 SKEWERS Diagram 225 - Black wins a Rook in 2 moves.10 abril 2025
CHAPTER 8 SKEWERS Diagram 225 - Black wins a Rook in 2 moves.10 abril 2025 -
 How to Play Vampire: The Masquerade - Part 3-2: Actual Play Episode 2 - RPGBOT.Quickstart S3E7110 abril 2025
How to Play Vampire: The Masquerade - Part 3-2: Actual Play Episode 2 - RPGBOT.Quickstart S3E7110 abril 2025 -
:quality(90)/cloudfront-us-east-1.images.arcpublishing.com/elcomercio/BRTSIWYCYVEJROKDT6N5OJYVFA.jpg) Vikings, casting de Alex Høgh Andersen: el papel que casi interpreta en lugar de Ivar el Deshuesado, Ivar the Boneless, Vikingos, Series de Netflix nnda nnlt, FAMA10 abril 2025
Vikings, casting de Alex Høgh Andersen: el papel que casi interpreta en lugar de Ivar el Deshuesado, Ivar the Boneless, Vikingos, Series de Netflix nnda nnlt, FAMA10 abril 2025 -
 Top 10 doors figure fanart ideas and inspiration10 abril 2025
Top 10 doors figure fanart ideas and inspiration10 abril 2025 -
 Show us Ant-Man trailer: Twitter users react as Marvel drops Werewolf by Night first teaser and confirms air date10 abril 2025
Show us Ant-Man trailer: Twitter users react as Marvel drops Werewolf by Night first teaser and confirms air date10 abril 2025 -
 Opera anuncia concorrente a Roblox que paga criadores - Canaltech10 abril 2025
Opera anuncia concorrente a Roblox que paga criadores - Canaltech10 abril 2025 -
 lyrics at your disposal — Coldplay- Paradise (request)10 abril 2025
lyrics at your disposal — Coldplay- Paradise (request)10 abril 2025 -
![Minecraft PSP - [LC Mod] - /Downloads - View Download](http://i.imgur.com/iqJctgl.png) Minecraft PSP - [LC Mod] - /Downloads - View Download10 abril 2025
Minecraft PSP - [LC Mod] - /Downloads - View Download10 abril 2025 -
 Santorini Nightlife Guide: 15 Best Tavernas, Bars & Clubs in Santorini - Sofia Adventures10 abril 2025
Santorini Nightlife Guide: 15 Best Tavernas, Bars & Clubs in Santorini - Sofia Adventures10 abril 2025

